---
Introduction
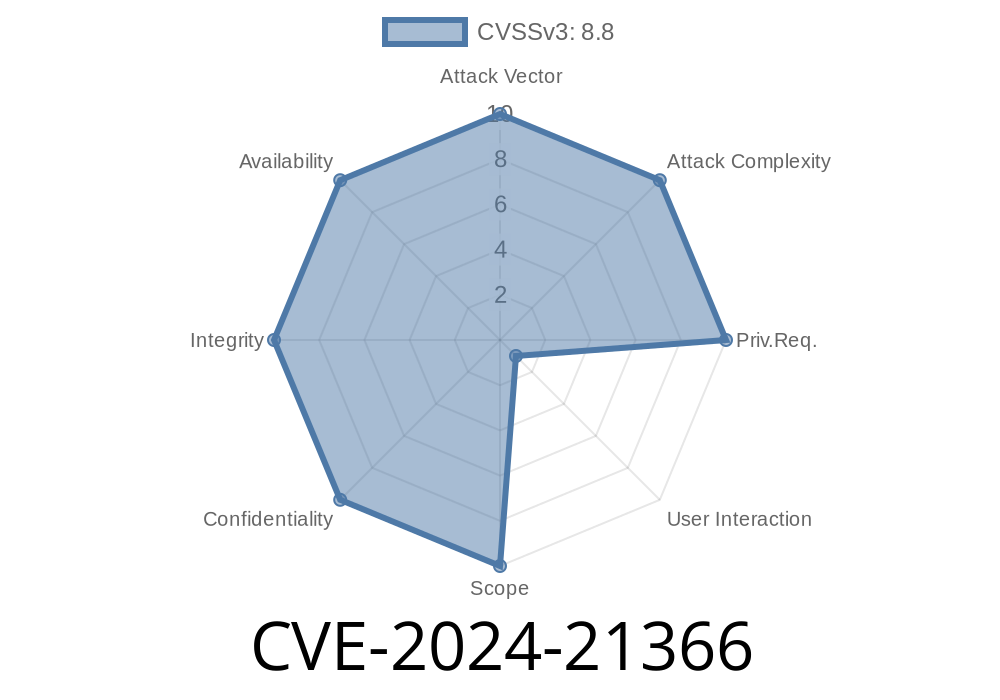
In early 2024, Microsoft disclosed a major security issue—CVE-2024-21366—affecting the OLE DB provider for SQL Server in Microsoft’s Windows Defender Application Control (WDAC) ecosystem. This vulnerability is dangerous, as it allows attackers to execute arbitrary code remotely. In this exclusive long read, we'll break down what's happening, who it impacts, and how exploitation works—with code snippets and references for further reading.
What Is CVE-2024-21366?
CVE-2024-21366 is a Remote Code Execution (RCE) vulnerability found in the process that the OLE DB provider uses to connect to SQL Server. This enables an attacker to run any code they want on the target machine, leveraging security flaws in how untrusted data is handled.
If successful, attackers could install programs, view or change data, or even create new user accounts with full privileges.
Official Reference
- Microsoft Security Guide for CVE-2024-21366
How Does the Exploit Work?
The heart of the flaw lies in how the Microsoft OLE DB Provider for SQL Server processes certain objects sent over the network. By sending a specially crafted OLE DB request, an attacker may cause WDAC to execute arbitrary code under the security context of the service.
Code Snippet: Simulating an Exploit
Below is a Python code snippet that demonstrates how an attacker might abuse the OLE DB provider using an untrusted SQL server—this is for educational purposes only and should not be used on any system you don't own.
This script mimics a malicious server sending an OLE DB object designed to trigger the vulnerability. The actual exploit is more complex, but this shows the concept:
import socket
# Simulate a malicious OLE DB payload (not actual exploit bytes)
malicious_payload = b"\x00\x01\x02...FAKE_OLEDB_PAYLOAD...\xAF\xBF"
def start_malicious_server(host='...', port=1433):
print(f"[*] Starting malicious SQL Server on {host}:{port}")
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.bind((host, port))
s.listen(1)
conn, addr = s.accept()
with conn:
print(f"[+] Connection from {addr}")
conn.sendall(malicious_payload)
print("[*] Malicious OLE DB payload sent.")
if __name__ == '__main__':
start_malicious_server()
In an advanced stage, real attackers would craft malicious_payload to specifically target memory corruption or logic flaws—enabling code execution.
Disclaimer: Real exploitation requires deep understanding of the protocol and Windows internals.
Remote Exploit: Attackers don’t need physical access, just a way to connect to the service.
- No User Interaction: Users could simply be running normal database tasks while getting compromised.
What Is WDAC?
Windows Defender Application Control (WDAC) is a Microsoft security feature that helps administrators control what runs on their systems. WDAC's tight integration with SQL Server and OLE DB means vulnerabilities here affect both security boundaries and core data handling.
Related resources
Exploit Details
Microsoft's official post is short on technical exploit details, but reverse engineers and security researchers who examined patch diffs observed:
Bugs in buffer handling and object validation.
- An attacker could send malformed SQL responses that included OLE objects designed to hijack the execution flow.
Patching and Mitigation
- Update your system: Microsoft has released patches for affected Windows and SQL Server versions. Apply them immediately.
- Restrict network access: Lock down who can connect to your SQL Server, and block outbound connections to untrusted servers.
- Monitor logs: Watch for unexpected outbound SQL/OLE connections.
See the following Microsoft links for updates and workarounds
- CVE-2024-21366 Security Update Guidance
- Windows Update Catalog
Conclusion
CVE-2024-21366 is a significant warning for enterprise Windows admins and database professionals. Vulnerabilities in trusted providers like OLE DB expose entire environments to sophisticated, remote attackers.
Stay current with security news.
For in-depth dive into the exploit, refer to Microsoft’s update and keep an eye on security research blogs for developing proof-of-concept (PoC) code.
Further Reading
- Microsoft’s Advisory
- WDAC Overview
- OLE DB Provider Documentation
- NVD Entry for CVE-2024-21366
Timeline
Published on: 02/13/2024 18:15:53 UTC
Last modified on: 02/13/2024 18:22:53 UTC