A newly disclosed vulnerability, CVE-2024-20945, affects Oracle Java SE and GraalVM products, threatening the security of systems that rely on Java technology. If you are running Oracle Java SE versions 8u391, 11..21, 17..9, or 21..1, or Oracle GraalVM for JDK / Enterprise in supported versions (see full list below), you are at risk. This post explains in plain English what the issue is, how it can be exploited, and what you can do to protect your systems.
Vulnerability Explainer
The vulnerability lies in the Security component across these Java platforms. A user with limited permissions, but with the ability to log onto the affected infrastructure (for instance, a developer or even a service account), could take advantage of this flaw by sending data to certain Java Security APIs. According to Oracle’s notes, data sent to these APIs—possibly via web services—can be crafted in such a way that it breaches the sandbox model Java usually enforces for untrusted code.
Applications supplying user data directly to Java Security APIs
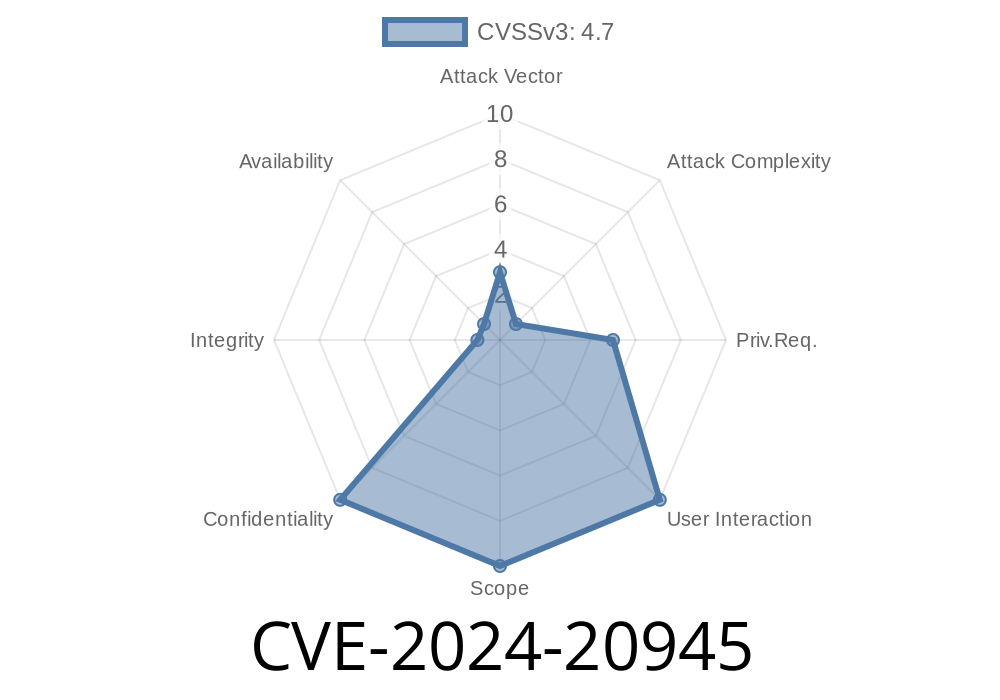
The vulnerability's CVSS score is 4.7, and while it's marked as "difficult to exploit" and requires some level of privilege and local access, it can result in unauthorized access to critical and complete data under Java’s protection.
- CVSS Vector: CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:U/C:H/I:N/A:N
C:H – High confidentiality impact
- I:N/A:N – No integrity/availability impact
What This Means in Practice
Imagine a Java EE or microservice in a cloud, accepting client data. If the service improperly passes this untrusted data into security-sensitive APIs, or loads code trusting the Java sandbox, an attacker could:
Exploit Example (Simplified)
While a full public exploit is not available (and Oracle discourages proof-of-concept sharing for active vulnerabilities), we can imagine a scenario where untrusted input is passed to a Security API:
Vulnerable pseudo-code
import java.security.AccessController;
import java.security.PrivilegedAction;
public class UnsafeExample {
public static void processUserInput(String input) {
// Potential mistake: running user-controlled code as privileged
AccessController.doPrivileged(new PrivilegedAction<Void>() {
public Void run() {
// Untrusted input is processed in a privileged block
evaluate(input);
return null;
}
});
}
private static void evaluate(String expr) {
// Dangerous: could access protected data via expression
System.out.println("Evaluating: " + expr);
// ...
}
}
If input comes from a web request or another user-controlled source, and privileged code lets it escape the Java sandbox, the attacker might gain access to secrets or files the environment intended to hide.
How Attackers Might Use This
1. Gain a foothold: Log in with any low-privileged account on a machine running affected Java versions.
2. Send crafted data: Communicate with poorly validated APIs or inject code into systems trusting the sandbox.
Bypass security boundaries: Retrieve private application data.
4. Exfiltrate sensitive information: Dump secrets, tokens, or config from memory/disk.
This flaw is dangerous especially for
- Shared development/build servers
Systems loading Java applets or running Web Start apps
Note: This exploit cannot be carried out over the network alone—attacker needs access to the same machine. But in cloud or CI/CD scenarios, that is often possible.
1. Update Immediately
- Oracle patched this vulnerability in its Critical Patch Update January 2024.
Oracle Resources
- Oracle Critical Patch Update Advisory - January 2024
- Oracle Java SE Security Vulnerabilities
- Oracle GraalVM Release Notes
References for Security Code Review
- Java Platform Security Architectural Overview
- doPrivileged pitfalls
Final Thoughts
CVE-2024-20945 is a reminder that even advanced security platforms like Java and GraalVM are only as safe as their weakest component. While exploitation requires some effort and access, the result—unauthorized reading of all your sensitive Java-application data—is a serious concern. Until you patch, do not trust the Java sandbox for protecting against local attackers, and absolutely avoid running or loading untrusted code.
Stay safe—patch early and review your privilege boundaries!
Note: This article is exclusive for security awareness purposes and does not encourage malicious activity. Always test responsibly and within the scope of your organization's security policy.
Timeline
Published on: 02/17/2024 02:15:48 UTC
Last modified on: 02/20/2024 19:51:05 UTC