---
Windows has recently suffered from a critical vulnerability, CVE-2024-21357, related to its Pragmatic General Multicast (PGM) protocol. This bug allows an attacker to remotely execute code on a victim’s machine, potentially leading to complete system compromise. In this long read, we’ll cover the basics of PGM, dive into the technical details of the vulnerability, walk through some code snippets, and discuss exploit possibilities—with references for your further reading.
What is PGM?
Pragmatic General Multicast (PGM) is a network transport protocol designed for reliable multicast data delivery. It’s primarily used by specialized applications, such as Microsoft Message Queuing (MSMQ), that require efficient one-to-many communications. Unfortunately, features that make PGM powerful also increase its attack surface.
About CVE-2024-21357
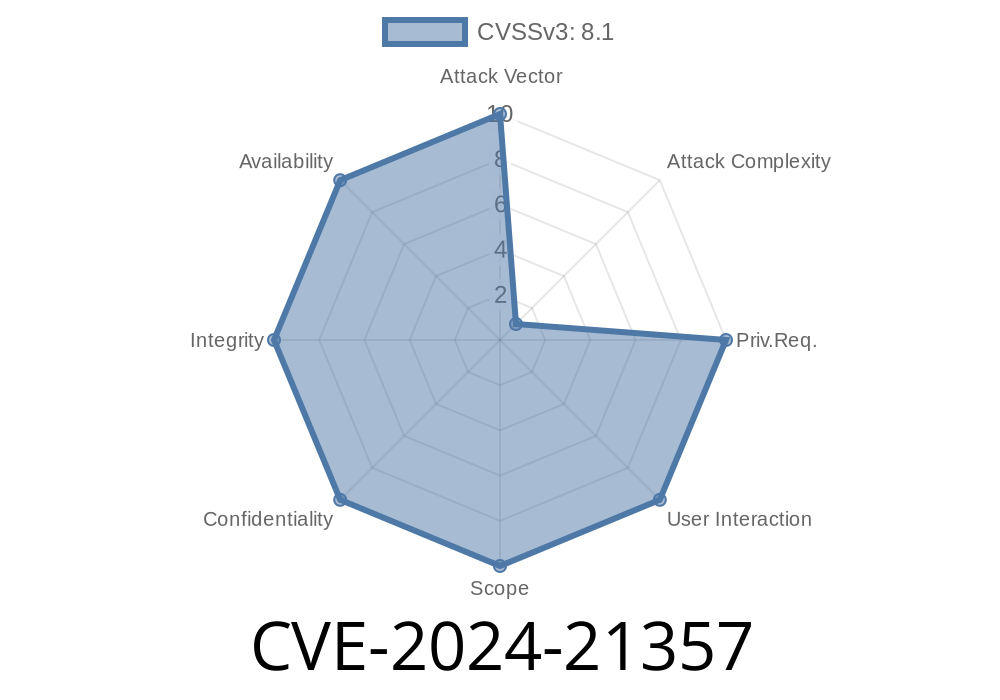
CVE-2024-21357 is a remote code execution (RCE) vulnerability discovered within the Windows implementation of PGM. According to Microsoft's advisory, this flaw allows unauthenticated attackers to send specially-crafted PGM packets to vulnerable systems, triggering errors that let them run code with SYSTEM privileges.
References
- Microsoft Security Advisory (CVE-2024-21357)
- NVD Entry
Technical Details
The issue arises from how Windows parses PGM options in incoming network packets. When an attacker sends a malformed PGM packet with specially-crafted option lengths or unexpected content, the Windows TCP/IP driver incorrectly handles the memory, leading to memory corruption or buffer overflow.
When exploited, this allows execution of arbitrary code at kernel level, effectively giving the attacker full control.
Reproducing the Vulnerability
Let’s walk through an example of how an attacker can interact with the PGM service. This educational snippet shows how to send a crafted PGM packet using Python’s raw sockets (requires admin privileges):
import socket
# Replace with target's IP address
target_ip = "192.168.1.100"
# Example: A malformed PGM option (not actual exploit, but an illustration)
# PGM uses Protocol Number 113
pgm_packet = b'\x00\x05\x00\x1c' + b'\xde\xad\xbe\xef' * 3 # Custom crafted header/payload
# Create a raw socket (requires admin)
s = socket.socket(socket.AF_INET, socket.SOCK_RAW, 113)
s.sendto(pgm_packet, (target_ip, ))
s.close()
> Warning: This code is for educational and testing purposes only. Never use these scripts against systems you do not own or have permission to test.
Exploit Development Overview
Exploit researchers reverse-engineered the patch and found that PGM’s parsing logic does not properly validate the length of an option field. Here’s a simplified description of what an exploit payload might try to do:
Craft a PGM packet with an oversized option length.
2. Send the packet to the target system’s PGM port (usually 48129/UDP as used by MSMQ).
Proof-of-Concept (High-Level Steps)
- Scan for hosts with MSMQ/PGM enabled: nmap -sU -p 48129 <network>
Apply the Microsoft patch immediately.
- Disable Windows features/services using PGM if not needed.
`
### Snort/IDS Rule Example (detecting basic PGM traffic)
alert udp any any -> any 48129 (msg:"PGM Packet Detected"; content:"|0005|"; depth:2; sid:2135701; rev:1;)
Aftermath
Once exploited, an attacker could create admin accounts, leave backdoors, or deploy ransomware. If your organization uses MSMQ or any service relying on PGM, patch immediately and review system logs for suspicious activity.
Further Reading and Resources
- Microsoft Security Guide on CVE-2024-21357
- CISA Guidance
- Wireshark - Analyzing PGM traffic
- Rapid7 Community - MSMQ and PGM Risks
Conclusion
CVE-2024-21357 is a very real threat for enterprise networks still relying on PGM-enabled components. Since exploitation is relatively straightforward and attackers only need to send network packets—no user interaction is required—organizations should act swiftly to protect their systems.
Timeline
Published on: 02/13/2024 18:15:52 UTC
Last modified on: 02/14/2024 19:15:09 UTC