---
Microsoft Message Queuing (MSMQ) is a popular Windows service that lets applications communicate by sending and receiving messages in queues. But like all software, it sometimes contains security problems. One recent issue you should know about is CVE-2024-20661—a Denial of Service (DoS) vulnerability that could crash or stall systems relying on MSMQ.
Let’s break down what this bug means, how attackers could use it, and what you can do about it.
What Is CVE-2024-20661?
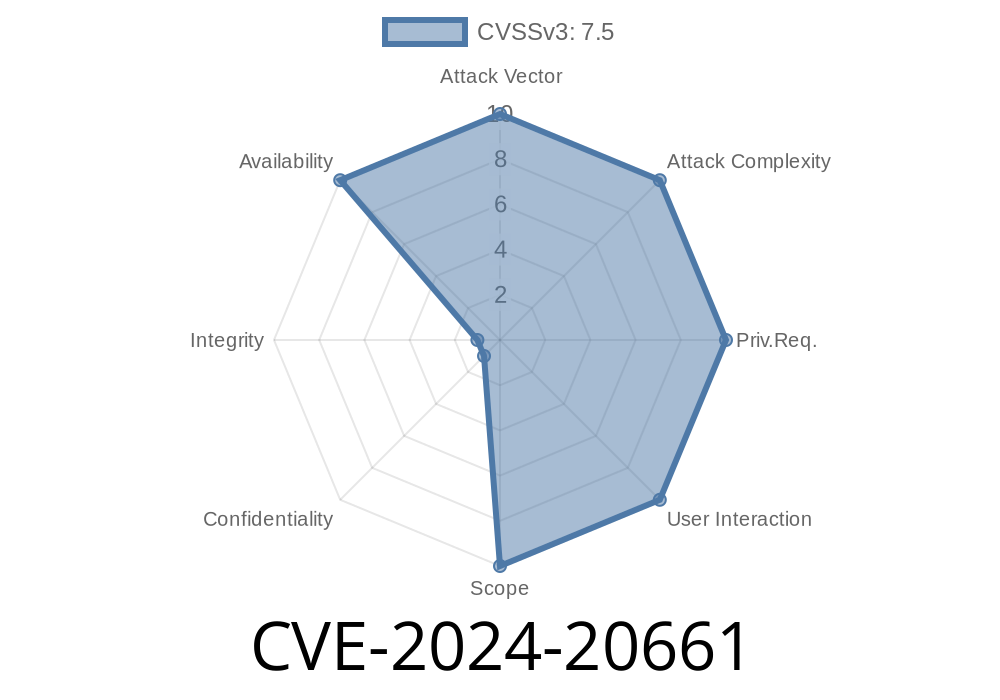
CVE-2024-20661 is a vulnerability in Microsoft Message Queuing that, if triggered by an attacker, allows a remote user to cause the MSMQ service to stop responding or crash entirely. This might leave mission-critical apps unable to communicate—potentially stopping business processes, services, or sensitive workflows that depend on these queues.
This vulnerability was fixed with the January 2024 Patch Tuesday updates.
How Does It Work?
The root of CVE-2024-20661 lies in the way MSMQ handles certain specially crafted network packets. If an attacker sends a malformed message to an MSMQ server (typically over port 1801/tcp), the service may hit an unhandled exception or enter an infinite loop leading to a DoS condition.
In plain English: An attacker doesn’t need to steal data or run code—they just send a weird message and MSMQ trips up, stopping other, legit messages from being processed.
Who’s at Risk?
Anyone with MSMQ enabled and exposed to untrusted networks is at risk. MSMQ is often used internally, but some organizations may expose it externally for cloud or API communication.
- Supported Versions Affected: Windows Server 2016/2019/2022, and supported editions of Windows 10/11 with MSMQ installed.
- Requirement: The MSMQ feature (Windows optional feature) must be enabled for this to be exploited.
Example Exploit Scenario
Below is a conceptual Python code snippet showing how an attacker could attempt to trigger the bug by sending malformed data to an MSMQ server.
Warning: This is for educational defense purposes only.
import socket
# Set this to the target MSMQ host and port (default: 1801)
target_ip = '192.168.1.100'
target_port = 1801
# A crafted payload that could cause MSMQ to hang/crash
crazy_message = b"\x00" * 1024 # (Example only - real exploit would be more specific)
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, target_port))
s.sendall(crazy_message)
s.close()
print("Message sent - if target vulnerable, MSMQ may hang or crash.")
except Exception as ex:
print("Exploit failed:", ex)
Note: The real exploit may involve a more specific message format based on MSMQ protocol, but this illustrates the basic idea.
DoS can be repeated to keep the service offline.
Importantly, this vulnerability does not allow code execution, privilege escalation, or data theft. It’s strictly about making the MSMQ service unavailable.
The official Microsoft update fully patches this problem.
- Update Windows: Install the January 2024 cumulative updates on all systems running MSMQ.
References and More Reading
- Microsoft Security Response Center Advisory CVE-2024-20661
- Microsoft Message Queuing official documentation
- Patch Tuesday January 2024 Overview (Blog)
Final Thoughts
CVE-2024-20661 is a cautionary tale about leaving unnecessary services enabled—or exposing them to the internet. Even services that don’t handle secrets can be a serious liability if they can be crashed by outsiders. If you use MSMQ: patch now, restrict network access, and monitor closely.
Timeline
Published on: 01/09/2024 18:15:49 UTC
Last modified on: 04/11/2024 20:15:12 UTC