If you’re running an Oracle E-Business Suite system, you need to pay attention to the latest vulnerability, CVE-2024-21071. This critical security hole affects the _Oracle Workflow_ product, specifically the Admin Screens and Grants UI component, in versions 12.2.3 through 12.2.13.
In this post, I’ll break down what this vulnerability is, why it matters, share some example code, outline exploit possibilities, and provide further references so you can dig deeper. Let's keep it simple and actionable.
What Is CVE-2024-21071?
CVE-2024-21071 is a vulnerability that can be easily exploited by an attacker who already has high privileges in Oracle Workflow, as long as they have network access via HTTP. The dangerous part: although the bug sits in Oracle Workflow, it can impact other E-Business Suite products (scope change).
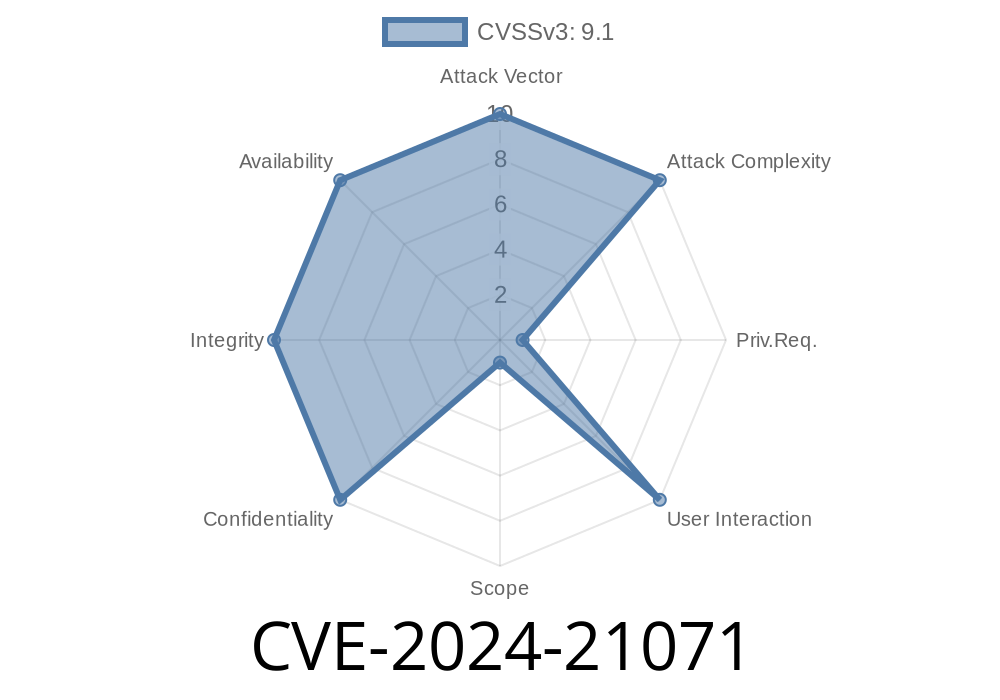
CVSS 3.1 Base Score: 9.1 (Critical)
- CVSS vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
References
- Oracle Critical Patch Update Advisory - April 2024
- NVD CVE Record: CVE-2024-21071
Technical Summary
This vulnerability sits in the way the Workflow Admin Screens/Grants UI processes HTTP requests. Specifically, a high-privilege user can send a crafted request that triggers unsafe handling of workflow admin operations, potentially allowing arbitrary code execution or privilege escalation—no user interaction required.
In plain English: if an attacker already has a powerful user account in Oracle Workflow, they can exploit this bug from anywhere on the network and take over the system.
Example Exploit Scenario
Let’s walk through a generic example (Note: the real exploit details are not public, but we’ll simulate what an exploit might look like based on similar Oracle Workflow bugs):
Suppose the workflow admin UI has a vulnerable parameter, action_id, in an HTTP POST request, which isn’t properly sanitized.
Example Exploit Request
POST /workflow/admin/grants HTTP/1.1
Host: ebs.example.com
Cookie: ORA_WF_SESSION=abcdef123456
Content-Type: application/x-www-form-urlencoded
action_id=1001092&command=grantAll&user=public
Malicious users could manipulate the command or action_id parameters, injecting commands or bypassing boundary checks, for example:
action_id=1001092 OR 1=1; -- &command=grantAllPrivileges&user=ADMIN
Example: Mass Data Exposure Snippet
If there’s a flaw that lets SQL or workflow commands run directly, attacker could use something like:
UPDATE wf_users SET is_admin='Y' WHERE user_name='attacker';
Associated request might resemble
POST /workflow/admin/grants HTTP/1.1
...
command=updateUser&user=attacker&set_admin=1
Disclaimer: The above requests are illustrative and may not match the exact real-world exploit.
When we look at the CVSS 9.1 score, it's clear—_this is a critical bug_. The combination of
- Easy network access (just HTTP to the right port/IP)
The ability for workflow admins (or compromised workflows) to become superusers
... means attackers who have any foothold inside your Oracle E-Business Suite workflow environment can quickly escalate and potentially take over connected applications as well.
How To Protect Yourself
- Patch immediately: Oracle has released a fix—apply the April 2024 Critical Patch Update ASAP.
- Restrict admin access: Until patched, limit admin user network access, use VPNs, and layer other authentication.
- Monitor logs: Watch for abnormal admin UI activity or privilege escalation attempts in your workflow logs.
More Reading and References
- Oracle Security Alerts & Updates
- Oracle E-Business Suite Support Docs
- NVD CVE-2024-21071 Entry
Recommendations
If you operate Oracle E-Business Suite, prioritize this patch. If you’re already running version 12.2.3–12.2.13, attackers with admin-level workflow access and network presence can potentially run roughshod over your system in just a few HTTP requests.
Timeline
Published on: 04/16/2024 22:15:25 UTC
Last modified on: 04/17/2024 12:48:31 UTC