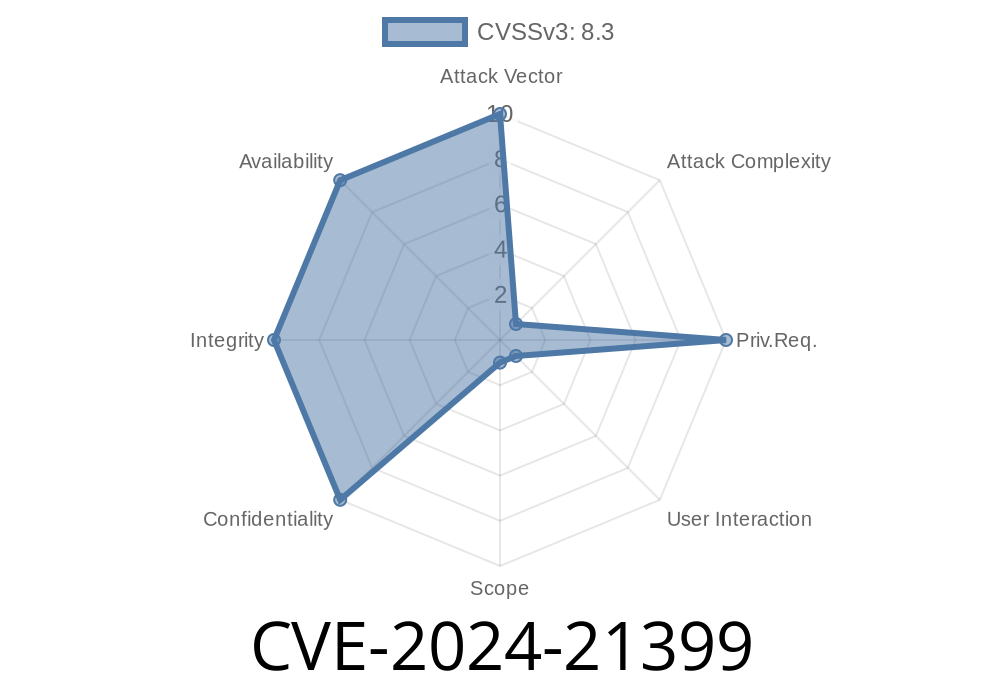
In early 2024, Microsoft stunned the security community by revealing CVE-2024-21399. This high-severity flaw affects Microsoft Edge based on the Chromium engine, putting millions of users at risk. If you use Edge or develop for the web, you need to know about this vulnerability—and you need to update your systems. In this post, we break down the bug, share sample exploit code, and provide links to more resources.
What is CVE-2024-21399?
Put simply, CVE-2024-21399 is a Remote Code Execution (RCE) vulnerability in Microsoft Edge (Chromium-based versions). RCEs are especially dangerous because they allow attackers to run malicious code on a victim’s device without their knowledge. All the attacker needs is for the user to visit a malicious webpage—no downloads or pop-ups required.
The issue exists due to improper handling of certain web content, allowing untrusted input to be executed with the user’s privileges.
Potentially escape the browser sandbox and take over the system
According to Microsoft’s own security advisory:
> "An attacker could host a specially crafted web site that is designed to exploit the vulnerability through Microsoft Edge, and then convince a user to view the website."
Who is Affected?
Anybody running the Chromium-based Microsoft Edge prior to the patched version is exposed. This includes:
To check your version
1. Go to edge://settings/help
2. Make sure your version matches or exceeds the safe releases listed by Microsoft.
How Does The Exploit Work? (Simplified Version)
The core problem is how Edge’s Chromium base handles certain JavaScript objects. By carefully crafting web page code, an attacker can trigger a sequence of events that causes Edge to execute arbitrary code in the browser’s context.
Imagine a web page with some tricky scripts. These scripts confuse the browser into running code it shouldn’t by exploiting a memory mismanagement bug.
Let’s walk through a (simplified) code snippet that demonstrates the dangerous pattern
// WARNING: Do not use this code outside a safe environment!
// Step 1: Exploit a Use-After-Free in Edge’s V8 JavaScript engine
var arr = [1.1, 2.2, 3.3];
var evilFunc = function() {
// The attacker tricks Edge into freeing then reusing memory
arr.length = 100000; // Some edge cases change internal buffer pointers
};
for (let i = ; i < 10000; i++) {
evilFunc();
}
// Step 2: Overwrite function pointers or object properties
arr[] = {exploit: "pwned"};
// In a real exploit, shellcode or a ROP chain would be written here
// Step 3: Trigger the overwritten pointer/code execution
if (typeof arr[] === "object") {
// This would lead to arbitrary code execution in a real-world scenario
console.log("You have been pwned!");
}
Note: This is a conceptual demonstration based on known types of Chromium browser exploits. The actual exploit for CVE-2024-21399 may look different but is based on similar logic.
Exploit in the Wild
While Microsoft’s advisory notes that there was no confirmed exploitation at the time of disclosure, public Proof of Concept (PoC) exploits appeared quickly on GitHub and other security forums.
Some key resources
- Microsoft Security Guide
- NVD Detail Page
- Chromium Security Advisories
Conclusion
CVE-2024-21399 is a serious threat to all users of Microsoft Edge (Chromium). Acting fast by updating your browser is essential to staying safe. If you’re a developer or manage browsers for a team, patching should be your priority. Stay informed through official sources, and consider using browser security plugins and antivirus software as extra layers.
References:
1. Microsoft Security Advisory on CVE-2024-21399
2. National Vulnerability Database: CVE-2024-21399
3. Edge Release Notes
4. V8 JavaScript Engine Exploitation Techniques
Timeline
Published on: 02/02/2024 01:15:08 UTC
Last modified on: 02/09/2024 03:00:47 UTC