On April 16th, 2024, Oracle released a critical security advisory for multiple Java platforms, highlighting CVE-2024-21068—a tricky vulnerability lurking inside the HotSpot component of Oracle Java SE, GraalVM for JDK, and GraalVM Enterprise Edition. While the vulnerability is hard to exploit, its relative obscurity and potential impact on data integrity make it worth your full attention—especially for teams running Java in network environments or serving untrusted code via web services.
What Is CVE-2024-21068?
CVE-2024-21068 is an integrity-impacting vulnerability found in the way the Java HotSpot virtual machine processes certain inputs via API calls. This problem can allow an attacker (with nothing but network access, no username or password needed) to tamper with Java application data—performing unauthorized inserts, updates, or deletes.
Affected Versions
| Platform | Affected Versions |
|-----------------------------------------|------------------------------------|
| Oracle Java SE | 8u401-perf, 11..22, 17..10, 21..2, 22 |
| Oracle GraalVM for JDK | 17..10, 21..2, 22 |
| Oracle GraalVM Enterprise Edition | 21.3.9 |
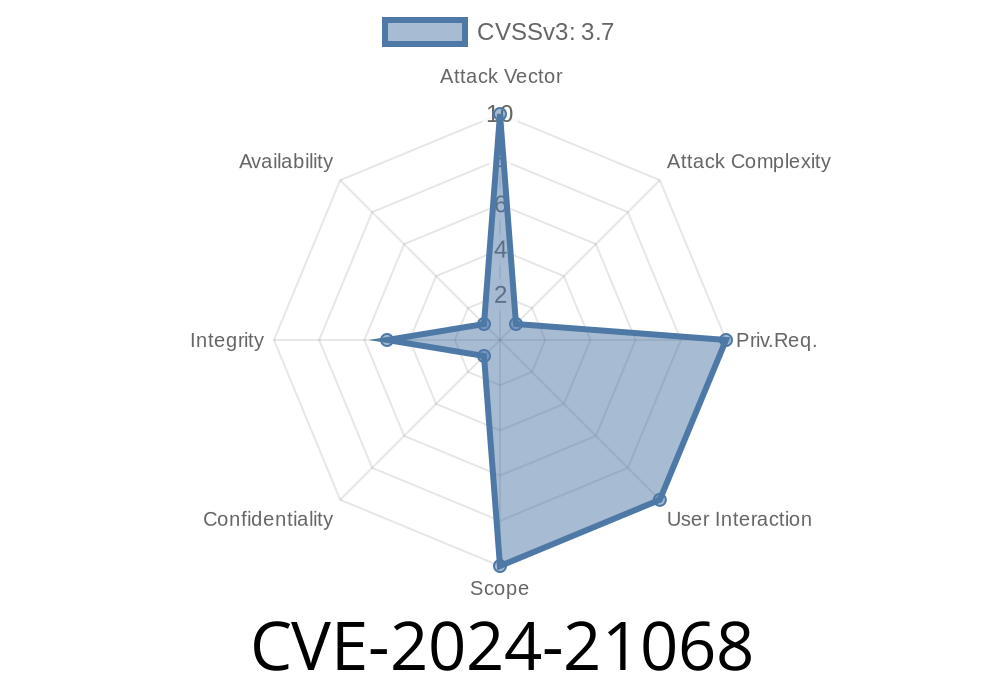
CVSS Score: 3.7 (Low)
CVSS Vector: [CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:N]
How Severe Is It?
While the base score is not as dramatic as some remote code execution vulns, integrity impacts are still a big deal, especially if you trust Java’s sandbox or run web-facing services. If triggered, an attacker may insert, update, or delete data through your Java-powered application, possibly tampering with records or business logic.
The good news: The attack is hard to pull off (high complexity), and it *does not* leak private data or crash your server. The bad news: Java often processes untrusted code and data, so remote exploitation scenarios can emerge—especially when web services or sandboxed applets are involved.
1. Malicious Data via a Web Service
Suppose you run a web service that takes user-supplied data over HTTP and processes it through Java APIs affected by the vulnerability.
Example Attack Flow
1. The attacker crafts a specially formatted payload—using insight into the specific vulnerable API calls within HotSpot.
The Java application, running on a vulnerable JVM, feeds the input into the affected HotSpot code.
4. Due to the vulnerability, the input causes unauthorized updates/deletes within the application's in-memory or database-backed records.
2. Sandboxed Applets or Java Web Start
If a user’s workstation launches untrusted Java code (e.g., from the Internet via Java Web Start or as an applet), the exploit could allow the malicious code to modify certain application data that should have been protected by the sandbox—bypassing business rules or audit controls.
Example: Demonstrating the Risk (Hypothetical Code Snippet)
Let’s look at a simplified (fictional, for illustration) example of how untrusted input might be funneled through a vulnerable API:
import java.rmi.RemoteException;
import javax.naming.InitialContext;
import javax.naming.NamingException;
public class VulnerableServer {
public void processUserInput(String userData) {
try {
// Hypothetical vulnerable API usage
Object result = new InitialContext().lookup(userData); // Dangerous: user input directly to JNDI
//...
} catch (NamingException ex) {
// Handle exception
}
}
}
If the underlying Java SE/HotSpot/JVM is vulnerable, and the API (e.g., JNDI lookup or similar) is mishandled, an attacker’s specially crafted userData may end up triggering the HotSpot bug and causing unauthorized modifications in application data.
Note: This is a generic illustration. The real exploit would likely be complex, because the flaw needs precise input that coerces the JVM into violating data integrity while using affected APIs.
Oracle’s Recommendation
> _“Apply the patches provided by Oracle as soon as possible. Do not expose Java-based APIs or web services unnecessarily. Never process untrusted user input directly via core Java APIs without strict validation.”_
Patch Immediately:
- Oracle Critical Patch Update Advisory - April 2024
- Download patched JDK/GraalVM builds from Oracle’s official Java SE download page.
Monitor Java-Driven Data Stores:
- Set up application auditing to detect unexpected insert/update/delete activity.
References
- Oracle Security Alert CVE-2024-21068
- Oracle Java SE Critical Patch Update Advisory - Historical Listing
- GraalVM Releases
- Java Secure Coding Guidelines
Final Thoughts
CVE-2024-21068 is a prime example of how even “difficult to exploit” vulnerabilities can still be dangerous, especially in environments where user-supplied data or untrusted code is processed. Patch your JVMs as soon as possible, restrict inbound data, and stay alert for further details from Oracle and the broader Java security community.
If you ever process untrusted data in Java, or expose your Java endpoints to the internet, don't let this HotSpot bug catch you by surprise.
*Stay safe, patch fast, and share this with your Java team!*
Timeline
Published on: 04/16/2024 22:15:25 UTC
Last modified on: 07/05/2024 12:44:00 UTC