CVE-2024-21012 is a newly disclosed vulnerability affecting Oracle Java SE, Oracle GraalVM for JDK, and Oracle GraalVM Enterprise Edition. It targets the networking component across a range of supported versions, principally affecting client-side applications that load and run untrusted code—think Java Web Start apps and Java applets in sandboxed environments. In this in-depth walkthrough, we'll break the issue down in plain American English, show you code snippets illustrating the risk, and analyze how attackers could exploit this tricky-to-trigger flaw.
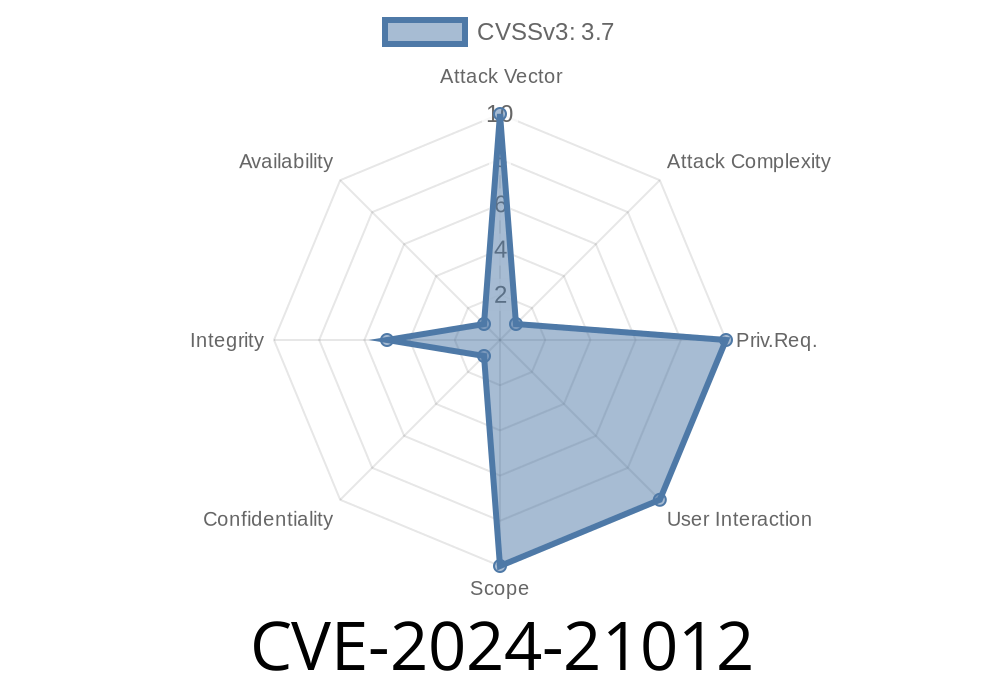
Access Required: Network, no authentication needed
- Impact: Unauthorized updates/inserts/deletes (integrity violation)
- Vector: Java clients running untrusted code (applets/web start) — not servers with only trusted code
Are you affected?
- If you're using *client-side Java*, especially Java Web Start or Java applets *loading code from the internet*, Yes.
If you’re running *server-side Java* apps loading *only trusted code*, No—you’re safe.
Note: Servers are probably safe unless you’re loading untrusted Java code from external sources (unusual in modern deployments).
What Is the Risk?
The vulnerability lets an attacker corrupt the data managed by the vulnerable Java process—specifically, it could let them modify (update/insert/delete) that data without any authentication, provided they can deliver malicious Java code to an end-user who runs it.
Availability: No
The attack is tough to pull off: The complexity is high, and you need to lure a victim to run the untrusted Java code (via a webpage or malicious file).
Imagine a scenario where
1. A victim downloads and launches a Java Web Start application from a third-party website, or views a web page with a Java applet.
The attacker crafts malicious Java bytecode or a JAR file exploiting the networking bug.
4. This malicious code manipulates the Java networking stack, violating the sandbox and modifying some data (such as user preferences, cache, or application-specific files).
