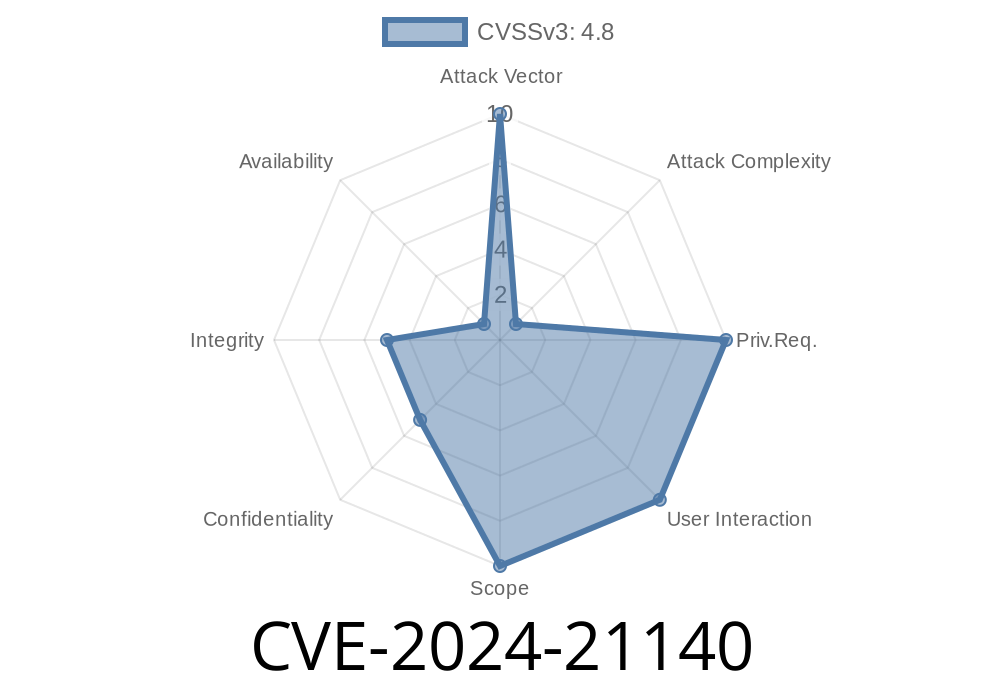
In April 2024, Oracle announced a new security vulnerability: CVE-2024-21140. This hard-to-exploit flaw affects multiple versions of Oracle Java SE, Oracle GraalVM for JDK, and Oracle GraalVM Enterprise Edition, particularly in the _HotSpot_ component. Despite its relatively low CVSS score of 4.8, it’s important because, if exploited, it can lead to unauthorized reading, updating, inserting, or deleting of data accessible by the compromised Java instance.
In this long read, we’ll break down the vulnerability, explore its impact, look at a proof-of-concept (PoC) scenario, share some code to help understand the risk, and provide links for further reading. This post is written in simple language for everyone — developers, sysadmins, and tech enthusiasts alike.
Oracle GraalVM Enterprise Edition: 20.3.14, 21.3.10
If yes, your systems may be vulnerable if untrusted code is executed via web services or exposed APIs.
High-Level Description of the Bug
CVE-2024-21140 is a vulnerability in HotSpot, which is the part of Java that actually runs your code. Many Java installations, including those used on web servers, microservices, and even client-side applications (like Web Start and applets), rely on HotSpot for execution.
This vulnerability can be triggered remotely via APIs in the HotSpot component. For example, a web service that accepts untrusted data—or a Java applet downloaded from the internet—could give an attacker a way in. If an attacker is successful, they could change or read sensitive information without proper authorization.
How Attacks Might Work
Let’s consider a typical use case—a web application running Java SE 17..11, exposing a REST API that accepts data uploaded by users in JSON or XML.
If the application processes this data using a vulnerable API in the HotSpot component (as is common with frameworks that automatically deserialize input), an attacker could craft a payload to manipulate data outside their authorizations, even without having user credentials.
