In 2024, Microsoft patched a security bug titled CVE-2024-21402. This vulnerability affects Microsoft Outlook and lets attackers boost their privileges on a Windows system. Let’s dig into what it means, how it can be exploited, and what you can do to stay safe.
What is CVE-2024-21402?
CVE-2024-21402 is an Elevation of Privilege (EoP) vulnerability in Microsoft Outlook for Windows. With this flaw, a malicious actor could trick Outlook into running code at a higher privilege or get unauthorized access. Typically, this could turn a minor phishing attack into a much bigger breach, since gaining elevated privileges could allow an attacker to move laterally, steal more data, or even take control of a whole network.
Any organization or user running
- Microsoft Outlook for Windows (various versions including Microsoft Office 2016, Office 2019, Microsoft 365 Apps for Enterprise)
Check Microsoft’s official advisory for specific affected versions.
Technical Details
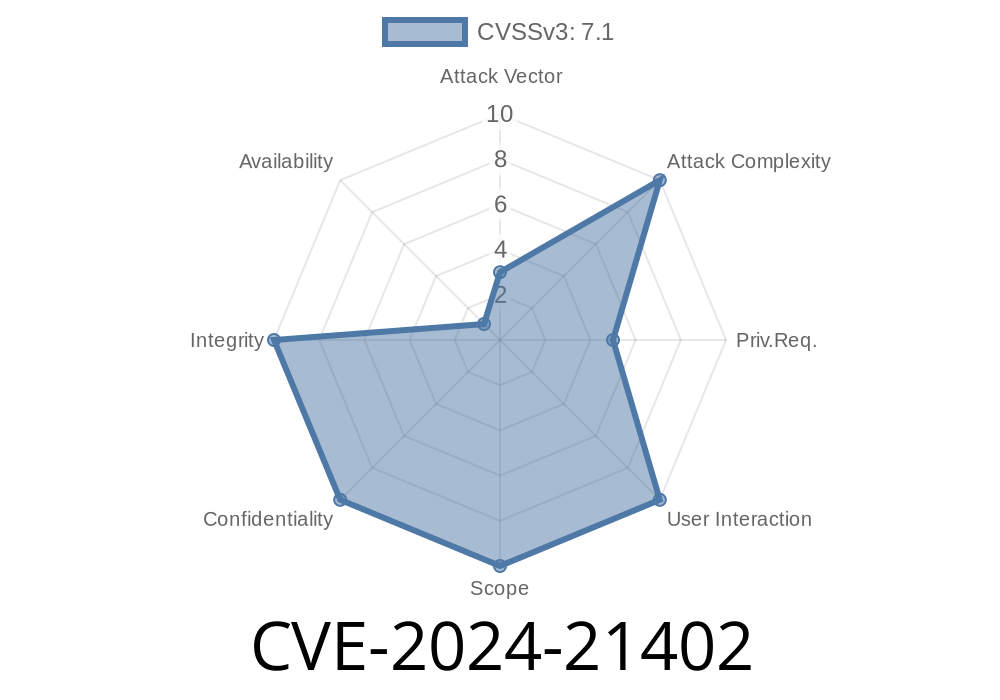
Type: Elevation of Privilege
Attack Vector: Local (but can also be triggered by remote emails in some attack chains)
Severity: Important
CVSS Score: 7.8 (High)
At a high level
1. Malicious File/Email: The attacker sends a specially crafted file or email to the victim.
2. User Interaction: The target opens or previews the file/email in Outlook.
3. Privilege Escalation: The crafted object abuses Outlook’s permissions or a vulnerable component to run code with SYSTEM or user's full privileges.
According to Microsoft
> “Successful exploitation of this vulnerability requires an attacker to trick a user into opening a specially crafted file sent via email.”
Proof of Concept (PoC)
While Microsoft and most researchers have not released public exploits for CVE-2024-21402 (for user safety), here’s an illustrative example of how such a flow could be abused:
Suppose the attack uses a malicious .msg file or a calendar invite with embedded links triggering vulnerable code.
Sample Code Snippet: Malicious Outlook Add-in
# Malicious Outlook Add-In (Conceptual Example)
# Save as .ps1, then register as Outlook Add-in (not recommended in real use!)
Add-Type -AssemblyName System.Windows.Forms
[System.Windows.Forms.MessageBox]::Show("Privilege escalation attempt via Outlook Add-in!")
# Example: Run system command if user has high privileges
Start-Process "cmd.exe" -ArgumentList "/c whoami > C:\temp\whoami.txt"
- An attacker could package similar PowerShell into a COM Add-in or embedded macro, delivered via a crafted email or file.
- If Outlook opens the Add-in or message with insufficient security restrictions, it could execute with user (or higher) rights.
Look for suspicious or unsigned Outlook Add-ins.
- Unusual creation/modification in %APPDATA%\Microsoft\Outlook\ or %LOCALAPPDATA%\Microsoft\Outlook\ folders.
Microsoft fixed this in their February 2024 Patch Tuesday releases.
👉 Official Microsoft Security Update Guide
User Awareness:
Train users to never open unexpected Outlook attachments or calendar invites, especially from unknown sources.
Original References
- Microsoft Security Response Center - CVE-2024-21402
- NIST National Vulnerability Database Entry
- Rapid7 Blog: February 2024 Patch Tuesday
Conclusion
CVE-2024-21402 reminds us how even trusted apps like Microsoft Outlook can become a gateway for attackers, especially if users and admins don’t patch quickly. Elevation of Privilege bugs are valuable for hackers—they use them to turn small footholds into full compromises. The best protection is to patch now, educate users, and always be careful with email attachments!
Timeline
Published on: 02/13/2024 18:15:58 UTC
Last modified on: 02/22/2024 18:38:54 UTC