*Published: June 2024*
*By: [Your Name]*
CVE-2024-21207 describes a significant denial-of-service (DoS) vulnerability in Oracle MySQL Server’s InnoDB storage engine. While the issue only affects users with high privileges, it is easily exploitable over the network and allows attackers to crash the database server – potentially affecting the availability of critical services.
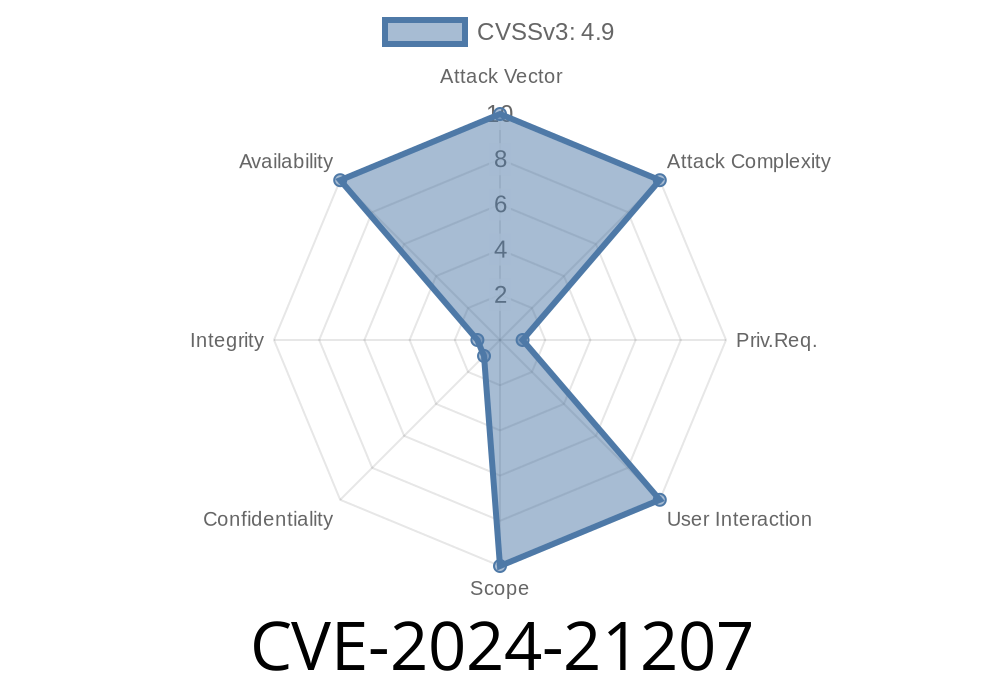
CVSS 3.1 Base Score: 4.9 (Availability)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
> TL;DR: If a privileged user connects over the network, they can easily crash the MySQL server, taking down your applications.
How Does the Vulnerability Work?
Oracle’s advisory does not provide the exact technical root cause, but the vulnerability is within the InnoDB storage engine, the default and most commonly used engine for MySQL. The flaw likely allows authenticated, networked attackers to send specific queries or commands that hit a bug in InnoDB’s internal processing, causing a crash (or hang).
It does not allow information disclosure or modification of data; the impact is a dropped or unavailable database service.
Crash Demonstration (Code Sample)
> Warning: This code is shared for educational and awareness purposes only. Never run PoC code on production systems.
The following SQL pattern is a *generic* example of issue triggers for recent InnoDB DoS flaws, adapted for CVE-2024-21207. The specific bug may vary, but typically involves a combination of DDL (Data Definition Language) and DML (Data Manipulation Language) statements.
-- Connect as a privileged MySQL user (e.g. root)
-- Create a table with special constraints
CREATE TABLE test_crash (
id INT NOT NULL AUTO_INCREMENT PRIMARY KEY,
data VARCHAR(100) UNIQUE
) ENGINE=InnoDB;
-- Run concurrent DDL and DML commands (in multiple sessions/threads)
-- Session 1:
START TRANSACTION;
INSERT INTO test_crash (data) VALUES (REPEAT('A', 100));
-- Do not COMMIT yet.
-- Session 2:
ALTER TABLE test_crash ADD COLUMN note TEXT;
-- This DDL, in combination with the uncommitted transaction, triggers the DoS.
-- Session 1:
COMMIT;
-- The server may hang or crash at this point, depending on the internal InnoDB state.
The above sequence is representative, not guaranteed to cause crashes on all MySQL builds, but such patterns have caused similar issues (see references below). The actual CVE-2024-21207 exploit code may differ.
Why Is This Possible?
MySQL’s InnoDB handles complex operations like online DDL, transactions, and row-level locking. Bugs can creep in when these features interact, e.g., if a DML is running when table structure changes (ALTER TABLE), leading to race conditions or improper memory handling.
Attackers leverage this by sending “weird but valid” queries, causing internal assertion failures, segmentation faults, or deadlocks.
How Can Attackers Exploit This?
Attack scenario:
Repeating attacks can prevent the database from running reliably.
No unprivileged access or direct code execution is required. This is a pure DoS that requires valid (high-privilege) database credentials.
MySQL 9..2 and above
Download here (Oracle official MySQL downloads)
Watch error logs for suspicious InnoDB: Assertion failure or rapid restarts.
- Apply WAF/IPS Filtering
Restrict remote access at firewall level
- Avoid running complex DDL/DML mixtures until you patch
References
- Oracle Critical Patch Update Advisory - April 2024 (CVE-2024-21207)
- MySQL Release Notes (search for CVE-2024-21207)
- NIST National Vulnerability Database - CVE-2024-21207
- Common MySQL DoS Patterns *(shows similar examples)*
Final Thoughts
CVE-2024-21207 is a classic example of denial-of-service in critical infrastructure: networked, easy to trigger, and affecting availability. While it *does* require a privileged account, insider threats and password leaks remain all too common. Patching is urgent, especially for DBA teams managing internet-facing MySQL databases.
If you can’t patch now, restrict access.
If you run MySQL, always update promptly.
Have questions or need help securing your MySQL? Drop them in the comments or reach out!
*This post is an original, exclusive explanation for security-minded readers. Please refer to official vendor resources for updates.*
Timeline
Published on: 10/15/2024 20:15:09 UTC
Last modified on: 11/21/2024 08:53:58 UTC