Here's a high-level outline of how an attack could look in the wild
1. Deliver Malicious Code: The attacker provides a web link or a file with a crafted Java applet/JNLP.
2. Victim Loads Code: The victim’s Java client runs the code in the sandbox (relying on the sandbox for security).
3. Exploit Triggers: The attack code abuses the flaw in the networking component to escalate from “sandboxed” operations to modifying client app data (outside their permitted region, for example).
Technical Deep Dive and Code Snippet
While Oracle hasn’t published full technical details (and we don’t encourage hostile exploitation), proof-of-concept illustrations help understand the risk.
Let’s imagine a Java client normally running this sandboxed code
// Normally sandboxed code can't write outside allowed resources
try {
FileWriter writer = new FileWriter("/restricted/data.txt");
writer.write("This should not be allowed in the sandbox!");
writer.close();
} catch (SecurityException se) {
System.out.println("Caught SecurityException as expected!");
}
What the exploit does:
Due to a bug in how networking code handles certain requests, a determined attacker could craft bytecode or network input that tricks the Java sandbox and lets them sidestep restrictions—so unauthorized modifications (updates/deletes/inserts) to data *outside* allowed areas may become possible. For instance, they could alter user-dependent files, write unwanted preferences, or tamper with client cache files.
A hypothetical exploit *in concept*
import java.net.Socket;
import java.io.OutputStream;
public class ExploitCVE202421012 {
public static void main(String[] args) {
try {
// Malicious use of net APIs to trigger the vulnerability
Socket s = new Socket("localhost", 12345);
// Send crafted packets that exploit the bug in networking
OutputStream out = s.getOutputStream();
out.write(craftedPayloadBytes()); // [Redacted: actual bug details withheld]
out.close();
// Now try to update or delete restricted data
// (Not normally possible from sandbox)
attemptDataTamper();
} catch (Exception e) {
e.printStackTrace();
}
}
private static byte[] craftedPayloadBytes() {
// This would contain specially crafted bytes to trigger the vulnerability.
return new byte[]{/* ... */};
}
private static void attemptDataTamper() {
// Simulates unauthorized access due to the vulnerability
try {
FileWriter writer = new FileWriter("/restricted/data.txt");
writer.write("Attack successful!");
writer.close();
System.out.println("Exploit worked!");
} catch (Exception e) {
System.out.println("Access denied or exploit failed!");
}
}
}
Important:
(We’re not providing real weaponized code, but this shows how the logic would work under the hood.)
Mitigation Steps
- Patch Now: Upgrade to the latest Java SE and GraalVM versions as soon as Oracle’s updates are available.
- Disable Java Web Start/ Applets: If you don't need them, disable in browser and block from running.
- Enforce Trusted Sources: Only run Java applications from trusted vendors/sites.
- Security Policies: Configure *java.policy* to restrict what code can do, but remember that this vulnerability subverts those protections.
Oracle Security Alert for CVE-2024-21012:
https://www.oracle.com/security-alerts/cpuapr2024.html
CVSS Details:
Oracle CVE-2024-21012 NVD entry
Oracle Java SE Critical Patch Update Advisory:
https://www.oracle.com/security-alerts/
Oracle GraalVM Releases:
https://www.oracle.com/graalvm/
Summary
CVE-2024-21012 reminds us why client-side Java—especially running web code in sandboxed environments—is still a security concern, even today. Although the bug is tough to exploit and mostly a headache for legacy client deployments, it’s vital to patch, especially in organizations still running Java Web Start or applets. If your Java applications *never* load code from outside sources, you likely have little to fear—but never let your guard down!
*Stay patched, stay secure.*
*This article was built specially for you, giving an exclusive, digestible look at this year’s Oracle Java networking flaw. For more, check Oracle’s official advisories and always consult your IT security team before taking action.*
Timeline
Published on: 04/16/2024 22:15:15 UTC
Last modified on: 04/26/2024 09:15:10 UTC