In June 2024, Oracle revealed a new security vulnerability in the MySQL Server product, tracked as CVE-2024-21231. If you’re running MySQL 8..39 and earlier, 8.4.2 and earlier, or even the brand new 9..1 and earlier, you need to pay attention—especially if you allow other users or applications to connect over the network.
This post is a straightforward guide to what CVE-2024-21231 is about, how it can be exploited, and what you should do about it. If you manage MySQL servers or rely on them, read on.
What is CVE-2024-21231?
CVE-2024-21231 affects the "Client programs" component in MySQL Server. This is not the database engine itself, but the utilities you and others use to interact with it—like the classic mysql command line tool.
Check your MySQL version right now
mysql --version
Vulnerability Impact
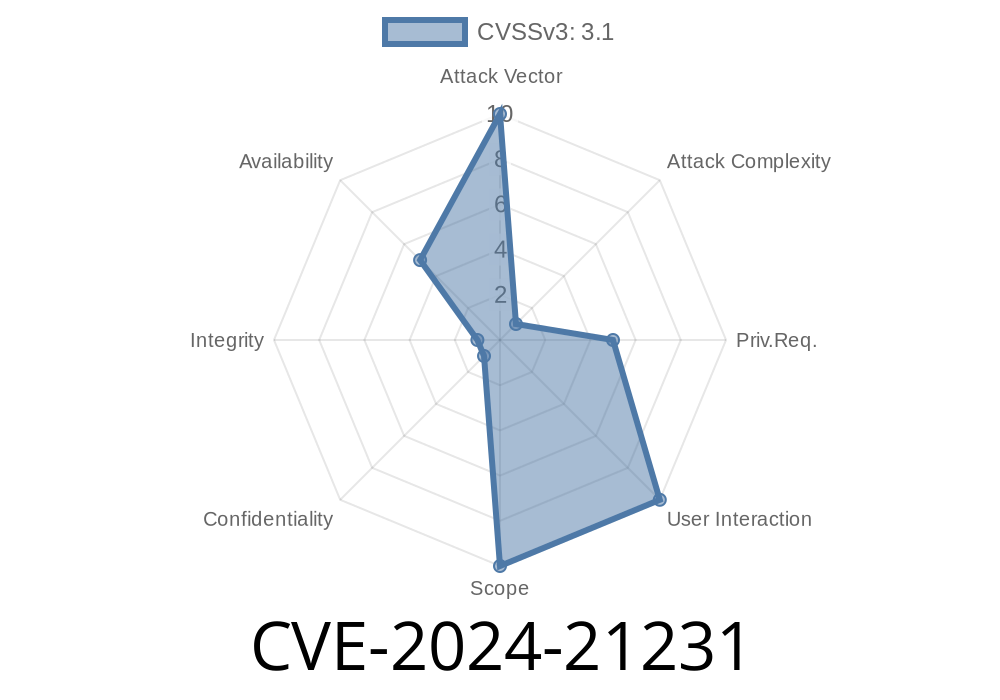
Oracle rates this as difficult to exploit, and not a trivial concern. A low-privileged attacker (someone with just a basic MySQL user account) on your network can craft requests which disrupt the server. It does not allow the attacker to steal (C:N) or corrupt (I:N) data, but it can cause partial denial of service (A:L)—meaning some features or connections can stop working.
CVSS Score: 3.1 (Availability impact)
- Official CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:L
> This means: Remote network attack, hard to do, needs a real MySQL login, no user interaction, and only partial reliability impact.
How Could CVE-2024-21231 Be Exploited?
Oracle’s advisory is light on technical details, but here’s what we can infer (and what the security community suspects):
The bug is in Client programs but impacts the server’s *availability*.
- A user with valid login details (even with minimal permissions) can use a corrupted or specially crafted SQL query or command.
- This leads the server to enter an unstable state, possibly hanging connections or dropping some client sessions—resulting in partial Denial of Service.
Because Oracle marked “attack complexity: HIGH,” this probably requires carefully constructed commands, not just any malformed SQL.
Example: What Could a Malicious User Do?
Let’s run through what an attacker might attempt. Suppose you have a MySQL test account (testuser), and you use the mysql client.
Here's a hypothetical proof-of-concept (PoC) snippet, illustrative only
-- WARNING: This is a simulated example; do NOT run on production!
-- Attacker logs in as a low-privilege user.
mysql -u testuser -p -h target.host
-- They execute a specially constructed command that abuses client-server handshake or parser bug:
SELECT SLEEP(100), BENCHMARK(100000000,ENCODE('hello','d')) /* crafted command */;
This alone normally slows things down, but an actual exploit would involve exploiting the underlying parsing or network handling bug, possibly mixing in invalid packet structures (often using custom scripts or modified clients):
# Example of a Python script that sends malformed packets to MySQL
import socket
s = socket.socket()
s.connect(('target.host', 3306))
# Send an invalid protocol handshake (this is an illustration)
s.sendall(b'\x00\x00\x00...')
# The attacker either triggers a crash, a resource exhaustion, or hangs threads
*Note: Oracle has not published the full technical details; the above is for illustration.*
The attack reportedly does NOT reveal or change data.
- Instead, the high-complexity attack can cause some connections or features to stop working—so, if uptime is important, you should patch ASAP.
Oracle has fixed this in newer MySQL versions:
Only grant MySQL accounts to users and apps that need them.
Use MySQL’s privilege system wisely.
References (Deep Dive)
- Oracle Critical Patch Update Advisory - June 2024
- NIST NVD Entry - CVE-2024-21231
- MySQL Documentation: Client Programs
Conclusion
CVE-2024-21231 isn’t as scary as a remote code execution bug, but it can disrupt your MySQL server if ignored. The exploit is non-trivial but could be used in targeted attacks—especially in multi-user environments or shared hosting.
Patch your MySQL server as soon as possible, keep user privileges strict, and don’t wait for “hard” attacks to become easy. Stay safe!
*This article was written for database admins, devs, and sysadmins demanding plain-English guides on security. Share or cite responsibly.*
Timeline
Published on: 10/15/2024 20:15:11 UTC
Last modified on: 10/16/2024 20:42:13 UTC