---
Introduction
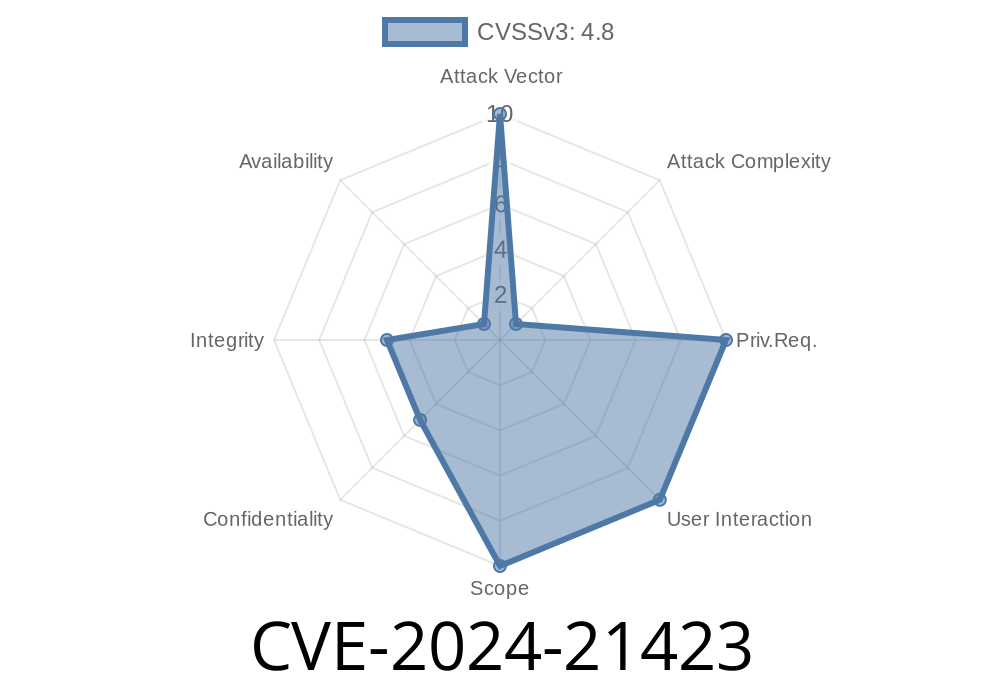
On February 13, 2024, Microsoft publicly disclosed CVE-2024-21423—a new information disclosure vulnerability affecting Microsoft Edge (Chromium-based). This type of vulnerability is particularly concerning because it could allow attackers to access sensitive information from your browsing sessions. In this post, we'll dive into what CVE-2024-21423 is, how it can be exploited, and what you can do to stay safe.
What is CVE-2024-21423?
CVE-2024-21423 is classified as an information disclosure vulnerability in Microsoft Edge, specifically those versions built on the Chromium engine (which is what powers Google Chrome as well). This flaw allows a remote attacker to access sensitive user information simply by getting the user to visit a malicious website.
The root cause of this vulnerability lies in how Microsoft Edge handles certain web content from untrusted sources. If exploited, it could allow an attacker to read information from memory that should be inaccessible, such as cookies, browsing history, or even data from other websites the user has open.
Technical Details and Exploit Scenario
While Microsoft did not release full technical details (common for actively exploited or easily weaponized bugs), security researchers and Microsoft's MSRC note describe it as a memory corruption issue due to "improper object handling" in certain browser contexts.
Trick the user into visiting that website (through phishing emails, ads, or social media).
3. The website executes carefully crafted JavaScript or HTML that abuses the flaw to bypass security boundaries in the browser.
4. The attacker could then read sensitive data from your session—including, potentially, information from other browser tabs or logged-in services.
Example Exploit Snippet
While there's no official proof-of-concept (PoC) exploit released (for obvious reasons), a simplified and hypothetical JavaScript snippet could look similar to this:
// Hypothetical Example: Edge CVE-2024-21423 Info Disclosure
// WARNING: This is a representation and not an actual exploit.
// Suppose the flaw is due to improper message event handling
window.addEventListener("message", (event) => {
// The vulnerability allows this code to read cross-origin data
if(event.origin !== "https://trusted-site.com";) {
// Normally, data here would be blocked, but due to the flaw:
console.log("Leaked Data:", event.data); // Sensitive info may be exposed!
}
});
// The attacker site sends a crafted message, potentially leaking data
window.postMessage("send-me-your-cookies", "*");
*Again, the actual vulnerability took advantage of deeper browser internals, but this conveys the general idea—code running in one context could access information it's not supposed to.*
Microsoft Edge is shipped with all Windows 10 and Windows 11 systems by default.
- Chromium-based browsers, with shared code, mean similar vulnerabilities can quickly become widespread.
- While this flaw by itself "only" leaks data, it can be highly valuable to attackers for further social engineering, credential theft, or as part of larger attacks.
References
- Microsoft Security Update Guide: CVE-2024-21423
- Edge Release Notes
- NVD - CVE-2024-21423
Conclusion
CVE-2024-21423 highlights the ongoing importance of keeping browsers up-to-date. Given how integrated Edge is into modern Windows, ignoring this patch could allow criminals to peek into your online life. The best defense is regular patching, safe browsing habits, and keeping yourself informed about new vulnerabilities as they emerge.
Timeline
Published on: 02/23/2024 22:15:54 UTC
Last modified on: 02/26/2024 13:42:22 UTC