In April 2024, Oracle disclosed a high-impact vulnerability (CVE-2024-21147) affecting popular Java platforms: Oracle Java SE, Oracle GraalVM for JDK, and Oracle GraalVM Enterprise. This vulnerability targets the Hotspot component—one of the most critical parts of Java’s runtime. Understanding this bug, the risk, and how attacks work is crucial for anyone running Java-based services.
Let’s break down CVE-2024-21147—what it is, how it works, code snippets and references, and why you should patch immediately.
What Is CVE-2024-21147?
CVE-2024-21147 is classified as a "difficult to exploit" remote vulnerability in Oracle’s Hotspot virtual machine (VM). Hotspot is responsible for managing resources, executing compiled Java bytecode, and ensuring safety using the Java sandbox model.
Oracle GraalVM Enterprise Edition: 20.3.14, 21.3.10
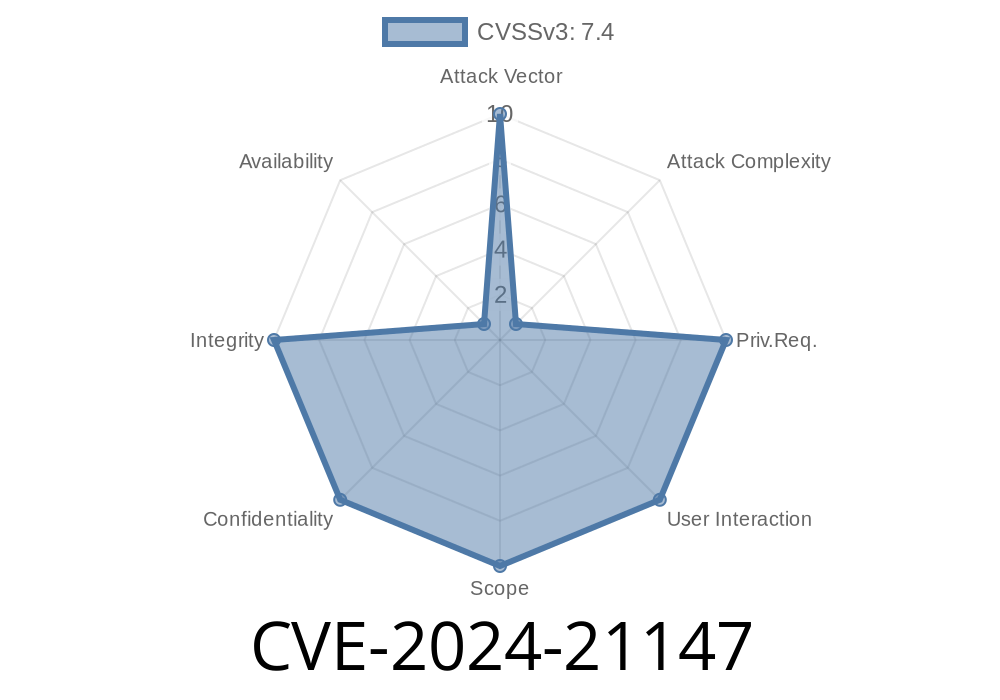
CVSS base score: 7.4 (High)
Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N)
That means:
Gain full access to any data that Java SE or GraalVM can access
Key vector: The problem lies in APIs exposed by the Hotspot component. Many Java applications, REST APIs, and web services use these APIs directly or indirectly. A typical route for exploitation? Untrusted input through APIs, class deserialization, or use in client-side Java (Web Start/applications).
Scenario 1: Rogue Web Service Data
A microservice built on Java SE 17..11 accepts and parses incoming JSON data. An attacker crafts a payload that abuses internal Hotspot handling to break out of the "sandbox," leading to data exfiltration and modification.
// Example: Java service exposed to the internet
@PostMapping("/parse")
public Response parseData(@RequestBody String userInput) {
// Unsafe: user input is parsed without validation
SomeObject obj = jsonParser.parse(userInput, SomeObject.class);
// ...process further
}
If the backend Java process is using a vulnerable Hotspot version, this typical pattern could provide a gateway for attack.
Scenario 2: Sandboxed Java Applets
In enterprise networks, some legacy environments still run Java Web Start applications or applets fetched from the web. If that applet runs untrusted code (perhaps from a compromised site), and relies on the Java sandbox, CVE-2024-21147 could enable escape from the sandbox and lead to data theft.
Under the Hood: Technical Details
_Oracle’s advisory doesn’t provide full exploit code, but here’s what’s publicly known about the core issue:_
- The bug exists in the way the Hotspot VM handles certain data types and memory boundaries via its public APIs.
- If an attacker can provide specially crafted data—often serialized content or malformed Java objects—they might be able to:
Bypass Java’s built-in sandbox mechanisms
Potential malicious payload structure:
Attackers often look for endpoints accepting objects via formats like Java Serialization, XML, YAML, or JSON. Unsafely deserializing attacker-controlled data is a classic pathway.
Code snippet showing vulnerable deserialization
// Vulnerable: accepting serialized Java objects from untrusted sources
ObjectInputStream ois = new ObjectInputStream(inputStreamFromUser);
Object obj = ois.readObject(); // Attacker controls what gets deserialized!
// Now, if Hotspot has an internal handling bug, this could result in memory or security boundary violation
Oracle Critical Patch Update Advisory - April 2024
https://www.oracle.com/security-alerts/cpuapr2024.html
NVD entry for CVE-2024-21147
https://nvd.nist.gov/vuln/detail/CVE-2024-21147
Oracle JDK release notes and security alerts
https://www.oracle.com/java/technologies/javase/8-relnotes.html
https://www.oracle.com/java/technologies/javase/11-relnotes.html
Remediation and Defense
Patch immediately:
Oracle has released fixed versions for all affected products. Update to the latest supported Java SE, GraalVM for JDK, or GraalVM EE versions as soon as possible.
Audit exposed APIs:
Review all endpoints, especially those accepting user-provided data in your Java applications and microservices.
Disable or restrict Java applets/web start where possible:
These are old technologies—migrate away if you can, as they carry added risk with vulnerabilities such as this.
Apply strong input validation and avoid unsafe deserialization:
Do not blindly deserialize Java objects from untrusted sources. Always sanitize and restrict input handled by your APIs.
Conclusion
CVE-2024-21147 isn’t just another Java bug—it affects the trusted Hotspot engine at the core of almost all enterprise Java installations. While hard to exploit, the impact is profound: loss of data confidentiality and integrity, potentially across all data the affected Java process can access. Any public-facing, API-driven Java services or legacy Java Web Start environments should prioritize patching. As always, keeping your platforms up-to-date is your best defense.
Stay safe, patch smart, and audit your endpoints.
Exclusive Tip:
If you’re an enterprise security admin, turn on logging for any suspicious API activity and monitor for unexpected data modifications after upgrading. The window for exploitation is small, but with automation in today’s threat landscape, don’t leave your Java installations unpatched even for a week.
Timeline
Published on: 07/16/2024 23:15:16 UTC
Last modified on: 07/19/2024 14:15:05 UTC