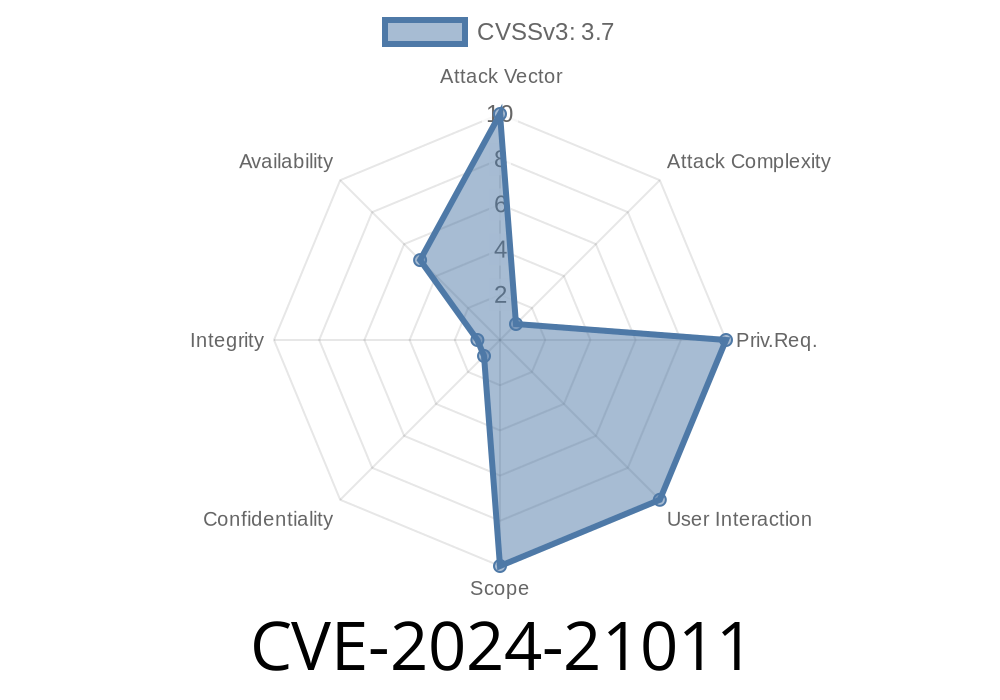
On January 16th, 2024, Oracle published its Critical Patch Update, including details of CVE-2024-21011, a vulnerability affecting the Hotspot component of Oracle Java SE and GraalVM distributions. The flaw is rated with a CVSS 3.1 base score of 3.7, meaning its impact is limited, but it’s important for those who maintain Java services, especially on the internet.
In this article, we’ll break down CVE-2024-21011 in simple terms, look at how it might be exploited, offer code and reference links, and give advice on how you can stay secure.
What is CVE-2024-21011?
CVE-2024-21011 is a vulnerability in Oracle Java SE’s Hotspot virtual machine, as well as Oracle GraalVM for JDK and GraalVM Enterprise Edition. The vulnerability affects the following product versions:
Oracle GraalVM Enterprise Edition: 20.3.13, 21.3.9
The flaw allows unauthenticated attackers with network access to cause a partial Denial of Service (DoS). This means they might be able to crash or slow down Java services running on affected systems, but cannot steal data or take control.
Availability (A): Low
Full vector:
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L
How Could This Be Exploited?
CVE-2024-21011 is considered difficult to exploit. An attacker does not need to log in or get a user’s help, but must send specially crafted network requests using certain Hotspot APIs—possibly via a web service you are running.
The service calls certain Hotspot APIs that do not properly check input.
- An attacker finds a way to send data through your service that triggers the bug, potentially crashing your Java process or making it unresponsive.
According to Oracle, the flaw can also affect
- Java applets or Java Web Start applications loaded from the internet that process untrusted data.
An attacker crafts a network request to a vulnerable Java or GraalVM service.
2. The request includes data that, when passed to a specific Hotspot API, triggers the bug (such as an infinite loop, resource exhaustion, or unexpected exception).
Example Code (Hypothetical)
Oracle has not provided exact triggering code due to disclosure policies. But, typical Denial of Service attacks in Java involve overloading resource-intensive APIs. Here’s a simplistic illustrative example using input that could stress a system (note: this is a stand-in, not the actual vulnerability):
import java.util.Base64;
public class DoSExample {
public static void main(String[] args) {
// Simulate attacker-supplied data (very large input)
String bigInput = "A".repeat(100_000_000);
// Vulnerable API call (hypothetical)
byte[] decoded = Base64.getDecoder().decode(bigInput);
System.out.println("Decoded " + decoded.length + " bytes");
}
}
An attacker might find an API (in Hotspot or a service using it) that, when given very large or malformed input, causes high CPU or memory usage. In reality, the vulnerable code would involve a specific API in Hotspot, and would probably not be as obvious as above.
Why Does This Matter?
While the risk is "partial Denial of Service," for web servers, APIs, or cloud services, even minor interruptions can be a big deal. Attackers could slow down or force restarts, hurting reliability and user trust.
Java sandboxed environments—like applets—are _also_ at risk if they accept code or data from untrusted sources.
Can it be automated? Only with a custom payload and target knowledge.
There’s no "ready-to-use" exploit public at the time of this writing. However, a security researcher could discover patterns that cause services using vulnerable Java/GraalVM versions to hang or crash by fuzzing exposed APIs.
Official Oracle Critical Patch Update advisory (January 2024):
https://www.oracle.com/security-alerts/cpujan2024.html
NVD entry for CVE-2024-21011:
https://nvd.nist.gov/vuln/detail/CVE-2024-21011
Monitor for abnormal behavior:
- Watch for sudden CPU/memory spikes and service crashes.
Conclusion
CVE-2024-21011 isn’t a headline-making bug, but it’s a reminder that even mature platforms like Java have tricky edge-cases with real-world impact. If you run Java, GraalVM, or associated Oracle products on the affected versions—especially if you handle data from the public internet—patch and review your usage.
Staying ahead of vulnerabilities relies on community awareness. Keep your systems updated, review advisories, and encourage responsible testing and disclosure.
Stay safe, and keep coding securely!
*This post is original content. Please see the official links above for further technical details as they become public!*
Timeline
Published on: 04/16/2024 22:15:15 UTC
Last modified on: 04/26/2024 09:15:10 UTC