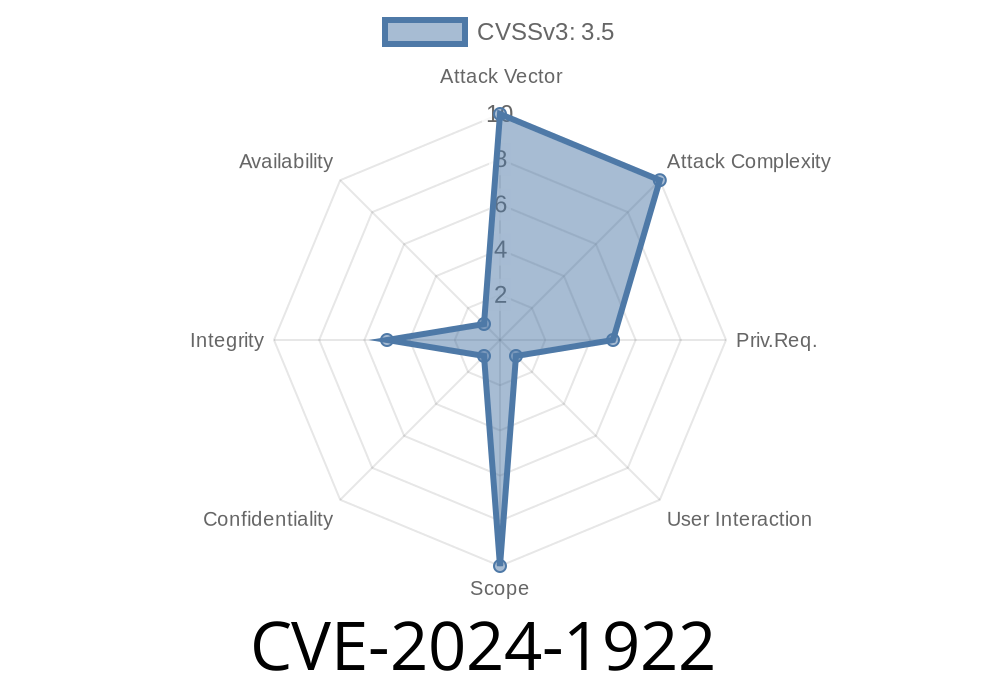
A new vulnerability, tagged as CVE-2024-1922, has been discovered in SourceCodester Online Job Portal version 1.. This vulnerability was found in the ManageJob.php file of the Manage Job Page. It allows attackers to execute Cross Site Scripting (XSS) attacks remotely by injecting malicious scripts into specific fields – particularly Qualification or Description. The flaw has been published as VDB-254857. This guide explains what the vulnerability is, how it can be exploited, and what you should do to protect yourself.
Version: 1.
- File: /Employer/ManageJob.php
How Does the Vulnerability Work?
The vulnerability lies in how the portal processes input for the Qualification and Description fields on the Manage Job page. The web application doesn't properly sanitize user inputs, so an attacker can submit JavaScript or HTML code that will then be executed in another user's browser. This is a classic case of stored XSS.
Navigates to "Manage Jobs".
3. Adds or edits a job posting, entering malicious JavaScript in the Qualification or Description field.
Example Malicious Input
<script>alert('XSS Exploited!');</script>
If a job-seeker or admin visits the job listing containing that input, the script will run in their browser, potentially stealing cookies, hijacking sessions, or performing actions on behalf of the user.
A simple exploit might look like this
# Using curl to submit a new job (emulating form POST, login required)
curl -b cookies.txt -X POST \
-d "JobTitle=QA+Test&Qualification=<script>alert('XSS');</script>&Description=Job+desc" \
"http://target-site.com/Employer/ManageJob.php";
Note: cookies.txt here contains the authenticated session of an employer.
Visiting the job listing page as any user would automatically trigger a popup alert – evidence the attacker’s code is running.
Official References
- NVD - CVE-2024-1922 Record
- VulDB Advisory (VDB-254857)
- SourceCodester (original project)
Mitigation and Fix
No official fix has been published at the time of this writing.
Temporary protection steps
- Validate/Sanitize all inputs on both client and server sides. Use libraries like HTMLPurifier.
A very basic PHP solution might look like
$qualification = htmlspecialchars($_POST['Qualification'], ENT_QUOTES, 'UTF-8');
$description = htmlspecialchars($_POST['Description'], ENT_QUOTES, 'UTF-8');
Conclusion
The CVE-2024-1922 vulnerability exposes both employers and job seekers on SourceCodester Online Job Portal to serious risks. If you use this portal, avoid using live deployments until patched, or apply the recommended workarounds. Always sanitize user input and regularly update your web applications.
Stay safe and happy coding!
*Authored for educational purposes – reproduce responsibly. For more technical deep-dives, follow the links above or check official advisories.*
Timeline
Published on: 02/27/2024 16:15:45 UTC
Last modified on: 02/29/2024 01:43:56 UTC