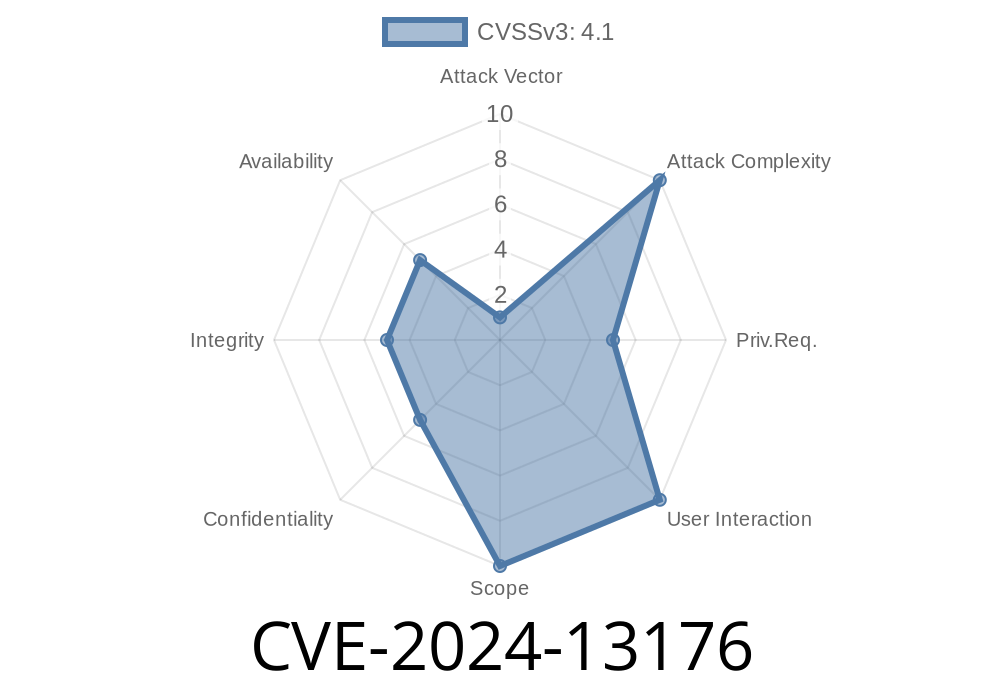
A new vulnerability—CVE-2024-13176—has popped up, targeting the ECDSA (Elliptic Curve Digital Signature Algorithm) cryptography used for secure digital signatures. This issue is a timing side-channel attack that can potentially leak a private key when signing messages. While the risk is relatively low due to the technical requirements, it’s a good demonstration of how even tiny, hard-to-detect differences in code execution time can have real security impact.
Issue Summary
ECDSA is a popular choice for digital signatures in cryptographic systems like TLS, SSH, and cryptocurrencies. CVE-2024-13176 reveals that a subtle timing signal leaks from the ECDSA signing process, especially when using the NIST P-521 elliptic curve.
The problem:
- In the signing operation, if the "inverted nonce"’s top word is zero, the operation runs ~300 nanoseconds faster.
- An attacker with access to accurate timing (local user or very fast network) could potentially measure this timing and, after collecting enough timing data, deduce bits of the private key.
Severity:
ECDSA Signing (Simplified)
When creating a signature, the ECDSA algorithm makes use of a random, secret number called a "nonce." For every signature, the code computes an inverse of this nonce (k_inv). Some elliptic curves, due to their number size, mean that occasionally, the "top word" (the most significant bits) of k_inv is zero. When that happens, some operations finish faster.
Here’s a simplified example to help you see where the problem may lie
def ecdsa_sign(private_key, message):
k = get_random_nonce()
k_inv = inverse_mod(k, n)
if top_word(k_inv) == :
# This branch is faster due to internal math operation shortcuts
do_fast_math()
else:
do_normal_math()
r = (G * k).x % n
s = (k_inv * (hash(message) + r * private_key)) % n
return (r, s)
If an attacker can remotely measure if do_fast_math() was called (by noticing if the signing was 300ns faster), it leaks info about k_inv, and, bit by bit, the private key.
Requirements
- The attacker can send arbitrary messages for signatures (a common scenario for authentication tokens or some APIs)
Attack Steps
1. Send many signing requests: The attacker sends many signing requests to the vulnerable server or service.
Measure timing: Record the time taken for each signing response.
3. Statistical analysis: Analyze the timing data; group signature timings to separate out when k_inv's top word is zero.
4. Key extraction: Use published cryptanalysis methods (see [References](#references)) to recover the private key bit by bit after collecting enough signatures.
Real-World Limitations
- Real world networks are noisy. It's hard to measure 300ns differences unless you are on a gigabit LAN or locally on the same computer.
How To Fix
Patches should make all code paths take the same amount of time, no matter the inputs. Library maintainers (e.g., OpenSSL, libgcrypt) now ensure ECDSA math is "constant time" everywhere.
apt-get update && apt-get upgrade
`
- Switch to curves that are not affected if possible.
- Restrict who can send signature requests to your service.
---
## Links & References
- Original Advisory:
https://nvd.nist.gov/vuln/detail/CVE-2024-13176
- libgcrypt Advisory:
https://lists.gnupg.org/pipermail/gnupg-announce/2024q2/000478.html
- Technical writeup:
https://soatok.blog/2024/04/12/cve-2024-13176-ecdsa-timing-side-channel/
- Constant-Time Cryptography:
https://crypto.stanford.edu/~dabo/pubs/papers/ssl-timing.pdf
- OpenSSL advisory:
https://www.openssl.org/news/secadv/20240417.txt
---
## TL;DR
- CVE-2024-13176 is a timing attack on ECDSA (mainly P-521 curve), letting attackers with precise timing steal private keys.
- Risk is low except for shared-server setups or very fast private networks.
- Patch your cryptographic libraries! Constant-time code fixes the leak.
Share this post with colleagues—timing still matters!
Timeline
Published on: 01/20/2025 14:15:26 UTC
Last modified on: 01/27/2025 21:15:11 UTC