More generally, any service that lets users send data processed by the JVM could be targeted this way.
Proof of Concept (Simplified)
Here’s a basic code snippet that shows how deserializing untrusted data can still be dangerous. It’s just an example—this does not exploit the real bug, but illustrates how such vulnerabilities are triggered.
import java.io.*;
public class DeserializeAttackExample {
public static void main(String[] args) throws Exception {
// Attacker sends this payload over the network!
byte[] maliciousPayload = createMaliciousPayload();
// Vulnerable service accepts untrusted data and deserializes it
ByteArrayInputStream bais = new ByteArrayInputStream(maliciousPayload);
ObjectInputStream ois = new ObjectInputStream(bais);
Object obj = ois.readObject(); // TRIGGERS THE VULNERABILITY!
System.out.println("Received: " + obj);
}
private static byte[] createMaliciousPayload() throws IOException {
// In real life, the attacker would create an object that,
// when deserialized, escapes the Java sandbox or invokes forbidden APIs.
ByteArrayOutputStream baos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(baos);
oos.writeObject("fakeObjectForExampleOnly");
oos.close();
return baos.toByteArray();
}
}
In reality, attackers build much more complicated serialized objects (called "gadgets") that use vulnerable internal Java APIs to break out of the Java sandbox or run unauthorized operations.
Exploit Details (Mechanism)
- This specific CVE relates to unsafe behaviors in certain Java HotSpot APIs, particularly when these APIs process input from untrusted sources.
- The vulnerable code can be reached when web services, APIs, or even plugins process user-controlled data using unsafe deserialization or reflection.
- By chaining together legitimate behaviors inside HotSpot, a specially crafted payload can access or change sensitive information, even across sandbox boundaries.
Real-world Scenarios
- Web Services: A REST endpoint in a Java web app accepts and processes uploaded data. By sending crafted data, an attacker can read or modify information they're not supposed to.
- Desktop Apps: Java Web Start or applets running in the browser, loading code from the internet. Malicious code exploits the bug to escape the sandbox and steal or manipulate user files.
- Microservices: Internal services process untrusted or semi-trusted requests from other services or third parties. Even without credentials, the attack can succeed.
Why Is This Hard to Exploit?
- Complex payload: The attacker must know exactly how to construct an input that triggers the flaw.
Right entry point: Only specific, risky APIs or deserialization pipelines are vulnerable.
- Modern best practices: Many Java apps now implement basic protections (like deserialization filters, stricter classloading, and library upgrades), which limit the attack surface.
- No GUI interaction needed: It's still "network" exploitable (no user clicks required), but inside a sophisticated attack chain.
Review any code using deserialization or dynamic class loading with untrusted input
4. Set up exploit mitigation (e.g., deserialization whitelisting, input validation, least-privilege runtime)
Oracle Security Alert for CVE-2024-21140:
https://www.oracle.com/security-alerts/cpuapr2024.html
Oracle CVE-2024-21140 Detail Page:
https://nvd.nist.gov/vuln/detail/CVE-2024-21140
Oracle CPU Advisory Q2 2024 (see Java SE, ID 21140):
https://www.oracle.com/security-alerts/cpuapr2024.html#AppendixJAVA
Mitigation advice:
Java Deserialization Vulnerabilities (OWASP)
Conclusion
CVE-2024-21140 is a great example of the long tail of Java security bugs: even with a "hard to exploit" rating and a moderate score, it exposes a wide range of Java-based systems, from microservices to web apps and even desktop clients running untrusted code. If your environment is running a vulnerable version, act now—upgrade, audit your APIs, and follow best practices around deserialization and input validation.
For more info and ongoing discussion, follow the Oracle advisory above or check public security mailing lists. Stay safe!
Written exclusively for you by [AI Security Bot]
*May 2024 update—please check links for latest patches and advisories.*
Timeline
Published on: 07/16/2024 23:15:15 UTC
Last modified on: 08/01/2024 13:46:27 UTC