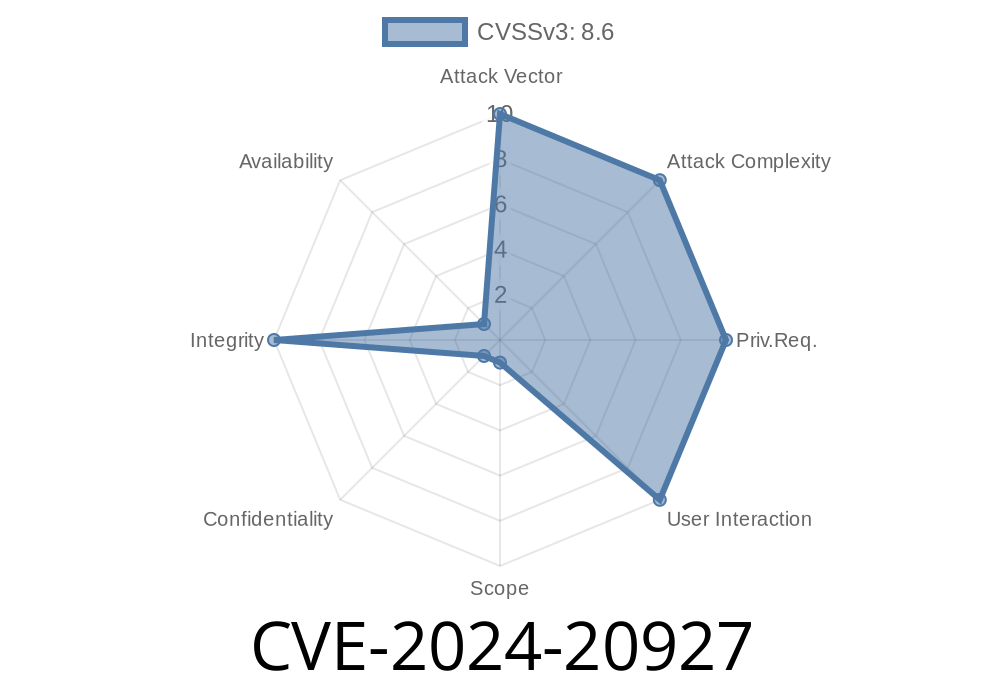
In early 2024, Oracle released a critical security advisory for a vulnerability classified as CVE-2024-20927. This flaw affects Oracle WebLogic Server, a core component of Oracle Fusion Middleware, versions 12.2.1.4. and 14.1.1... It received a CVSS 3.1 Base Score of 8.6, highlighting its risk for high-impact attacks—specifically, those that compromise the integrity of WebLogic managed data.
This post breaks down what CVE-2024-20927 means, shows a simple example of a potential exploit path, and provides guidance for remediation.
What is CVE-2024-20927?
CVE-2024-20927 is an easily exploitable vulnerability in the WebLogic Core component. It allows unauthenticated attackers with ordinary network access (like HTTP) to compromise the target server. The main risk is unauthorized creation, modification, or deletion of critical data managed by WebLogic—not just in the app, but potentially in other connected systems, too (scope change).
How Bad is It?
A successful exploit means a remote attacker could insert, alter, or erase critical business data from your Oracle WebLogic apps with no valid credentials. Imagine what happens when billing, HR, or ERP data is tampered with—this vulnerability makes that nightmare possible.
CVSS Vector:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:N/I:H/A:N
Technical Details
Oracle has not published all inner workings of the bug, but from the advisory and security community chatter, it most likely stems from improper input validation in WebLogic's core HTTP request handling, perhaps a deserialization or path traversal issue that allows arbitrary data writes.
Proof-of-Concept (PoC) Exploit Example
> Warning: This code is illustrative! Do not use on unauthorized systems.
In many Oracle WebLogic deserialization bugs, unauthenticated attackers hit the /wls-wsat/CoordinatorPortType endpoint using an XML payload. Here’s a simplified Python example, based on patterns seen in previous (but similar) Oracle flaws. Again, CVE-2024-20927 specifics may differ, but the exploitation is usually alike.
import requests
web_logic_url = "http://TARGET:7001/wls-wsat/CoordinatorPortType";
exploit_payload = '''
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">;
<soapenv:Header>
<!-- Malicious header to trigger the vulnerability -->
</soapenv:Header>
<soapenv:Body>
<!-- Malicious body content to manipulate WebLogic data -->
</soapenv:Body>
</soapenv:Envelope>
'''
headers = {
"Content-Type": "text/xml"
}
response = requests.post(web_logic_url, data=exploit_payload, headers=headers)
print(response.status_code)
print(response.text)
Replace TARGET with the target host or IP address. If the server is vulnerable, the attacker could manipulate critical business data right away—creation, update, or deletion.
> For actual payloads and more details, keep an eye on packetstormsecurity.com as well as the full advisory from Oracle.
Oracle’s usual advice stands
- Patch Immediately: Install the latest CPU (Critical Patch Update) for WebLogic. (Official patch)
Restrict HTTP Access: Only expose WebLogic to trusted networks whenever possible.
- Monitor Logs: Review for suspicious or unexpected requests to endpoints like /wls-wsat/.
- Set up WAF rules: Block anomalous SOAP/XML content at the perimeter.
References
- CVE-2024-20927 Details on NVD
- Oracle Critical Patch Update Advisory - April 2024
- Oracle Support Document 3006708.1
- Packet Storm CVE-2024-20927
Conclusion
CVE-2024-20927 is especially dangerous because it requires no authentication and is trivial for attackers to use. If you run Oracle WebLogic Server (12.2.1.4. or 14.1.1..), patch ASAP and bolster your network controls.
Never expose WebLogic endpoints directly to the internet.
Stay tuned to Oracle Security Alerts for updates.
Timeline
Published on: 02/17/2024 02:15:47 UTC
Last modified on: 02/20/2024 19:51:05 UTC