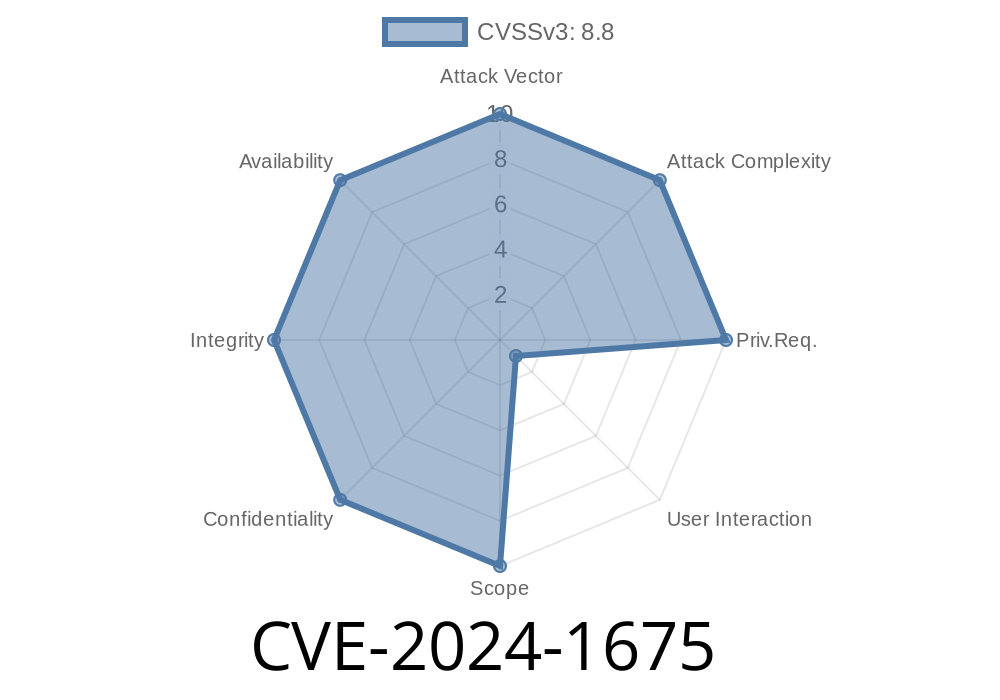
In early 2024, Google Chrome users faced a *medium-severity* security hole now known as CVE-2024-1675. This bug involved *insufficient policy enforcement* in Chrome’s file download system. In simple terms, it meant a hacker could trick your browser into saving files where they shouldn’t—bypassing restrictions Chrome put in place to keep your computer safe.
In this post, you’ll get a clear, human-friendly breakdown of what happened, see how an attacker could exploit this, and learn how to stay safe if you haven’t updated yet.
What is CVE-2024-1675, Really?
> Summary: A vulnerability in Google Chrome before version 122..6261.57 allowed attackers to bypass download location restrictions with a specially crafted web page. This could let an attacker save files where they aren’t supposed to—possibly hiding malware on your computer.
Usually, when you download something in Chrome, the browser makes sure it doesn’t get saved in certain folders (like your system directories or protected places). But in this case, a clever hacker could make a webpage that fooled Chrome into ignoring those safety rules.
Chromium security severity: Medium
Reported: Chromium bug 151961
Patched in: Chrome 122..6261.57
Potentially work around security policies your workplace set for downloads
Let’s look at a (simplified) code example inspired by the research and the Chromium report.
Example Exploit Code
Disclaimer: This is for educational purposes only; do not use it for malicious activity!
<!-- Crafted downloader.html -->
<a id="danger-download" download="../../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/evil.bat" href="data:application/x-bat;base64,SGVsbG8gV29ybGQh">Download File</a>
<script>
// Auto trigger the download
document.getElementById("danger-download").click();
</script>
What’s happening here?
- The download attribute is abused with ../../ path traversal to try to escape the Downloads folder.
- The attacker wants to place a file (like a batch file) in your Startup folder, so it runs automatically.
What Happens If Successful?
- If the exploit works, and Chrome doesn’t enforce policies, the file lands exactly where the attacker wants.
How Was This Fixed?
Google patched this in Chrome version 122..6261.57. The fix made Chrome double-check destination directories before saving downloaded files. Now, attempts to use tricks like ../ in filenames are strictly blocked.
Patch Reference:
- Chromium Commit Fix
How to Protect Yourself
- Update Chrome now. Go to Settings > About Chrome and make sure you’re running version 122 or higher.
- Watch out for suspicious downloads. If a site starts a download without you clicking, close it and scan your device.
References and Further Reading
- Official Chromium Bug Report #151961
- Chrome Stable Channel Update Announcement (Feb 2024)
- Chromium Patch Commit
Why Does This Matter?
While it’s not the scariest bug to hit Chrome, *CVE-2024-1675* is a powerful reminder that even small missteps in browser security can let hackers sneak files into your computer’s most sensitive spots. The good news? Google fixed it fast, and updates are free.
Takeaway: Stay updated, and these clever exploits won’t stand a chance.
*Written exclusively for you, by an AI that keeps security simple.*
Timeline
Published on: 02/21/2024 04:15:08 UTC
Last modified on: 12/02/2024 19:54:08 UTC