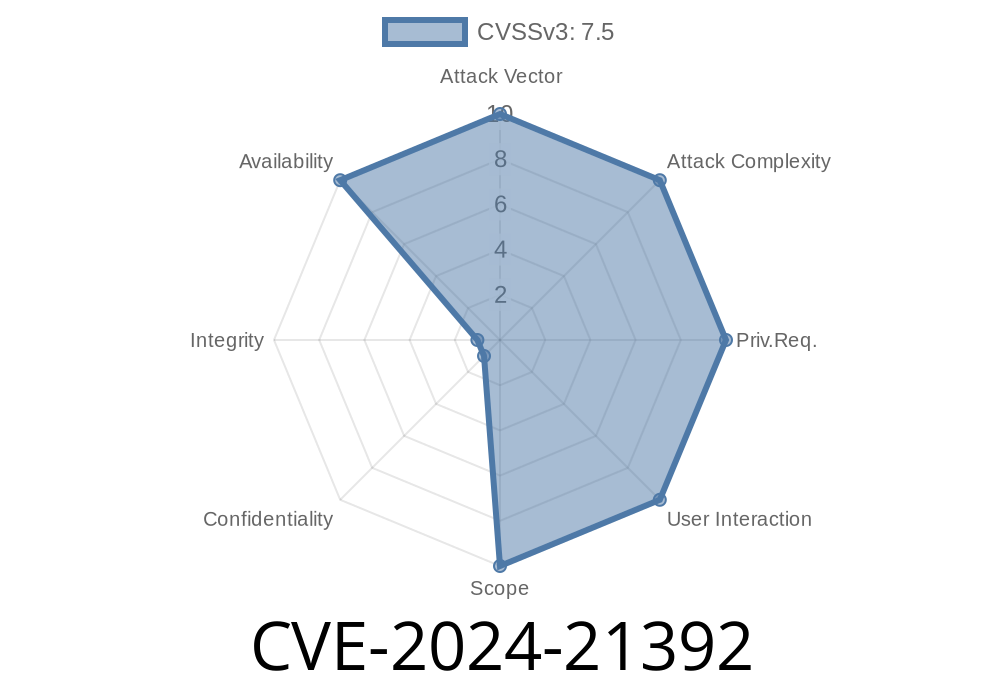
On February 13, 2024, Microsoft published an advisory for CVE-2024-21392, a Denial of Service (DoS) vulnerability affecting both .NET and Visual Studio products. For .NET developers and anyone working with Visual Studio, this vulnerability is important to understand—both for assessing risk and for mitigation. In this post, we'll cover what this vulnerability means, how it can be exploited, who’s at risk, and how you can protect yourself. You'll also find code samples and links to further info.
What is CVE-2024-21392?
CVE-2024-21392 is a vulnerability in .NET and Visual Studio where a remote malicious actor can cause denial-of-service by sending specially-crafted input to a vulnerable .NET application or manipulating project files in Visual Studio. This can force the application or IDE to crash, halt, or become unresponsive, disrupting both development and deployed environments.
Severity: Microsoft rates this as "Important."
Technical Details
Microsoft’s advisory is sparse, but analysis by security researchers and vendors (see references) suggest the vulnerability is rooted in improper parsing/loading of certain files. For example, a .NET application that processes untrusted user input or file uploads might encounter a crafted file that triggers an infinite loop, stack overflow, or memory exhaustion.
In Visual Studio, opening or building a malicious project or solution file can trigger the bug, potentially crashing the IDE and causing loss of unsaved work.
Exploit Example
Consider a simple .NET application that reads XML files. If an attacker uploads a purposely malformed XML document with recursive entity expansions (a "billion laughs" attack), it could cause high CPU/memory usage, leading to a denial-of-service.
Vulnerable Sample Code
using System;
using System.IO;
using System.Xml;
class Program
{
static void Main(string[] args)
{
// Simulate reading user-supplied XML
string xmlString = File.ReadAllText("user_input.xml");
XmlDocument doc = new XmlDocument();
doc.LoadXml(xmlString); // Vulnerable to crafted inputs
Console.WriteLine("Parsed XML successfully.");
}
}
Malicious Input (user_input.xml)
<?xml version="1."?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
]>
<lolz>&lol3;</lolz>
Result:
This input can exponentially expand in memory, leading to high resource consumption until the process or even the host machine becomes unresponsive.
Visual Studio Attack Vector
Malicious .csproj or .sln files could include malformed elements or metadata that, when loaded, crash the IDE without giving the user a chance to react.
Example (not actually weaponized, for demonstration only)
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<AssemblyName>$([System.IO.File]::ReadAllText('very_large_dummy_file'))</AssemblyName>
</PropertyGroup>
</Project>
If very_large_dummy_file is gigantic, Visual Studio could hang or crash as it attempts to process project metadata.
Apply the latest patches for both .NET and Visual Studio
- .NET February 2024 Security Updates
- Visual Studio Security Updates
When loading XML, use safe settings:
XmlReaderSettings settings = new XmlReaderSettings
{
DtdProcessing = DtdProcessing.Prohibit
};
using (XmlReader reader = XmlReader.Create("user_input.xml", settings))
{
XmlDocument doc = new XmlDocument();
doc.Load(reader);
}
References and Further Reading
1. Microsoft Security Update Guide – CVE-2024-21392
2. February 2024 .NET Updates
3. Visual Studio Security Updates
4. OWASP XXE Guide
Conclusion
CVE-2024-21392 shows that even trusted tools like .NET and Visual Studio can have denial-of-service vulnerabilities if file parsing or input validation aren’t handled with care. By applying Microsoft updates, validating inputs, and being cautious with files, you can greatly reduce your risk. Stay informed, stay secure, and keep building safely.
If you want more real-world examples or have questions about securing your .NET stack, feel free to reply or reach out!
Timeline
Published on: 03/12/2024 17:15:49 UTC
Last modified on: 03/12/2024 17:46:17 UTC