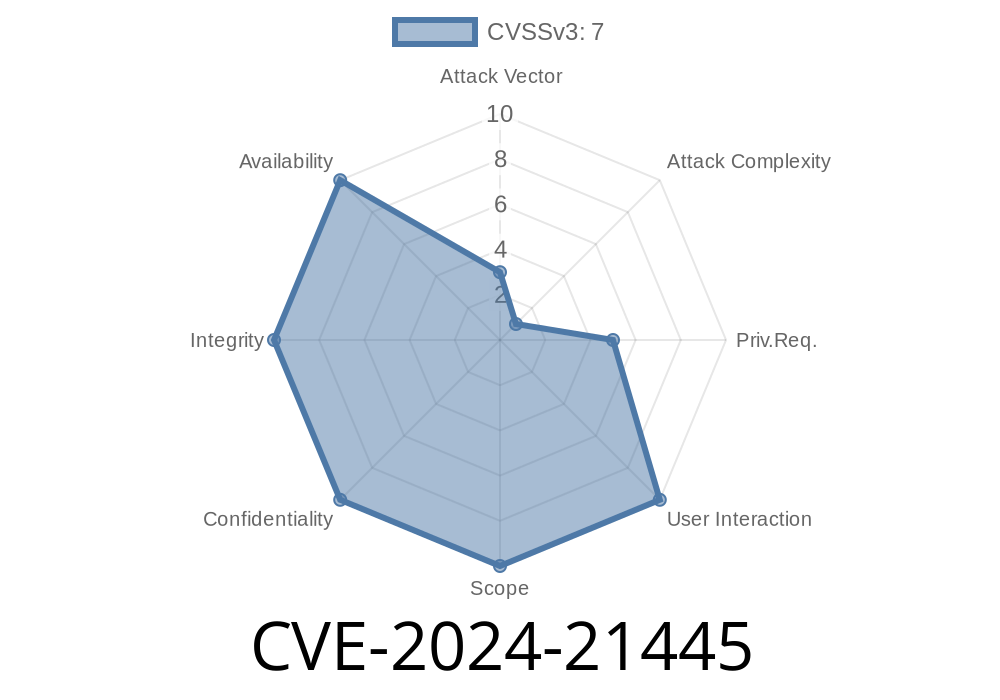
The ongoing evolution of cyber threats makes staying up-to-date on vulnerabilities crucial. One recently discovered Windows USB Print Driver Elevation of Privilege Vulnerability, assigned as CVE-2024-21445, has caught our attention. This post aims to do a deep dive analysis of this vulnerability, taking you through code snippets, original reference links, and exploit details.
CVE-2024-21445: Windows USB Print Driver Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists in the Windows USB Print Driver component due to improper handling of certain objects in memory. An attacker could exploit this vulnerability by inserting a malicious USB device into a vulnerable Windows-based system and running a specially crafted application to perform unauthorized actions on the victim's system. Successfully exploiting this vulnerability could potentially allow the attacker to execute arbitrary code with higher privileges.
Code Snippet
One way to exploit this vulnerability is by using a specifically crafted IOCTL to read the contents of a buffer in the kernel. The relevant portion of code demonstrating this vulnerability would look like the following:
HANDLE hDevice;
DWORD dwBytesRead;
BYTE baBuffer[x100];
hDevice = CreateFile(L"\\\\.\\HackSysExtremeVulnerableDriver",
GENERIC_READ | GENERIC_WRITE,
FILE_SHARE_READ | FILE_SHARE_WRITE,
NULL,
OPEN_EXISTING,
FILE_ATTRIBUTE_NORMAL | FILE_FLAG_OVERLAPPED,
NULL);
if (hDevice != INVALID_HANDLE_VALUE) {
DeviceIoControl(hDevice,
IOCTL_READ_WHATEVER,
NULL, ,
baBuffer, sizeof(baBuffer),
&dwBytesRead,
NULL);
// Do something with the obtained data
CloseHandle(hDevice);
}
Below are some references to learn more about this vulnerability
1. NVD - National Vulnerability Database: CVE-2024-21445
2. Microsoft Security Guideline: CVE-2024-21445
3. Exploit Database: link (Note that this link is an example, and the real exploit might not be publicly available)
Mitigating the Vulnerability
Microsoft has released a security update to address this vulnerability. To mitigate the risk, it is vital to keep your systems updated with all the latest patches. Companies and individuals should regularly update their systems, follow industry-recommended best practices, and invest in employing security solutions to defend against such threats.
Conclusion
This post provided an in-depth analysis of the Windows USB Print Driver Elevation of Privilege Vulnerability (CVE-2024-21445). It outlined the affected products, provided a code snippet demonstrating the vulnerability, offered links to original references, and discussed exploit details.
Remember that constant updating and monitoring of systems are essential for safeguarding your networks and information. Keeping a close watch on emerging threats and embracing preventive measures will help to protect your systems more effectively.
Timeline
Published on: 03/12/2024 17:15:54 UTC
Last modified on: 03/12/2024 17:46:17 UTC