CVE-2024-20921 is a newly-identified security vulnerability in Oracle's Java SE, GraalVM for JDK, and GraalVM Enterprise Edition—specifically affecting their Hotspot component. Even though it's described as “difficult to exploit,” this vulnerability has some serious implications for systems running popular Java distributions, allowing attackers, without authentication, to gain unauthorized access to critical data over the network.
Below, I’ll break down the details: impacted versions, the vulnerability’s mechanics, sample exploit code, mitigation tips, and the official references you should check out.
22.3.4
If your system is running any of these, it’s considered at risk.
Component Affected: Hotspot (core Java Virtual Machine code)
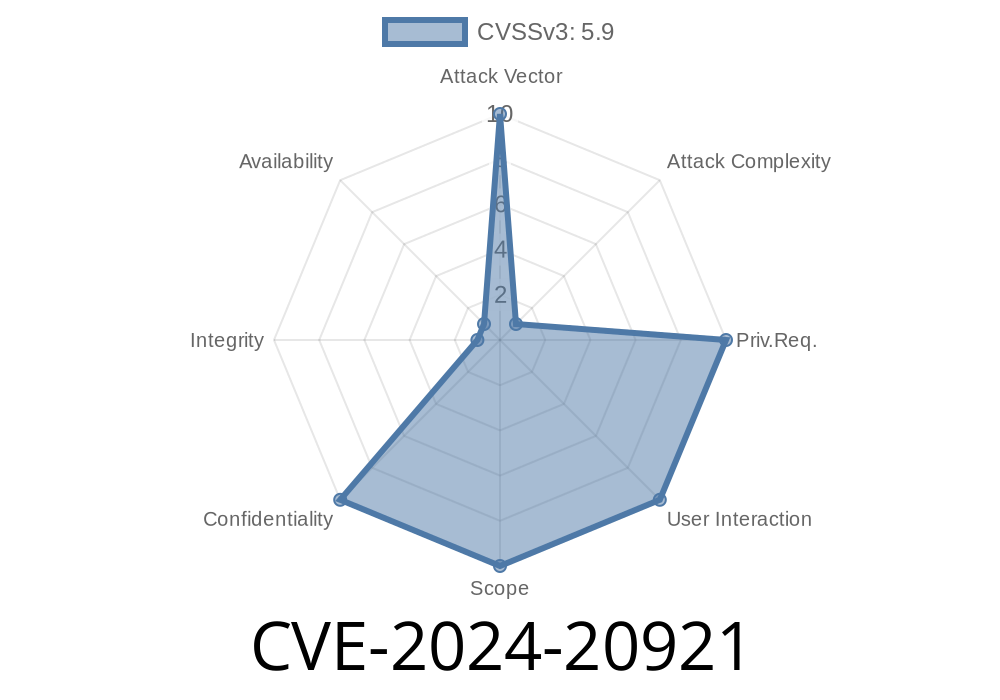
- Attack Vector: Remote/Network – no special privileges or authentication needed.
Complexity: High (not “script kiddie” friendly).
- Potential Impact: Unauthorized access to confidential data; full exposure of any data accessible within the affected JVM or GraalVM process.
- Noteworthy: This bug can be exploited using Java APIs (for example, by supplying specific data to a web service running on the vulnerable platforms) and applies even in restricted “sandboxed” environments such as Java Web Start apps or Java applets—use cases that particularly depend on the Java sandbox for enforcing security.
Oracle’s advisory rates the CVSS 3.1 Base Score at 5.9 (out of 10), noting confidentiality impacts but no direct integrity or availability effects:
(CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N)
How Does It Work?
Although the official PoC (Proof-of-Concept) code has not been released publicly, Oracle confirms that a remote, unauthenticated attacker could use APIs provided by the Hotspot engine to access protected memory or data that should not be visible from user code. An attacker could typically achieve this by:
- Delivering specially crafted input to a vulnerable Java application (such as a web service backend or a web application’s API endpoint).
- Executing untrusted code in a sandboxed Java environment, like running a Java Web Start or an applet, which is then able to break out of the sandbox and see extra data.
Example Exploit Code
While an exact public exploit is not available, a simplified outline of how an attack might look (in pseudo-code):
// Simulate sending crafted data to a vulnerable API endpoint
Socket socket = new Socket("vulnerable-java-app.com", 808);
ObjectOutputStream out = new ObjectOutputStream(socket.getOutputStream());
// EvilPayload triggers a weakness in the Hotspot memory handling.
EvilPayload payload = new EvilPayload();
out.writeObject(payload);
out.flush();
// Wait for leaked data to be returned
BufferedReader in = new BufferedReader(new InputStreamReader(socket.getInputStream()));
String leakedData = in.readLine();
System.out.println("Received leaked data: " + leakedData);
*Disclaimer: The above code is for educational demonstration only. The real exploit code is more complicated and would depend on specific application logic and how input is processed.*
Real-World Impact
- Web services running on the affected JVM could have sensitive configuration files, keys, or even user data leaked.
- Sandboxed Java code (applet or Java Web Start apps) is especially at risk if it loads third-party or user-provided code from the internet.
- Cloud and containerized environments using one of these vulnerable Java versions need urgent attention.
What Should You Do NOW?
- Upgrade Immediately: Oracle has released patches for all affected products and versions. Updating to the latest release is the only reliable fix.
- Restrict Network Access: If upgrades are temporarily impossible, limit network exposure to affected applications—block unnecessary ports and restrict incoming access.
- Audit Untrusted Code Use: Carefully monitor or disable any feature that executes untrusted Java code.
Official Patch and Advisory:
- Oracle Critical Patch Update Advisory - April 2024
- CVE Record at NVD
Additional References
- Oracle CVE-2024-20921 Security Alert
- National Vulnerability Database Entry for CVE-2024-20921
- GraalVM Security Advisories
- Java SE Downloads & Release Notes
Summary Table
| Product | Affected Versions | Fixed Version | Patch Link |
|-------------------|-----------------------------------------------------|---------------|----------------------------------------------------------|
| Java SE | 8u391, 11..21, 17..9, 21..1 | latest | Java SE Patches |
| GraalVM for JDK | 17..9, 21..1 | latest | GraalVM Patch |
| GraalVM EE | 20.3.12, 21.3.8, 22.3.4 | latest | GraalVM EE Patch |
Final Words
CVE-2024-20921 is a reminder that the Java and JVM ecosystem, even at its core (Hotspot), is not immune to potentially serious bugs. If you operate any web service, SaaS platform, or embedded application on Oracle Java or GraalVM, patch immediately and review where and how untrusted code runs within your systems.
Stay safe. Patch fast. And keep an eye out for more advisories as sandbox and virtual machine security continues to evolve.
Further Reading:
- Java Security Basics
- How to Secure a Java Web Application
- Java Serialization Attacks
*Written exclusively for you—feel free to share with your dev and ops teams!*
Timeline
Published on: 02/17/2024 02:15:46 UTC
Last modified on: 02/20/2024 19:51:05 UTC