Oracle’s recent security advisory unveiled CVE-2024-21085—a subtle yet potent vulnerability lurking within the Concurrency component of Oracle Java SE and Oracle GraalVM Enterprise Edition. Even though exploitation is tricky, it paves the way for an unauthenticated attacker to cause partial Denial-of-Service (DoS) using network-accessible vectors. Let’s break down what makes CVE-2024-21085 notable, how it could be exploited, and how you can safeguard your systems.
Oracle GraalVM Enterprise Edition: 20.3.13, 21.3.9
Note: Older and other versions may not be directly affected, but always check Oracle’s official advisory for the latest updates.
What’s the Issue?
This vulnerability sits in the “Concurrency” component. Attackers, without any authentication, can hit Java applications over multiple network protocols. If the application exposes relevant APIs to the network—for instance, via RESTful web services or Java RMI—the attacker can send specifically crafted requests. Successful use of this bug can hang or slow down the Java instance—partial DoS—but can’t steal or tamper with data directly.
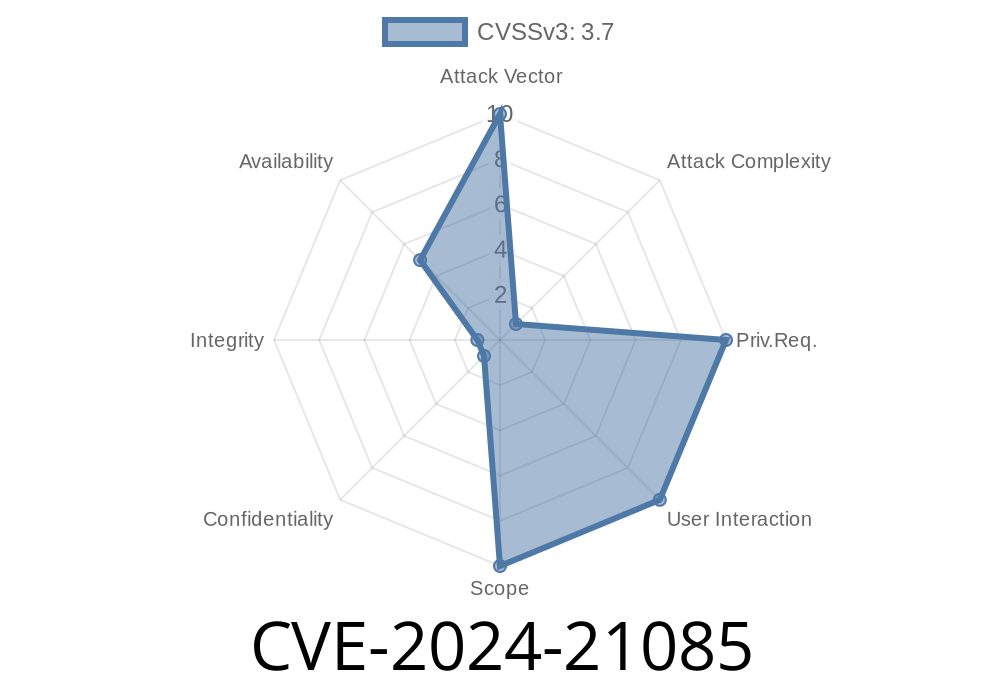
Oracle flagged this as “Difficult to exploit” and scored it as CVSS 3.7
AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L
How Does It Work?
Without diving into Oracle’s proprietary code, the flaw hinges on how Java concurrency objects—likely Executors, ForkJoinPools, or work queues—handle malicious or runaway code submitted by the application or exposed REST endpoints.
In vulnerable versions
- Attackers might be able to submit tasks or jobs that get stuck, enter infinite loops, or otherwise starve thread pools.
- If such APIs are not properly sandboxed or protected, an attacker’s crafted job could hog all execution slots, blocking legitimate work.
Suppose your Java application has this basic REST endpoint
@Path("/runJob")
public class JobResource {
private final ExecutorService executor = Executors.newFixedThreadPool(5);
@POST
@Consumes(MediaType.APPLICATION_JSON)
public Response runJob(String jobCode) {
Runnable task = compileToRunnable(jobCode); // Danger: Running untrusted code!
executor.submit(task);
return Response.ok("Job submitted!").build();
}
}
If no authentication or rate-limiting protects this endpoint, an attacker can submit dozens or hundreds of malicious tasks—infinite loops, while(true) blocks, or code that abuses thread resources.
Result:
Thread pool saturates with never-ending tasks. Your service is still up… but real users wait in line forever (partial DoS).
Let's say the attacker can submit this “job” to the server
public class Attacker implements Runnable {
@Override
public void run() {
// Infinite loop: saturate a thread in executor pool
while (true) {
// Burn CPU, never exit
}
}
}
Because the attacker can submit as many “Attacker” jobs as there are threads in the pool, all legitimate tasks get locked out.
Realistic Exploitation Paths
- Untrusted web service APIs (/submitJob, /runTask, etc.) that run arbitrary code.
- Java Web Start / applets running untrusted code expecting the Java sandbox to protect them.
RMI services that allow arbitrary remote jobs.
Important: Even well-intentioned “sandboxing” isn’t always enough, since abusing concurrency can lock up server resources until restart.
Defensive Measures
1. Patch Immediately: Oracle’s April 2024 CPU includes fixes—Upgrade Java SE and GraalVM to the latest versions.
2. API Hardening: Never expose APIs that execute submitted code without strong authentication/validation.
Validate any input that triggers code execution.
4. Sandbox Untrusted Code: Do not assume the Java sandbox is bulletproof against resource exhaustion bugs.
References
- Oracle: CPU April 2024 Advisory (CVE-2024-21085)
- NVD: CVE-2024-21085 Details
- GraalVM Enterprise Downloads & Updates
Conclusion
CVE-2024-21085 won’t let an attacker take over your Java servers or steal confidential data, but it lets them slow down or freeze your Java apps through abused Concurrency APIs—especially in cloud or enterprise settings with public endpoints. Review your exposure, patch up, and double-check any endpoint that runs user-submitted code or tasks.
Timeline
Published on: 04/16/2024 22:15:28 UTC
Last modified on: 04/26/2024 09:15:11 UTC