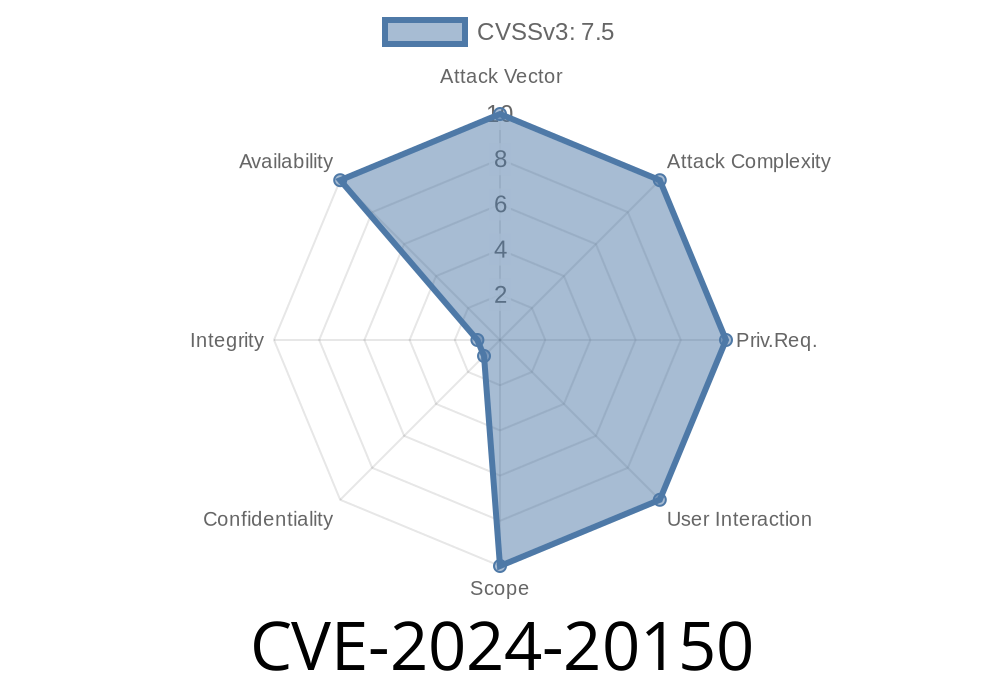
A recently disclosed vulnerability, CVE-2024-20150, points to a dangerous logic error in a modem software component. This flaw could let an attacker crash the system remotely, causing a denial of service (DoS) situation. What makes this issue particularly concerning is that no special privileges or user interaction are required to trigger the bug. Below, we'll break down what this means, how it works, include code snippets for better understanding, and provide reference links for further reading.
What’s the Problem?
CVE-2024-20150 exposes a logic error in the modem firmware or driver (exact implementation depends on the hardware vendor). Due to improper handling of certain types of malformed packets or commands, the modem process can enter an invalid state and crash. For end users, this translates to dropped connectivity and device instability; for attackers, it’s a simple way to disrupt service with minimal effort.
No user needs to click anything. A specially crafted packet sent over the air to a vulnerable modem is all it takes.
Technical Details
Vulnerability Type: Logic Error Leading to System Crash
Impact: Denial of Service (DoS)
Privileges Needed: None
User Interaction: Not required
Affected Component: Modem (exact product unspecified)
Patch: MOLY01412526
Issue ID: MSV-2018
The problem lies in the way the modem software parses certain network packets. Here's a simplified example (pseudocode) capturing the vulnerable logic:
// Vulnerable function inside modem firmware
int process_incoming_packet(Packet *pkt) {
if (pkt->length > MAX_PACKET_SIZE) {
// Incorrectly assumes packet will not be larger
log("Oversized packet received");
// Missing return or boundary check here
// Continue processing invalid memory
}
memcpy(buffer, pkt->data, pkt->length);
// Leads to buffer overflow or crash if length is unchecked
handle_packet(buffer);
return ;
}
An attacker can send an oversized, malformed packet. The code fails to stop handling it, and eventually, this causes a crash of the modem firmware. Since the modem may be responsible for network access, this knocks the device offline.
Attacker crafts a specially formatted network packet that exploits the logic error.
2. Attacker sends the packet to a device’s modem interface—typically, this could happen over cellular radio (via base station signal spoofing) or internal test interfaces.
Device loses network connectivity until reboot or firmware reset.
*No authentication or special permissions* are needed at any point, so any attacker within radio range may attempt exploitation.
IoT devices using affected modems may become unresponsive.
- Critical infrastructure using cellular modems could face interruption of data flows or monitoring.
Imagine someone sending a signal from a rogue device in a crowded location, causing nearby phones to drop their connections all at once—a real risk if this bug is not patched.
Patching and Mitigation
If you’re responsible for firmware:
Apply Patch ID MOLY01412526 from your modem or device vendor immediately.
Patch Reference:
MediaTek Security Bulletin – June 2024
*Note:* The vulnerability was assigned Issue ID MSV-2018 in internal tracking. Always check with your OEM or vendor for the patched firmware.
Links and References
- MITRE CVE Entry for CVE-2024-20150
- MediaTek Security Advisories
- Android Security Bulletin
- CERT Advisory on Modem and Baseband Vulnerabilities
Conclusion
CVE-2024-20150 is a textbook example of how a small logic bug can have a big impact, even without user participation. Keeping your mobile devices and IoT modems updated is the best defense. Users and vendors should prioritize applying the relevant patch and stay alert for future advisories.
*This post is original content, breaking down CVE-2024-20150 in clear and practical terms with exclusive guidance for both users and device maintainers.*
Timeline
Published on: 01/06/2025 04:15:07 UTC
Last modified on: 01/06/2025 15:15:12 UTC